What is hashing in cyber security – What is hashing in cybersecurity? Hashing is a fundamental concept in cybersecurity, playing a crucial role in ensuring data integrity and authenticity. It involves transforming data into a unique, fixed-length string of characters, known as a hash. This process is irreversible, meaning you can’t recreate the original data from the hash. Imagine a digital fingerprint that uniquely identifies a piece of information, providing a robust way to detect any unauthorized alterations or manipulations.
Hashing finds its way into numerous applications within the digital realm, including password protection, digital signatures, and blockchain technology. It acts as a cornerstone of cybersecurity, providing a reliable mechanism for verifying the integrity of data and protecting against malicious attacks.
Introduction to Hashing

Hashing is a fundamental concept in cybersecurity, acting like a unique fingerprint for data. It involves transforming any data, regardless of its size, into a fixed-length string of characters, known as a hash. This process is irreversible, meaning you can’t reconstruct the original data from its hash.
Hash Functions
A hash function is a mathematical algorithm that takes an input (data) and produces a unique output (hash). The key characteristic of a hash function is that it’s deterministic; the same input always generates the same output. This ensures consistency and predictability in the hashing process.
Real-world Examples of Hashing
Hashing finds applications in various aspects of our digital lives, often without us even realizing it.
- Password Storage: When you create an account on a website, your password is not stored directly. Instead, it’s hashed, and the hash is stored. This protects your password, as even if the database is compromised, attackers won’t have access to your actual password.
- File Integrity Verification: Hashing is used to verify the integrity of files. A hash is generated for a file, and this hash is then compared to a previously stored hash. If the hashes match, it confirms that the file hasn’t been tampered with. This is commonly used in software downloads to ensure that the downloaded file hasn’t been corrupted or altered.
- Digital Signatures: Hashing is used in digital signatures to ensure the authenticity and integrity of digital documents. A hash of the document is generated and encrypted with the sender’s private key. The recipient can then verify the signature by decrypting the hash using the sender’s public key and comparing it to the hash of the received document. If the hashes match, it confirms that the document is authentic and hasn’t been tampered with.
Hashing in Cybersecurity
Hashing plays a crucial role in cybersecurity, acting as a fundamental building block for ensuring data integrity and authenticity. It involves transforming data into a unique and fixed-length string of characters, known as a hash, using a mathematical function. This hash represents the original data, allowing for efficient verification and comparison.
Data Integrity
Hashing is instrumental in ensuring data integrity, which refers to the accuracy and completeness of information. When a hash is generated for a piece of data, any modification to the original data, even a single character change, will result in a different hash. This property makes hashing an effective tool for detecting alterations to data.
For example, consider a file containing sensitive financial information. If the hash of this file is stored securely, any changes made to the file, such as adding or deleting information, will be immediately evident when the hash is recalculated and compared to the original.
This approach provides a strong guarantee that the data has not been tampered with, offering a reliable mechanism for safeguarding sensitive information.
Data Authenticity
Hashing also plays a vital role in verifying the authenticity of data, confirming its origin and ensuring it has not been forged or altered. When a hash is associated with a specific data source, it acts as a digital fingerprint, uniquely identifying that source.
For instance, a digital signature often utilizes hashing to ensure the authenticity of an electronic document. The sender creates a hash of the document and encrypts it using their private key. The recipient can then verify the signature by decrypting the hash using the sender’s public key and comparing it to the hash of the received document.
This process confirms that the document originated from the claimed sender and has not been tampered with during transmission.
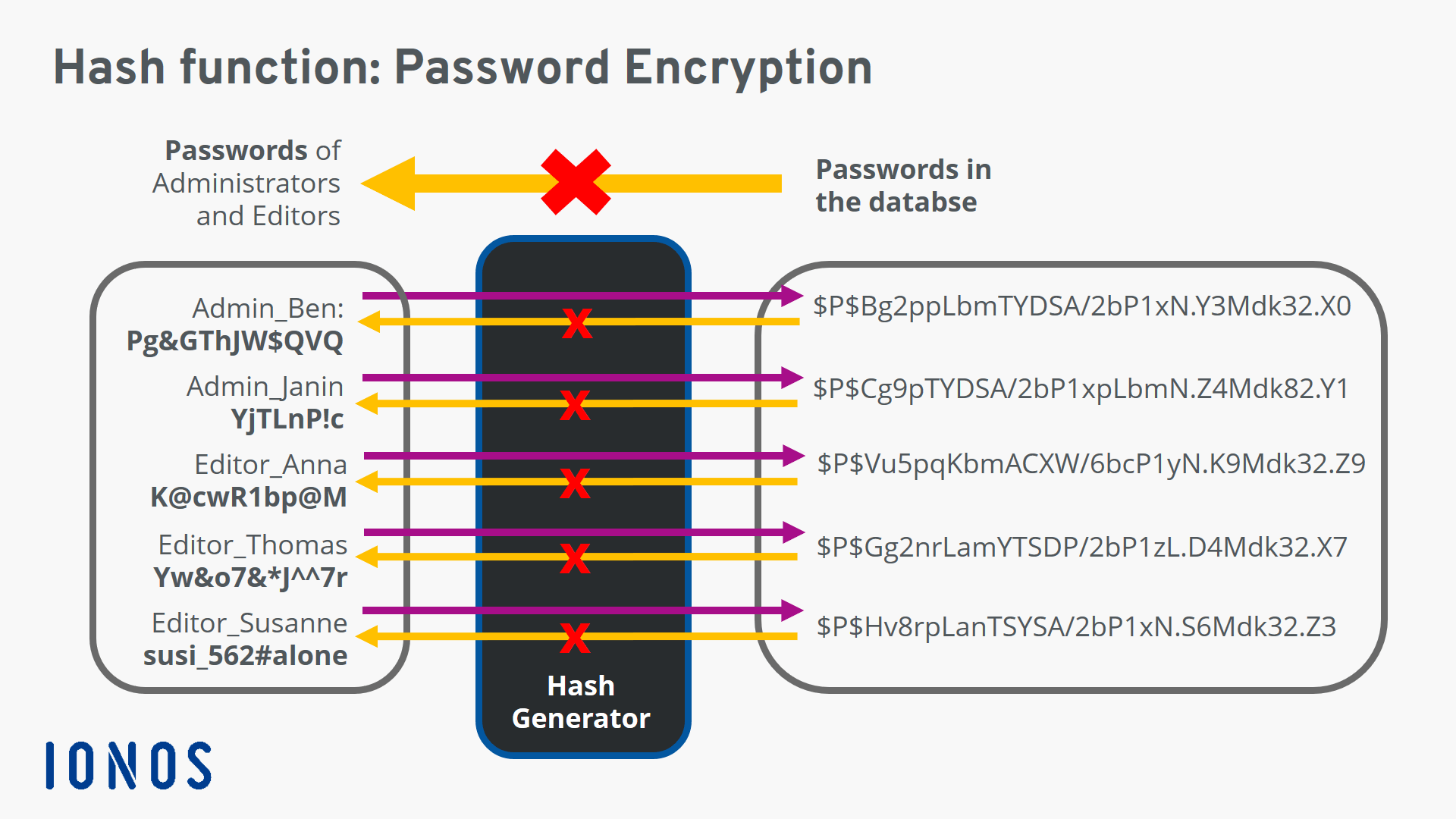
Password Protection
Hashing is widely used for password protection, providing a secure mechanism to store and manage user credentials. Instead of storing passwords in plain text, which is highly vulnerable to breaches, hashing transforms them into one-way functions.
This means that the original password cannot be retrieved from the hashed value, making it impossible for unauthorized individuals to access the passwords even if they gain access to the hashed data.
However, a robust password hashing algorithm should also be resistant to brute-force attacks, where attackers try to guess the original password by repeatedly hashing different combinations.
- Salt: A random string added to the password before hashing, making it more difficult for attackers to use pre-computed tables of common passwords and their corresponding hashes.
- Hashing iterations: The number of times a password is hashed, increasing the computational effort required to crack it.
Hashing Algorithms
Hashing algorithms are the mathematical functions that convert data of any size into a fixed-length string of characters, known as a hash value or message digest. They are a fundamental component of cybersecurity, playing a crucial role in data integrity, authentication, and digital signatures.
Common Hashing Algorithms
Hashing algorithms are essential for various security applications. They are used to ensure data integrity, authenticate users, and secure digital signatures. Some commonly used hashing algorithms in cybersecurity include MD5, SHA-1, and SHA-256.
- MD5 (Message Digest 5) is a widely used hashing algorithm that produces a 128-bit hash value. While it was once considered secure, it has been found to be vulnerable to collisions, where different inputs can produce the same hash value. This vulnerability makes it unsuitable for applications requiring high security.
- SHA-1 (Secure Hash Algorithm 1) generates a 160-bit hash value. Similar to MD5, SHA-1 has also been compromised, with researchers demonstrating the possibility of collisions. Consequently, it is no longer considered secure for critical applications.
- SHA-256 (Secure Hash Algorithm 256) is a more robust algorithm that produces a 256-bit hash value. It is considered more secure than MD5 and SHA-1 and is widely used in various applications, including digital signatures, blockchain technology, and password hashing.
Comparing Hashing Algorithms
Each hashing algorithm has its strengths and weaknesses.
| Algorithm | Hash Value Length | Strengths | Weaknesses |
|---|---|---|---|
| MD5 | 128 bits | Fast and efficient | Vulnerable to collisions |
| SHA-1 | 160 bits | More secure than MD5 | Vulnerable to collisions, although more difficult to exploit than MD5 |
| SHA-256 | 256 bits | Highly secure, considered collision-resistant | Slower than MD5 and SHA-1 |
Collision Resistance
Collision resistance is a crucial property of hashing algorithms. It refers to the difficulty of finding two different inputs that produce the same hash value. A collision-resistant algorithm makes it extremely challenging for attackers to manipulate data without detection.
A strong hashing algorithm should make it computationally infeasible to find two different inputs that produce the same hash value.
Collision resistance is essential for ensuring data integrity and preventing attackers from forging digital signatures or manipulating data without detection. For example, in digital signatures, the hash value of a document is used to verify its authenticity. If an attacker could find a collision, they could create a different document with the same hash value, potentially leading to fraudulent activities.
Applications of Hashing
Hashing, a fundamental concept in cybersecurity, finds diverse applications in various aspects of digital security, from ensuring data integrity to safeguarding online transactions. Let’s delve into some of the key areas where hashing plays a crucial role.
Digital Signatures
Digital signatures are electronic signatures that use cryptography to verify the authenticity and integrity of digital documents. They are based on the principle of asymmetric cryptography, where a pair of keys, a public key and a private key, is used to encrypt and decrypt information. Hashing plays a vital role in digital signatures by ensuring that the message hasn’t been tampered with during transmission.
The process involves the following steps:
- The sender uses a hash function to calculate the hash of the message.
- The sender then encrypts the hash using their private key. This encrypted hash is known as the digital signature.
- The sender attaches the digital signature to the message and sends it to the receiver.
- The receiver uses the sender’s public key to decrypt the digital signature and obtain the original hash.
- The receiver then calculates the hash of the received message using the same hash function.
- If the calculated hash matches the decrypted hash, the receiver can be confident that the message hasn’t been tampered with and originated from the claimed sender.
Blockchain Technology
Blockchain technology, renowned for its decentralized and secure nature, relies heavily on hashing for its core functionality. Each block in a blockchain contains a set of transactions, a timestamp, and a hash of the previous block. The hash of each block acts as a unique identifier and links it to the previous block, creating a chain of blocks. This chain structure ensures that any alteration to a block in the chain will result in a different hash, making it immediately apparent that the blockchain has been tampered with.
The immutability of the blockchain is a direct consequence of the use of hashing.
A blockchain can be considered a distributed ledger where each block is a record of transactions, and the hash function serves as a cryptographic seal that ensures the integrity of the entire chain.
Network Security Protocols
Hashing plays a crucial role in securing network communication by ensuring data integrity and authentication. Several network security protocols leverage hashing to achieve these objectives.
- Password Hashing: When a user creates an account on a website or service, their password is not stored in plain text but is instead hashed using a secure hashing algorithm.
If the password is compromised, only the hash is stolen, making it difficult for attackers to recover the original password. - Message Authentication Codes (MACs): MACs are used to verify the authenticity and integrity of messages sent over a network. A MAC is calculated by applying a hash function to the message and a secret key shared between the sender and receiver.
The receiver can verify the message by recalculating the MAC and comparing it to the received MAC. Any discrepancy indicates that the message has been tampered with or originated from an unauthorized source. - Secure Sockets Layer (SSL)/Transport Layer Security (TLS): SSL/TLS protocols are widely used to secure communication over the internet, such as online banking and e-commerce transactions.
Hashing is used in SSL/TLS to ensure the integrity of data exchanged between the client and server.
The server sends its public key to the client, which is then used to encrypt the session key.
The session key is used to encrypt all subsequent communication between the client and server.
Hashing and Data Security: What Is Hashing In Cyber Security
Hashing plays a pivotal role in safeguarding data by ensuring its integrity and confidentiality. The strength of the hashing algorithm used directly impacts the effectiveness of these security measures.
The Importance of Strong Hashing Algorithms
Strong hashing algorithms are essential for robust data security. They offer a high level of resistance against various attacks, such as brute-force attempts and collision attacks.
- Collision Resistance: A strong hashing algorithm produces unique hash values for distinct inputs, making it extremely difficult for attackers to find two inputs that generate the same hash. This prevents attackers from creating fake data that matches the hash of legitimate data.
- Preimage Resistance: A strong hashing algorithm makes it computationally infeasible to reverse the hashing process, meaning attackers cannot determine the original data from its hash value. This prevents them from altering or manipulating data without detection.
- Second Preimage Resistance: A strong hashing algorithm makes it difficult to find a different input that produces the same hash value as a given input. This property ensures that even if an attacker knows the hash value of a specific piece of data, they cannot create a different piece of data with the same hash.
Risks Associated with Weak or Compromised Hashing Algorithms
Using weak or compromised hashing algorithms poses significant security risks, potentially exposing sensitive data to attackers.
- Brute-Force Attacks: Weak algorithms are susceptible to brute-force attacks, where attackers systematically try different inputs until they find one that produces the desired hash value. This allows them to compromise data integrity and confidentiality.
- Collision Attacks: Weak algorithms may be vulnerable to collision attacks, where attackers find two different inputs that generate the same hash value. This allows them to forge data that appears legitimate, potentially leading to data manipulation and unauthorized access.
- Rainbow Table Attacks: Compromised algorithms may have pre-computed tables of hash values, known as rainbow tables, which attackers can use to quickly determine the original data from its hash value. This significantly weakens the security of data protected by such algorithms.
Examples of How Hashing Can Be Used to Protect Sensitive Data, What is hashing in cyber security
Hashing provides various methods to safeguard sensitive data:
- Password Storage: Hashing is commonly used to store passwords securely. Instead of storing passwords in plain text, websites store their hash values. If a database is compromised, attackers only gain access to the hash values, not the actual passwords. This makes it much harder for attackers to use the stolen data to access user accounts.
- Data Integrity Verification: Hashing is used to ensure data integrity by verifying that data has not been tampered with. When data is transmitted or stored, its hash value is calculated and stored alongside it. Upon retrieval, the hash value is recalculated and compared to the stored value. Any discrepancies indicate that the data has been altered, alerting users to potential breaches.
- Digital Signatures: Hashing is used to create digital signatures, which are used to authenticate the origin and integrity of digital documents. When a document is signed, its hash value is encrypted with the signer’s private key. Anyone with the signer’s public key can verify the signature by decrypting the hash value and comparing it to the hash value of the document.
This process ensures that the document is authentic and has not been tampered with.
Hashing in Practice
Hashing is a fundamental concept in cybersecurity, and its applications are numerous and diverse. It plays a crucial role in protecting data integrity, ensuring authenticity, and safeguarding user privacy. This section explores real-world scenarios where hashing is employed, examines a simple hashing system to illustrate its process, and delves into the challenges and limitations associated with its use.
Real-World Examples of Hashing
Hashing is a ubiquitous technology that underpins many security measures we encounter daily. Here are some prominent examples:
- Password Storage: Hashing is essential for storing passwords securely. Instead of storing passwords in plain text, which could be easily compromised, websites and applications store their hash values. When a user attempts to log in, the entered password is hashed and compared with the stored hash. If they match, authentication is successful. This prevents attackers from accessing passwords even if they gain access to the database.
- Data Integrity Verification: Hashing is used to ensure the integrity of data transmitted over networks. A hash value is calculated for the data before transmission. Upon receiving the data, the recipient calculates the hash again and compares it to the original hash. Any discrepancy indicates that the data has been tampered with. This technique is used in file downloads, email communication, and other data transfer scenarios.
- Digital Signatures: Hashing is central to digital signatures, which provide authenticity and non-repudiation. When a document is signed digitally, the hash of the document is encrypted using the signer’s private key. The recipient can then verify the signature by decrypting the hash using the signer’s public key and comparing it to the hash of the received document. This process ensures that the document is genuine and hasn’t been altered.
Illustrative Hashing System
To understand how hashing works, consider a simple system where we want to hash a message.
- Message: “Hello, world!”
- Hashing Function: A simple function that takes the message as input and outputs a fixed-length hash value. For example, we can sum the ASCII values of all characters in the message and take the modulo of the sum by a specific number.
- Hash Value: The output of the hashing function, which is a unique representation of the message. In this case, the hash value could be a number between 0 and 99 (if we take the modulo by 100).
For instance, if the sum of the ASCII values of the characters in the message is 937, and we take the modulo by 100, the hash value would be 37.
Challenges and Limitations of Hashing
While hashing is a powerful tool for cybersecurity, it does have some limitations:
- Collisions: Hashing functions are designed to produce unique hash values for different inputs. However, it is theoretically possible (though statistically improbable) for two different inputs to generate the same hash value. This is known as a collision. Collisions can undermine the integrity of hashing systems, as they can be exploited by attackers to create fake data that has the same hash value as the original data.
- Reverse Engineering: While hashing is a one-way function, it is possible in some cases to reverse engineer the hash value to obtain the original message. This is particularly true for weak hashing algorithms or when the hash value is generated using a small set of possible inputs. This vulnerability can be exploited by attackers to crack passwords or forge digital signatures.
- Complexity of Implementation: Implementing hashing algorithms securely and efficiently requires expertise and careful consideration of factors such as algorithm selection, key management, and error handling. Improper implementation can lead to security vulnerabilities and weaken the effectiveness of hashing systems.
In conclusion, hashing emerges as a powerful tool in the cybersecurity landscape, safeguarding data integrity and authenticity through its unique and irreversible nature. By understanding its principles and applications, we can appreciate its crucial role in securing our digital world. As technology continues to evolve, hashing remains a vital component of robust cybersecurity strategies, ensuring the trust and reliability of our digital interactions.
FAQ Compilation
How does hashing ensure data integrity?
Hashing ensures data integrity by generating a unique hash value for each piece of data. If the data is altered, even slightly, the hash value will change, indicating that the data has been tampered with.
What are some common hashing algorithms used in cybersecurity?
Some common hashing algorithms include MD5, SHA-1, and SHA-256. These algorithms vary in their complexity and security levels, with SHA-256 generally considered more secure than MD5 and SHA-1.
What are the risks associated with weak hashing algorithms?
Weak hashing algorithms are vulnerable to collisions, where two different inputs can generate the same hash value. This can compromise data integrity and allow attackers to forge data or bypass security measures.






