Which is most secure radius pki – Which RADIUS PKI configuration is most secure? This question is at the heart of network security, as it involves the intricate interplay of authentication, authorization, and encryption. RADIUS, or Remote Authentication Dial-In User Service, is a network protocol used for centralized authentication and authorization, while PKI, or Public Key Infrastructure, provides a robust framework for managing digital certificates and keys.
By integrating RADIUS and PKI, organizations can significantly enhance the security of their networks, ensuring that only authorized users and devices have access to sensitive resources.
The security of a RADIUS PKI configuration hinges on a variety of factors, including the choice of authentication methods, cryptographic algorithms, key lengths, and overall system design. Understanding these factors and implementing best practices is crucial for achieving a highly secure and resilient network environment. This article delves into the intricacies of RADIUS and PKI, exploring different configurations and their security implications, and ultimately providing insights into which RADIUS PKI configuration is most secure.
RADIUS and PKI
In the realm of network security, RADIUS and PKI play crucial roles in establishing and maintaining robust authentication and authorization mechanisms. Understanding the fundamental concepts of each and their integration benefits is essential for safeguarding sensitive data and ensuring secure access to network resources.
RADIUS Authentication
RADIUS, which stands for Remote Authentication Dial-In User Service, is a network protocol used for centralized authentication, authorization, and accounting (AAA) services. It enables network access servers (NAS), such as routers and switches, to authenticate users and devices against a central RADIUS server. The process of RADIUS authentication involves the following steps:* Authentication Request: When a user attempts to access a network resource, the NAS sends an authentication request to the RADIUS server.
Authentication Response
The RADIUS server verifies the user’s credentials against its database and sends an authentication response to the NAS.
Access Grant or Denial
Based on the authentication response, the NAS grants or denies access to the network resource.
Public Key Infrastructure (PKI), Which is most secure radius pki
Public Key Infrastructure (PKI) is a system that uses cryptography to secure communication and authenticate identities within a network. It relies on the concept of asymmetric cryptography, which employs a pair of keys: a public key and a private key.* Public Key: This key is freely distributed and can be used to encrypt data or verify digital signatures.
Private Key
This key is kept secret and is used to decrypt data encrypted with the corresponding public key or sign digital documents.PKI provides the following functionalities:* Digital Certificates: PKI uses digital certificates to bind a public key to a specific entity, such as a user or device.
Certificate Authority (CA)
A trusted entity that issues and manages digital certificates.
Certificate Revocation List (CRL)
A list of revoked certificates that are no longer valid.
Digital Signatures
PKI uses digital signatures to verify the authenticity and integrity of digital documents.
Benefits of Integrating RADIUS and PKI
Integrating RADIUS and PKI offers numerous benefits for enhancing network security:* Stronger Authentication: PKI-based certificates provide a more robust authentication mechanism than traditional password-based authentication.
Improved Security
PKI encrypts communication between the NAS and the RADIUS server, protecting sensitive information from unauthorized access.
Centralized Key Management
PKI allows for centralized management of digital certificates, simplifying key distribution and revocation processes.
Enhanced Auditability
PKI provides a detailed audit trail of all authentication and authorization events, facilitating security investigations.
RADIUS Security Implementations
RADIUS, or Remote Authentication Dial-In User Service, is a network protocol that provides centralized authentication, authorization, and accounting (AAA) for users connecting to a network. While RADIUS itself is a powerful protocol, its security depends on the underlying authentication methods employed. Different RADIUS security implementations offer varying levels of protection, each with its strengths and weaknesses.
RADIUS Authentication Methods
The choice of authentication method within RADIUS significantly impacts the security of the network. Here’s a breakdown of common RADIUS authentication methods:
- Password Authentication Protocol (PAP): PAP transmits user credentials, including the username and password, in plain text. This makes it highly vulnerable to eavesdropping and interception, rendering it unsuitable for sensitive environments.
- Challenge Handshake Authentication Protocol (CHAP): CHAP provides a more secure alternative to PAP by using a challenge-response mechanism. The RADIUS server sends a random challenge to the client, which then calculates a response based on its shared secret and the challenge. This response is sent back to the server, which verifies its authenticity. While CHAP is more secure than PAP, it is still susceptible to brute-force attacks if the shared secret is weak or compromised.
- Extensible Authentication Protocol (EAP): EAP is a flexible framework that supports various authentication methods, including TLS, TTLS, PEAP, and LEAP. EAP allows for more sophisticated authentication techniques, such as digital certificates and mutual authentication, providing a higher level of security. However, EAP implementations can be complex to configure and manage, requiring expertise in network security.
PKI-Based RADIUS Authentication
PKI-based RADIUS authentication leverages digital certificates to secure the communication between RADIUS clients and servers. It provides a robust and secure mechanism for user authentication and authorization, enhancing the overall security posture of network infrastructure.
Certificate Issuance, Distribution, and Revocation
The process of certificate issuance, distribution, and revocation is crucial in PKI-based RADIUS authentication. This process ensures the integrity and trustworthiness of certificates used for authentication.
- Certificate Issuance: A Certificate Authority (CA) is responsible for issuing digital certificates to RADIUS clients and servers. The CA verifies the identity of the applicant and issues a certificate containing information about the entity, including its public key.
- Certificate Distribution: Once issued, certificates are distributed to the respective clients and servers. This can be done through secure channels, such as email or dedicated certificate repositories.
- Certificate Revocation: In case of compromise or expiration, certificates need to be revoked. The CA maintains a Certificate Revocation List (CRL) that contains information about revoked certificates. RADIUS clients and servers regularly check the CRL to ensure the validity of certificates.
Advantages of PKI for RADIUS Authentication
PKI offers several advantages for RADIUS authentication, contributing to a more secure and reliable network environment.
- Strong Authentication: PKI-based RADIUS authentication relies on digital certificates, which provide a strong and verifiable method of authentication.
- Mutual Authentication: PKI enables mutual authentication, where both the client and server verify each other’s identities, preventing unauthorized access and man-in-the-middle attacks.
- Non-Repudiation: Digital signatures associated with certificates provide non-repudiation, ensuring that both the client and server cannot deny their actions.
- Enhanced Security: PKI-based RADIUS authentication strengthens security by encrypting communication between clients and servers, protecting sensitive information from eavesdropping and tampering.
- Scalability and Flexibility: PKI is scalable and flexible, allowing for the authentication of a large number of users and devices across various network environments.
Secure RADIUS PKI Configurations
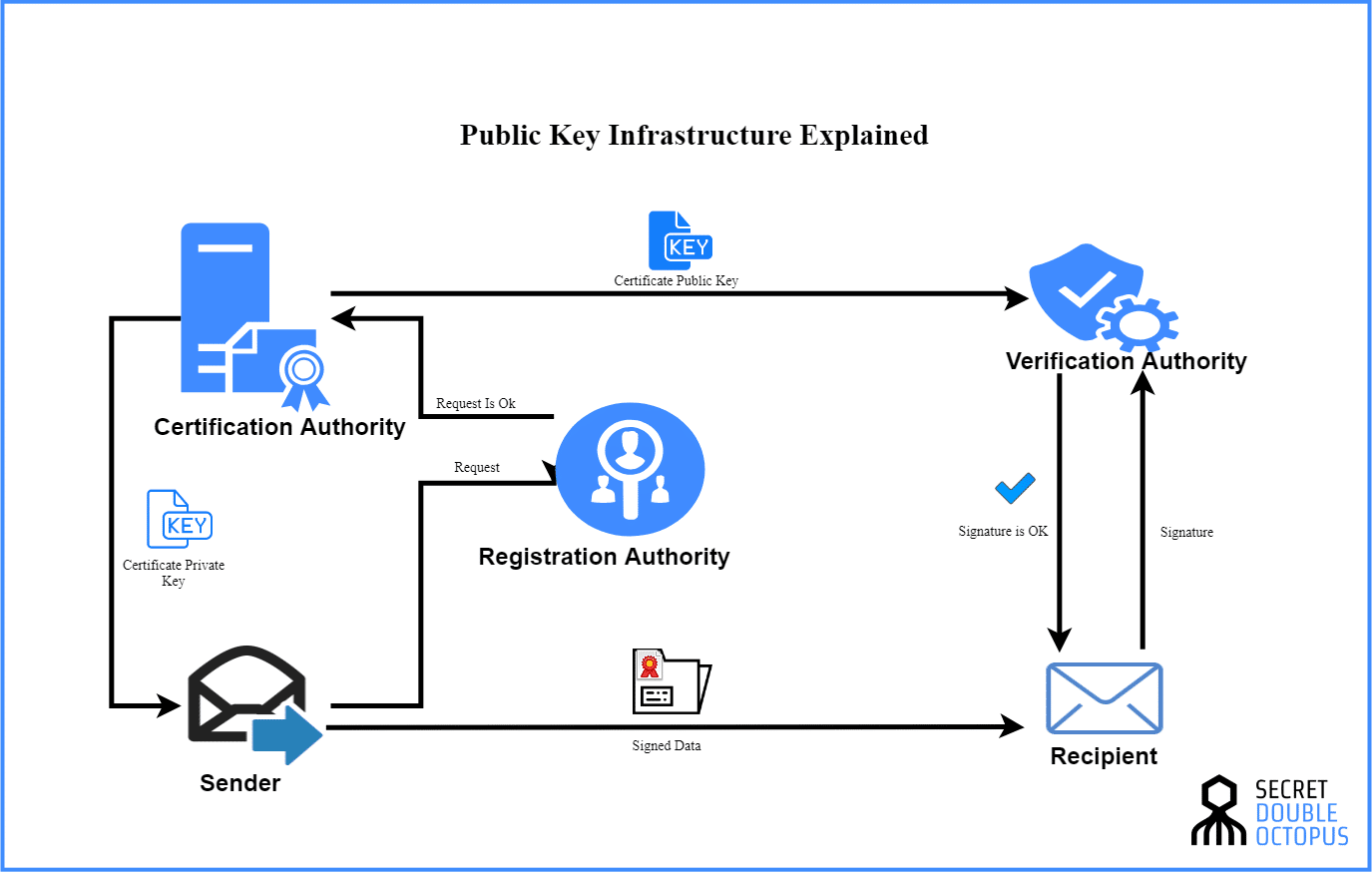
Implementing a secure RADIUS PKI configuration is crucial for safeguarding your network infrastructure and protecting sensitive user data. By integrating Public Key Infrastructure (PKI) with RADIUS authentication, you can significantly enhance security by establishing trust and verifying identities through digital certificates.
Choosing Appropriate Cryptographic Algorithms and Key Lengths
Selecting strong cryptographic algorithms and appropriate key lengths is paramount for ensuring robust encryption and digital signature capabilities. This section delves into best practices for choosing cryptographic algorithms and key lengths, providing guidance for a secure RADIUS PKI configuration.
- Symmetric Key Algorithms: For data encryption, consider using AES (Advanced Encryption Standard) with a key length of at least 128 bits. AES-256 offers even stronger protection but may incur a slight performance penalty.
- Asymmetric Key Algorithms: For digital signatures and key exchange, RSA (Rivest-Shamir-Adleman) or ECC (Elliptic Curve Cryptography) are widely used. RSA with key lengths of 2048 bits or higher is generally considered secure, while ECC with a 256-bit curve provides comparable security with smaller key sizes.
- Hashing Algorithms: SHA-256 or SHA-384 are recommended for generating secure hash values for digital signatures and message integrity verification.
Designing a Secure RADIUS PKI Configuration
A well-designed RADIUS PKI configuration minimizes vulnerabilities and ensures a robust authentication and authorization system. This section Artikels key considerations for designing a secure RADIUS PKI configuration, focusing on best practices and security principles.
- Certificate Authority (CA): Choose a reputable and trusted CA to issue digital certificates for RADIUS servers, clients, and users. A CA’s role is to validate identities and issue certificates, ensuring trust in the system.
- Certificate Management: Implement a robust certificate management system to track certificate validity, renewal, and revocation. This ensures that only valid certificates are used for authentication and authorization.
- Secure Communication: Encrypt RADIUS communication between servers and clients using TLS/SSL (Transport Layer Security/Secure Sockets Layer) to prevent eavesdropping and man-in-the-middle attacks. TLS/SSL encrypts data exchanged between RADIUS servers and clients, ensuring confidentiality and integrity.
- Access Control: Implement strict access control policies to limit access to RADIUS servers and PKI infrastructure. This includes restricting access to authorized personnel and enforcing strong authentication mechanisms for accessing sensitive components.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in the RADIUS PKI configuration. This includes assessing the security of certificates, encryption algorithms, and access control mechanisms.
Security Considerations
While RADIUS and PKI integration enhances security, it’s crucial to acknowledge potential vulnerabilities and implement mitigation strategies to ensure robust protection. This section delves into common security risks, attack vectors, and best practices for safeguarding your RADIUS and PKI infrastructure.
Vulnerabilities and Attack Vectors
RADIUS and PKI, despite their inherent security features, can be susceptible to various attacks. Understanding these vulnerabilities is essential for implementing effective countermeasures.
- Man-in-the-Middle (MitM) Attacks: An attacker intercepts communication between the RADIUS server and the client, potentially gaining access to sensitive data, such as usernames, passwords, and certificates.
- RADIUS Server Compromise: A compromised RADIUS server could grant unauthorized access to network resources or expose sensitive data.
- PKI Key Compromise: Compromised private keys used for certificate signing can lead to unauthorized access and data breaches.
- Weak Authentication Mechanisms: Using weak passwords or insecure authentication protocols can create vulnerabilities for attackers to exploit.
- Misconfigured RADIUS Servers: Incorrectly configured RADIUS servers, including weak access controls or improper encryption settings, can leave the system open to attacks.
Mitigation Strategies
To address these vulnerabilities, it’s essential to implement robust security measures:
- Secure Communication Channels: Use strong encryption protocols like TLS/SSL to protect RADIUS communication between the server and clients.
- Secure RADIUS Server: Deploy the RADIUS server in a secure environment with strong access controls and regular security updates.
- Secure Key Management: Use secure key management practices to protect private keys used for certificate signing. Implement hardware security modules (HSMs) for enhanced key protection.
- Strong Authentication: Enforce strong password policies, including complexity requirements and regular password changes. Consider multi-factor authentication (MFA) for increased security.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities.
- Security Monitoring: Implement robust security monitoring tools to detect suspicious activity and potential attacks.
Best Practices
- Use Strong Encryption: Employ strong encryption protocols like TLS/SSL to secure all RADIUS communication.
- Implement Access Control Lists (ACLs): Restrict access to the RADIUS server based on user roles and network policies.
- Enable Certificate Revocation: Implement a certificate revocation mechanism to invalidate compromised certificates promptly.
- Use Secure RADIUS Protocols: Employ secure RADIUS protocols, such as EAP-TLS and EAP-TTLS, for authentication.
- Regularly Update Software: Keep RADIUS servers and other related software up-to-date with the latest security patches.
Implementation and Deployment: Which Is Most Secure Radius Pki
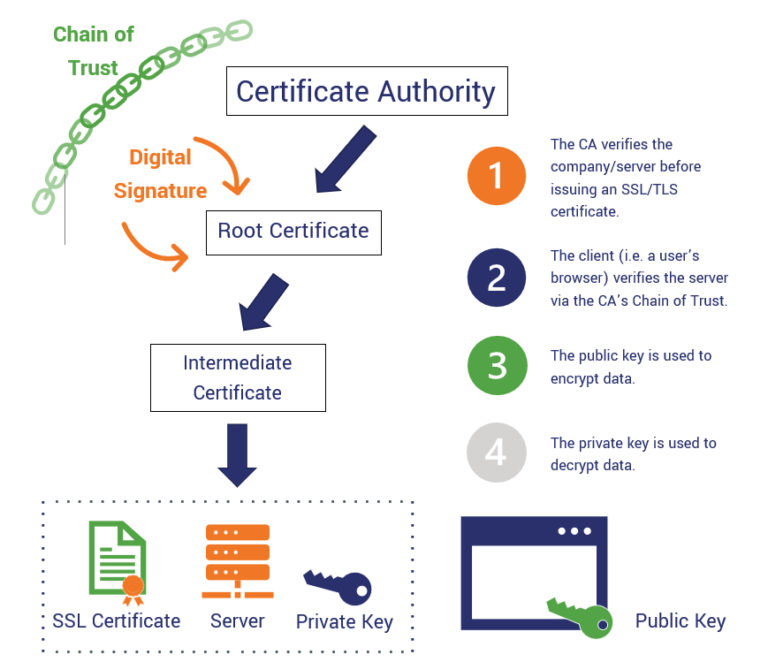
Implementing PKI-based RADIUS authentication involves setting up a robust infrastructure that securely manages digital certificates and enables authentication based on those certificates. This section provides a step-by-step guide, outlining the necessary hardware and software components, and offering a comprehensive checklist of essential configuration settings.
Hardware and Software Components
To implement PKI-based RADIUS authentication, you need to gather the following essential hardware and software components:
- RADIUS Server: A RADIUS server acts as the central authentication point, processing authentication requests from network devices and validating user credentials against the PKI infrastructure. Popular options include FreeRADIUS, Microsoft NPS, and Cisco ISE.
- PKI Infrastructure: A PKI infrastructure is crucial for managing digital certificates, including certificate generation, revocation, and distribution. Popular PKI solutions include Microsoft CA, OpenSSL, and Let’s Encrypt.
- Certificate Authority (CA): The CA is the trusted entity responsible for issuing and managing digital certificates. The CA’s role is to verify the identity of certificate applicants and ensure the authenticity and integrity of certificates.
- Registration Authority (RA): The RA acts as an intermediary between the CA and certificate applicants. It verifies user requests and submits them to the CA for processing.
- Network Devices: These devices, such as routers, switches, and wireless access points, support RADIUS authentication and can be configured to use PKI-based authentication.
- Client Devices: User devices, such as laptops, smartphones, and tablets, must be configured to support PKI-based authentication and have the necessary certificates installed.
Configuration Checklist
- Configure the RADIUS Server:
- Install and configure the RADIUS server software, ensuring it supports PKI-based authentication.
- Define the RADIUS server’s network settings, including its IP address, subnet mask, and default gateway.
- Configure the RADIUS server to use the PKI infrastructure for certificate validation.
- Create RADIUS user accounts and configure their authentication attributes, including certificate-based authentication settings.
- Configure the PKI Infrastructure:
- Install and configure the PKI infrastructure software, including the CA and RA.
- Define the PKI infrastructure’s security policies, including certificate validity periods, revocation procedures, and encryption algorithms.
- Create and manage digital certificates for users, network devices, and the RADIUS server.
- Configure the RADIUS server to trust the CA’s certificates and use them for certificate validation.
- Configure Network Devices:
- Configure network devices to support RADIUS authentication and use PKI-based authentication.
- Define the RADIUS server’s IP address and shared secret (if applicable) on each network device.
- Install the necessary certificates on network devices for secure communication with the RADIUS server.
- Configure Client Devices:
- Install the necessary certificates on client devices for secure communication with the RADIUS server.
- Configure client devices to use PKI-based authentication and specify the RADIUS server’s address.
Monitoring and Management
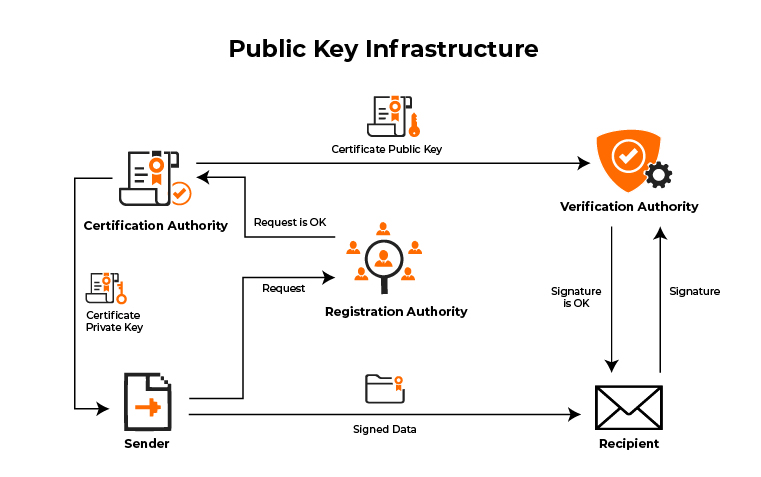
Ensuring the security of RADIUS and PKI systems is an ongoing process that involves vigilant monitoring and proactive management. Effective monitoring helps identify potential security incidents, while robust management practices ensure the integrity and security of certificates and keys.
Monitoring for Security Incidents
Monitoring RADIUS and PKI systems for security incidents is crucial to detect and respond to potential threats promptly.
- Log Analysis: Regularly review RADIUS and PKI server logs for suspicious activity, including failed authentication attempts, unauthorized access, and unusual certificate requests.
- Network Monitoring: Monitor network traffic for anomalies, such as unexpected spikes in RADIUS communication or attempts to access PKI servers from unusual locations.
- Security Information and Event Management (SIEM): Implement a SIEM solution to centralize security logs from various sources, including RADIUS and PKI systems, for comprehensive threat detection and analysis.
- Intrusion Detection Systems (IDS): Deploy IDS to detect and alert on potential attacks targeting RADIUS and PKI infrastructure.
Identifying and Responding to Suspicious Activity
Once suspicious activity is detected, it is essential to investigate and respond appropriately.
- Alerting: Configure alerts for critical events, such as failed authentication attempts, unauthorized certificate requests, or unusual network activity.
- Investigation: Investigate suspicious activity to determine the root cause, the extent of the compromise, and the potential impact.
- Containment: Isolate affected systems or network segments to prevent further damage and limit the spread of the incident.
- Remediation: Address the underlying vulnerabilities, restore compromised systems, and implement necessary security measures to prevent recurrence.
Certificate and Key Management
Maintaining the security of certificates and keys is critical for the overall security of RADIUS and PKI systems.
- Certificate Authority (CA) Management: Securely manage the CA infrastructure, including the private key and certificates, to prevent unauthorized access and compromise.
- Certificate Revocation: Establish a process for revoking compromised certificates promptly to prevent their use.
- Key Rotation: Regularly rotate keys to minimize the impact of key compromise.
- Backup and Recovery: Maintain backups of certificates and keys in a secure location for recovery in case of loss or damage.
- Certificate Expiration Monitoring: Monitor certificate expiration dates and renew certificates before they expire to avoid service disruptions.
Real-World Applications
PKI-based RADIUS authentication is a powerful security mechanism that has widespread applications in various industries. This approach offers robust security, scalability, and flexibility, making it ideal for securing access to sensitive networks and resources.
Enterprise Networks
PKI-based RADIUS authentication is essential for securing enterprise networks. It ensures that only authorized users can access critical resources and data.
- User Authentication: PKI certificates issued to employees provide a secure and reliable way to authenticate users to the network. These certificates can be stored on smart cards, hardware tokens, or software-based digital wallets.
- Network Access Control (NAC): PKI can be integrated with NAC solutions to enforce access policies based on user identity and device health. This helps prevent unauthorized access and mitigate security risks.
- Secure Network Segmentation: PKI enables the creation of secure network segments, restricting access to specific resources based on user roles and permissions. This enhances security by isolating sensitive data and critical systems.
Wi-Fi Deployments
PKI plays a crucial role in securing Wi-Fi networks, especially in public and enterprise settings.
- Secure Wireless Authentication: PKI certificates enable secure authentication of Wi-Fi users, preventing unauthorized access and data breaches.
- WPA2/3 Enterprise Security: PKI is the foundation for WPA2/3 Enterprise security, which uses 802.1x authentication to provide robust protection for wireless networks.
- Guest Access Management: PKI can be used to provide secure and controlled guest access to Wi-Fi networks, allowing organizations to manage guest access while ensuring network security.
VPNs
PKI is widely used in VPN deployments to provide secure and authenticated access to remote users.
- Secure Tunneling: PKI certificates are used to establish secure tunnels between VPN clients and servers, encrypting all data transmitted over the network.
- Mutual Authentication: PKI enables mutual authentication between VPN clients and servers, ensuring that both parties are who they claim to be.
- Certificate-Based Access Control: PKI can be used to implement certificate-based access control, restricting VPN access based on user roles and permissions.
Ultimately, the most secure RADIUS PKI configuration is the one that best addresses the specific needs and security requirements of an organization. By carefully considering the factors Artikeld in this article, network administrators can choose the appropriate authentication methods, cryptographic algorithms, and key lengths to achieve a robust and secure network environment. The implementation of best practices, regular monitoring, and proactive security measures are essential for mitigating potential vulnerabilities and ensuring the long-term security of RADIUS and PKI systems.
Key Questions Answered
What are the key differences between PAP, CHAP, and EAP authentication methods?
PAP (Password Authentication Protocol) is a simple authentication method that transmits passwords in plain text, making it highly insecure. CHAP (Challenge Handshake Authentication Protocol) is more secure, as it uses a challenge-response mechanism to verify passwords. EAP (Extensible Authentication Protocol) is a flexible and extensible framework that supports various authentication methods, including TLS, TTLS, and PEAP.
What are the main advantages of using PKI for RADIUS authentication?
PKI provides several advantages for RADIUS authentication, including:
- Stronger authentication: PKI certificates provide a higher level of assurance than traditional passwords.
- Centralized certificate management: PKI allows for the centralized issuance, distribution, and revocation of certificates, simplifying key management.
- Enhanced security: PKI provides a framework for secure communication, including data encryption and digital signatures.
How can I monitor RADIUS and PKI systems for security incidents?
Monitoring RADIUS and PKI systems for security incidents involves:
- Log analysis: Regularly review logs for suspicious activity, including failed authentication attempts, certificate revocation requests, and unusual traffic patterns.
- Security information and event management (SIEM): Utilize SIEM tools to collect and analyze security data from multiple sources, providing comprehensive visibility into potential threats.
- Intrusion detection systems (IDS): Deploy IDS to detect and alert on known attack patterns and malicious activities.





