Imagine a fortress, built not of stone and mortar, but of layers of carefully crafted security measures. This fortress protects your most valuable assets – your data, your systems, and your reputation. This is the essence of an information security program, a strategic roadmap designed to safeguard your organization from cyber threats. What are the steps of the information security program lifecycle?
It’s a journey that involves meticulous planning, proactive implementation, constant monitoring, and continuous improvement.
The information security program lifecycle is a cyclical process that begins with a comprehensive assessment of your organization’s vulnerabilities and risks. You then create a detailed blueprint, outlining policies, controls, and procedures to mitigate those risks. Implementation is a critical phase where you put these strategies into action, from installing firewalls to training employees on best practices. The journey doesn’t end there.
You must constantly monitor your systems, detect threats, and respond effectively to incidents. Finally, you continuously evaluate your program’s effectiveness, identify areas for improvement, and adapt to the ever-changing landscape of cyber threats.
Planning Phase
Right, so the planning phase is like the foundation of your whole information security program. It’s where you set out your goals and figure out how you’re gonna achieve them. Think of it as planning a mega road trip – you need to know where you’re going, how you’re gonna get there, and what you’re gonna do along the way.
Aligning Information Security with Business Goals
The main aim of the planning phase is to make sure your information security program is actually useful and relevant to your business. You need to understand what your company’s goals are, and then figure out how information security can help you achieve them. It’s all about making sure your security measures are helping your business, not hindering it.
Risk Assessment
Risk assessment is like figuring out the potential hazards on your road trip. You need to identify what could go wrong, how likely it is to happen, and how much damage it could cause. This helps you prioritize what you need to protect and how much effort you need to put into it.
Identifying Risks
To identify risks, you need to look at all the different areas of your business and think about what could go wrong. This could be anything from a data breach to a system outage. You can use tools like threat modeling or brainstorming to help you think of all the possibilities.
Analyzing Risks
Once you’ve identified the risks, you need to analyze them to understand how likely they are to happen and how much damage they could cause. This is where you can use things like risk matrices and risk scoring models.
Prioritizing Risks
After you’ve analyzed the risks, you need to prioritize them based on how likely they are to happen and how much damage they could cause. This helps you focus your resources on the risks that are most important to address.
Developing an Information Security Policy
Your information security policy is like your road trip itinerary – it lays out the rules and guidelines for how you’re going to manage information security. It should cover all aspects of your program, from data classification to incident response.
Key Information Security Policies
- Access Control: This policy Artikels how you’re going to control who has access to your systems and data. It might include things like password policies, multi-factor authentication, and access reviews.
- Data Classification: This policy Artikels how you’re going to classify your data based on its sensitivity and importance. This helps you determine what level of security measures are needed for each type of data.
- Incident Response: This policy Artikels how you’re going to handle security incidents, like data breaches or system outages. It should include steps for identifying, containing, and recovering from incidents.
Statement of Information Security Program Objectives
Your information security program objectives are like the goals you set for your road trip – they define what you want to achieve with your program. They should be clear, concise, and measurable. Here’s an example:
“To protect the confidentiality, integrity, and availability of the organization’s information assets, and to comply with all applicable laws and regulations.”
Implementation Phase

Right, so the planning is done, now it’s time to actually put all those fancy security measures in place. This is where the real action happens, and it’s all about making sure your systems and data are properly protected.
Implementation of Security Controls
Here’s where we get into the nitty-gritty of putting those security controls in place. Think of it like building a fortress, but instead of moats and drawbridges, we’re using tech, policies, and physical barriers.
- Technical Controls: These are the techy bits that do the heavy lifting. They’re like the digital locks and alarms that keep your data safe. Examples include firewalls, intrusion detection systems (IDS), antivirus software, and encryption.
- Administrative Controls: These are the rules and procedures that guide how people use technology. They’re like the security guards who make sure everyone’s following the rules. Examples include security policies, access control lists, and incident response plans.
- Physical Controls: These are the physical measures that protect your hardware and data centres. They’re like the walls and fences that keep the bad guys out. Examples include security cameras, locks, and physical access control systems.
Examples of Security Controls
Here’s a rundown of specific security controls you can use for different areas of your business:
Network Security
- Firewalls: These act like a gatekeeper, blocking unauthorized access to your network. Think of them as the bouncers at a club, only letting in people on the guest list.
- Intrusion Detection Systems (IDS): These are like the security cameras that watch for suspicious activity on your network. If they spot anything fishy, they alert the security team.
- Virtual Private Networks (VPNs): These create a secure tunnel for your data to travel through, even if you’re using a public Wi-Fi network. Imagine it like a secret passageway that only you and your trusted friends can use.
Endpoint Security
- Antivirus Software: This software protects your devices from malware, like viruses and worms. It’s like a vaccine for your computer, keeping it healthy and protected.
- Endpoint Detection and Response (EDR): This is like a detective that investigates suspicious activity on your devices. It can identify and stop threats before they cause any damage.
- Data Loss Prevention (DLP): This software helps prevent sensitive data from leaving your network. It’s like a security guard who checks everyone’s bags before they leave the building.
Data Security
- Encryption: This scrambles your data so that only authorized people can read it. Think of it like locking your data in a safe, only accessible with the right key.
- Data Masking: This replaces sensitive data with fake data, protecting it from unauthorized access. Imagine it like disguising your data with a mask, so nobody can recognize it.
- Data Backup and Recovery: This ensures that you have a copy of your data in case something goes wrong. It’s like having a backup plan in case your house burns down.
User Awareness Training and Education
It’s not just about tech, mate. You need to make sure your users are clued up on how to stay safe online. It’s like teaching them how to spot a scam artist or how to handle a dangerous situation.
- Phishing Awareness: Teach users how to identify phishing emails and websites. These are like traps set by bad guys to steal your personal information.
- Password Security: Emphasize the importance of strong passwords and two-factor authentication. Think of it like using a combination lock on your digital door.
- Social Engineering: Explain how social engineering can be used to trick people into giving up sensitive information. It’s like someone trying to charm their way into your house by pretending to be a friend.
Best Practices for Implementing Security Awareness Programs
Here’s how to make your security awareness program a smash hit:
- Tailor Training Materials: Make sure your training materials are relevant to your users’ roles and responsibilities. You wouldn’t teach a chef how to build a website, would you?
- Use Engaging Content: Keep your training materials interesting and interactive. Nobody wants to sit through a boring lecture.
- Regularly Assess Understanding: Conduct regular quizzes and assessments to ensure users are absorbing the information. You wouldn’t want to leave them clueless, would you?
Checklist for Implementing Security Controls, What are the steps of the information security program lifecycle
Here’s a handy checklist to help you implement security controls across different departments:
| Department | Security Controls |
|---|---|
| Human Resources | Background checks, employee onboarding, security awareness training |
| IT Department | Firewall, intrusion detection systems, antivirus software, encryption |
| Finance Department | Access control lists, data masking, data backup and recovery |
| Sales and Marketing | Data loss prevention, secure email protocols, phishing awareness training |
| Operations | Physical security measures, security cameras, access control systems |
Operation and Monitoring Phase: What Are The Steps Of The Information Security Program Lifecycle

This phase is all about keeping your information security program running smoothly and making sure it’s actually doing its job. It’s like regularly servicing your car to make sure it’s safe and reliable.
Ongoing Monitoring and Assessment
You need to keep a close eye on your security program to make sure it’s still working effectively. This means regularly checking for any potential weaknesses and making sure everything is up to date. It’s like checking your car’s oil levels and tyre pressure to make sure it’s in tip-top shape.
Security Information and Event Management (SIEM)
SIEM tools are like your security system’s central control panel. They collect information from different parts of your network and systems, analyse it for suspicious activity, and alert you to potential threats. It’s like having a security guard watching all the cameras and sounding the alarm if they spot anything dodgy.
Security Audits and Penetration Testing
Regular security audits are like having a professional mechanic check your car for any problems. They look for any weaknesses in your security program and suggest ways to improve it. Penetration testing is like having a hacker try to break into your system to find any vulnerabilities. This helps you identify and fix any security flaws before they can be exploited.
Managing Security Incidents
No matter how good your security program is, there’s always a chance that something might go wrong. That’s why it’s important to have a plan in place for dealing with security incidents. It’s like having a first aid kit for your car – you might not need it often, but it’s essential to have it just in case.
Security Monitoring Tools
Here’s a table outlining different types of security monitoring tools and their key functionalities:| Tool Type | Key Functionalities ||—|—|| Intrusion Detection Systems (IDS) | Detecting malicious activity on a network || Intrusion Prevention Systems (IPS) | Blocking malicious activity on a network || Firewall | Controlling network traffic and preventing unauthorised access || Antivirus Software | Detecting and removing malware from systems || Vulnerability Scanners | Identifying security vulnerabilities in systems and applications || Log Management Tools | Collecting and analysing security logs to identify suspicious activity || Security Information and Event Management (SIEM) | Centralising security data from multiple sources and providing real-time threat detection and analysis |
Review and Improvement Phase
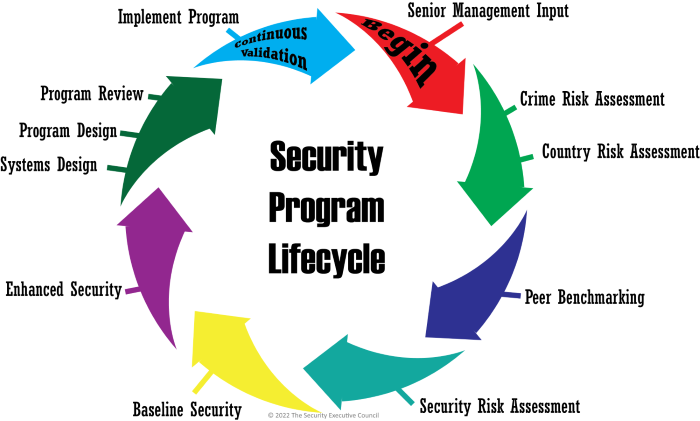
Right, so this is where you check if your security program is actually doing its job, and if not, you need to sort it out. Basically, you’re constantly checking and improving to keep up with the ever-changing world of cyber threats.
Key Performance Indicators (KPIs) for Evaluating Information Security Program Effectiveness
To make sure your security program is actually working, you need to set some goals and measure how well you’re hitting them. These goals are called KPIs.
- Number of Security Incidents: This shows how many times your security measures were breached. Ideally, you want this number to be low, and it’s important to track how many incidents were successful.
- Mean Time to Detect (MTTD): This tells you how long it takes to spot a security incident. The quicker you detect an issue, the less damage it can cause.
- Mean Time to Respond (MTTR): This is the time it takes to fix a security issue once it’s been found.
You want this to be as short as possible to minimise the impact of the incident.
- Security Awareness Training Completion Rates: This shows how many employees have completed security training. The more people who understand security, the less likely they are to accidentally cause a breach.
- Percentage of Systems with Security Patches Applied: This shows how many systems are up-to-date with the latest security patches. Keeping your systems patched helps to close security vulnerabilities.
Methods for Conducting Security Program Reviews and Assessments
There are different ways to review your security program and make sure it’s still doing its job.
- Internal Audits: This involves your own team checking your security program against your policies and procedures. It’s like a self-assessment, and it’s a good way to spot any gaps in your security.
- External Audits: This is where you bring in a third party to check your security program. They can provide a more objective assessment, and they might be able to spot things that your own team missed.
- Penetration Testing: This involves simulating a real attack on your systems to see how well your security holds up. It’s a good way to test your defenses and identify any vulnerabilities.
- Vulnerability Scanning: This is a automated process that scans your systems for known vulnerabilities. It’s a quick way to identify any potential security risks.
Identifying Areas for Improvement and Implementing Corrective Actions
Once you’ve done your reviews and assessments, you’ll probably find some areas where your security could be improved.
- Review the results of your audits and assessments: Look for any patterns or trends in the findings. This will help you identify the areas that need the most attention.
- Prioritise the areas for improvement: Not all issues are created equal. Focus on the most critical issues first, and then work your way down the list.
- Develop corrective actions: For each area for improvement, create a plan to address the issue.
This might involve updating policies, implementing new technologies, or providing additional training.
- Implement the corrective actions: Once you’ve developed your plan, put it into action. Make sure to monitor the progress and adjust your plan as needed.
Importance of Continuous Improvement and Adaptation of the Information Security Program to Evolving Threats
The world of cyber security is constantly changing, so you need to be constantly improving your security program to keep up.
“The only constant is change.” – Heraclitus
- Stay informed about new threats: Read security blogs, attend conferences, and talk to other security professionals. This will help you stay ahead of the curve and identify emerging threats.
- Update your policies and procedures: As new threats emerge, you may need to update your policies and procedures to address them.
- Implement new technologies: New security technologies are constantly being developed, so it’s important to keep up with the latest advancements.
- Provide ongoing security awareness training: Your employees are your first line of defense, so it’s important to keep them informed about security threats and best practices.
Examples of Security Program Improvement Initiatives
There are loads of things you can do to improve your security program. Here are a few examples:
- Implement multi-factor authentication (MFA): This adds an extra layer of security by requiring users to provide more than one form of authentication.
- Deploy an intrusion detection system (IDS): This system monitors your network for suspicious activity and alerts you to potential threats.
- Implement a data loss prevention (DLP) solution: This helps to prevent sensitive data from leaving your network.
- Enhance security awareness training: Provide regular training to your employees on security best practices, phishing attacks, and social engineering.
- Conduct regular security audits: These audits can help you identify vulnerabilities and areas for improvement in your security program.
In today’s interconnected world, information security is no longer an option – it’s a necessity. By following the steps of the information security program lifecycle, you can build a resilient fortress, protecting your organization from the ever-present threat of cyberattacks. Remember, security is a journey, not a destination. It requires ongoing vigilance, proactive measures, and a commitment to continuous improvement.
FAQ Explained
What is the difference between an information security policy and a security control?
An information security policy is a high-level document that Artikels an organization’s overall approach to security. It sets the framework for security practices. Security controls, on the other hand, are specific mechanisms or procedures designed to implement those policies. They are the tangible actions taken to protect information assets.
What are some common examples of security controls?
Security controls can be technical, administrative, or physical. Examples include firewalls, intrusion detection systems, access control lists, data encryption, employee training, security audits, and physical security measures like locks and security cameras.
How often should I review and update my information security program?
It’s recommended to review your program at least annually, or more frequently if there are significant changes in your organization’s operations, technology, or regulatory environment. Keep in mind that the cyber threat landscape is constantly evolving, so staying ahead of the curve is crucial.
What are some common information security certifications?
There are several certifications available for individuals working in information security. Some popular ones include the Certified Information Systems Security Professional (CISSP), Certified Information Security Manager (CISM), and CompTIA Security+.






