Which of the following is associated with port security? This question delves into the critical realm of network security, where protecting sensitive data and preventing unauthorized access are paramount. Port security, a fundamental element of network defense, plays a vital role in safeguarding network infrastructure and ensuring data integrity. It involves implementing security measures at the network port level, restricting access and preventing malicious activity.
By understanding the core principles of port security, network administrators can bolster their network’s resilience against a wide range of threats, from accidental misconfigurations to targeted attacks.
Port security encompasses a range of mechanisms and techniques designed to secure network ports and prevent unauthorized access. These mechanisms can include MAC address filtering, which restricts access to specific devices based on their MAC addresses, port authentication, which verifies the identity of devices before granting access, and port lockdown, which disables unused ports to minimize potential vulnerabilities. Implementing these measures effectively requires careful planning, configuration, and ongoing monitoring to ensure that the network remains secure.
Port Security Fundamentals
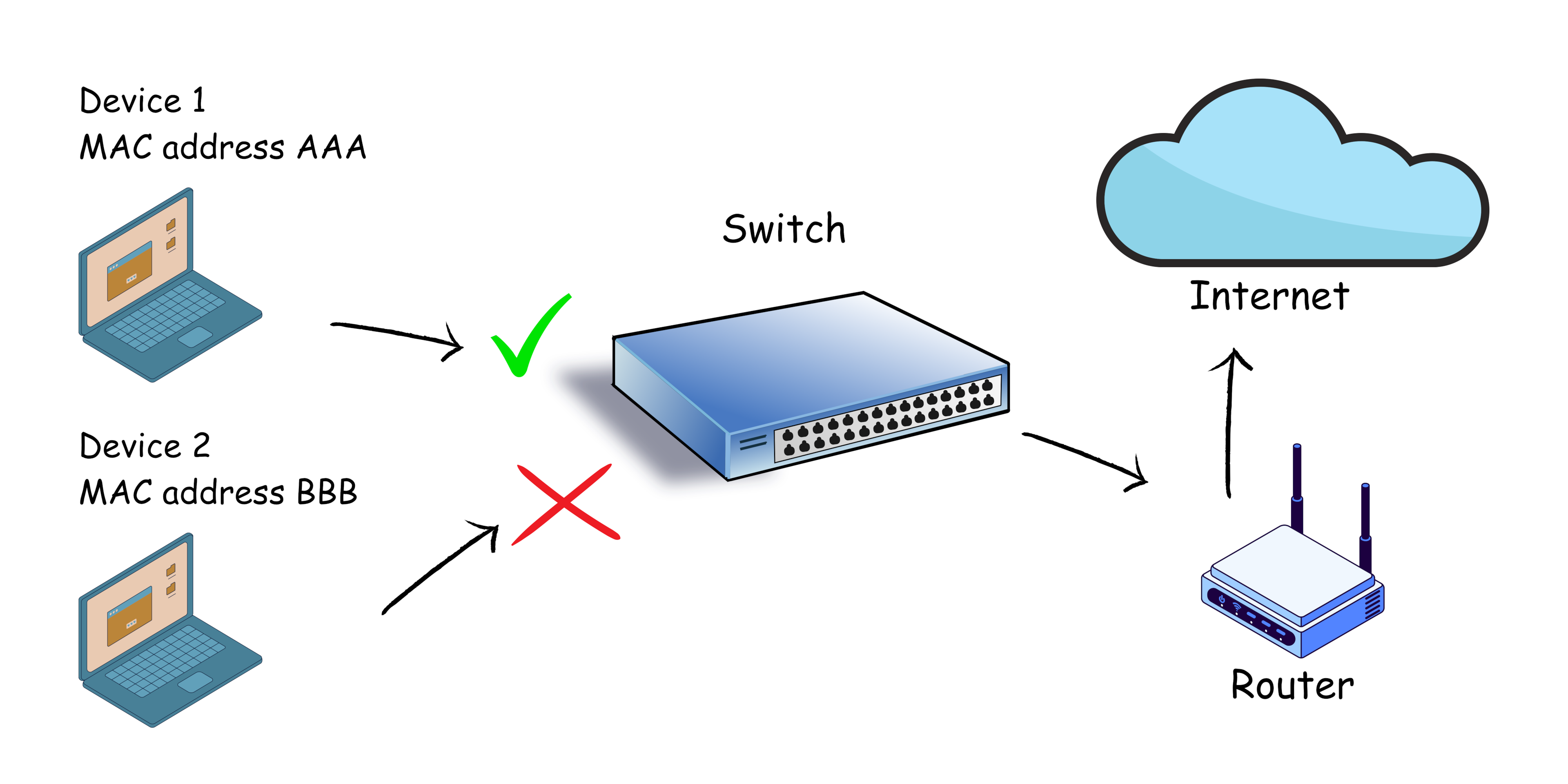
In the ever-evolving landscape of network security, safeguarding network access points is paramount. Port security, a fundamental aspect of network defense, plays a crucial role in ensuring the integrity and confidentiality of network traffic.
Purpose of Port Security
Port security aims to prevent unauthorized access to network devices and resources by controlling the flow of traffic at the physical layer. It establishes a robust defense mechanism against various security threats, including unauthorized connections, MAC address spoofing, and denial-of-service attacks.
Key Principles and Concepts
Port security operates on the principle of limiting access to network ports based on specific criteria. This involves defining authorized devices and their associated MAC addresses, thereby restricting access to only those permitted devices.
Real-World Scenarios
Port security finds its application in numerous real-world scenarios, where it is crucial for maintaining network security.
- Secure Network Access: In organizations with sensitive data, port security ensures that only authorized devices can connect to the network. This prevents unauthorized users from gaining access to confidential information.
- Preventing MAC Address Spoofing: Port security mitigates the risk of MAC address spoofing, where attackers attempt to impersonate legitimate devices to gain access to the network. By verifying MAC addresses, port security ensures that only authorized devices can connect.
- Protecting Against Denial-of-Service Attacks: Port security can help protect against denial-of-service (DoS) attacks, where attackers flood a network with traffic, overwhelming the network’s resources and making it unavailable to legitimate users.
Port Security Mechanisms: Which Of The Following Is Associated With Port Security
Imagine a fortress, its walls fortified to keep intruders at bay. Similarly, in the digital realm, network devices employ robust mechanisms to protect their ports from unauthorized access. These mechanisms, collectively known as port security, act as vigilant guardians, ensuring only authorized devices can connect and communicate.
MAC Address Filtering
MAC address filtering is a fundamental port security mechanism. It operates by creating a whitelist of authorized MAC addresses, allowing only devices with those specific addresses to connect to the port. Any device attempting to connect with a MAC address not on the whitelist is blocked.
MAC address filtering is like a gatekeeper checking IDs. Only those with valid IDs are allowed entry.
MAC address filtering is relatively simple to implement and can be effective in preventing unauthorized access. However, it has limitations. It is susceptible to MAC address spoofing, where attackers can disguise their devices with a valid MAC address. Additionally, managing a large whitelist can be cumbersome, especially in dynamic environments where devices frequently change.
Port Authentication
Port authentication is a more robust mechanism that goes beyond simple MAC address filtering. It involves a secure authentication process to verify the identity of devices before granting access. This process typically involves the exchange of credentials, such as usernames and passwords, or the use of digital certificates.
Port authentication is like a sophisticated security system that verifies identities through multiple checks.
Port authentication provides a higher level of security compared to MAC address filtering. It is less susceptible to spoofing attacks and offers greater control over access. However, it requires more configuration and can be more complex to implement.
Port Lockdown
Port lockdown is the most restrictive port security mechanism. It disables all communication on a port, effectively locking it down. This is typically used for ports that are not actively used or for ports that need to be isolated for security reasons.
Port lockdown is like sealing a door shut, preventing any access.
Port lockdown offers the highest level of security, but it can also be disruptive if not implemented carefully. It is important to ensure that legitimate devices are not inadvertently locked out.
Comparison of Port Security Mechanisms
| Mechanism | Effectiveness | Implementation Complexity ||—|—|—|| MAC Address Filtering | Moderate | Low || Port Authentication | High | Moderate || Port Lockdown | Highest | High |
Practical Examples
MAC Address Filtering
In a small office network, a network administrator might configure a switch to allow only specific laptops and printers to connect to a specific port. This prevents unauthorized devices from accessing the network.
Port Authentication
In a corporate network, a switch might be configured to require 802.1x authentication before granting access to a port. This ensures that only authorized users with valid credentials can connect to the network.
Port Lockdown
In a server room, a switch might be configured to lock down all unused ports, reducing the risk of unauthorized access.
Port Security Configuration
Port security is a critical layer of defense for modern networks, ensuring the integrity and security of your infrastructure. It works by defining and enforcing access control rules for each port on your network switch or router, effectively limiting which devices can connect to your network.
Configuration Parameters
Port security configuration involves defining a set of parameters that dictate how the switch or router will enforce access control on each port. These parameters are essential for customizing the security behavior of your network and achieving the desired level of protection.
- Port Security Mode: This parameter determines the specific security policy that will be applied to the port. Common modes include:
- Static: This mode allows you to explicitly define the MAC addresses of devices permitted to connect to the port. Only devices with authorized MAC addresses will be granted access.
- Dynamic: This mode dynamically learns the MAC addresses of devices that connect to the port and automatically grants them access. However, it often includes a maximum number of allowed devices (maximum MAC addresses) to prevent unauthorized connections.
- Sticky: This mode combines the features of static and dynamic modes. It allows you to manually define static MAC addresses while also dynamically learning new addresses within the allowed limit. This offers a balance between control and flexibility.
- Maximum MAC Addresses: This parameter defines the maximum number of unique MAC addresses that are allowed to connect to the port. This helps prevent MAC address flooding attacks, where attackers attempt to overwhelm the switch with a large number of MAC addresses, potentially disrupting network connectivity.
- Violation Action: This parameter defines the action that the switch or router will take when a port security violation occurs. Common actions include:
- Shutdown: This action immediately disables the port, preventing any further traffic from passing through it. This is the most common and effective action for preventing unauthorized access.
- Restrict: This action limits the port to only allow traffic from the authorized MAC addresses. This allows for some level of communication while still preventing unauthorized access.
- Log: This action logs the violation event in the switch or router’s logs, allowing you to track and investigate security incidents. This is a useful option for monitoring and auditing purposes.
- Aging Time: This parameter defines the amount of time that a learned MAC address will be kept in the port security database. After the aging time expires, the MAC address will be removed, requiring the device to reauthenticate to access the port. This helps prevent unauthorized access if a device with a learned MAC address is removed from the network.
Configuration Guide, Which of the following is associated with port security
The specific steps for configuring port security will vary depending on the network device model you are using. However, the general process will involve accessing the device’s command-line interface (CLI) or web-based management interface and configuring the desired parameters for each port.
For example, to configure port security on a Cisco switch, you would use the following commands:
- Enable port security: This command enables port security on the selected port.
switch(config)# interface
switch(config-if)# port security - Define maximum MAC addresses: This command sets the maximum number of MAC addresses allowed on the port.
switch(config-if)# port security maximum - Define violation action: This command sets the action that the switch will take when a violation occurs.
switch(config-if)# port security violation - Define static MAC addresses: This command manually defines the MAC addresses of devices allowed to connect to the port.
switch(config-if)# port security mac-address
Port Security Best Practices
Port security, a crucial aspect of network security, safeguards your network by controlling access to network ports. Implementing best practices ensures the effectiveness of port security, protecting your network from unauthorized access and malicious activities. This section delves into practical strategies to enhance the security of your network.
Optimizing Port Security Settings
Effective port security relies on meticulous configuration. Here are key practices for optimizing port security settings:
- Enable Port Security: The first step is to enable port security on all switches. This restricts access to ports based on defined rules.
- Configure Port Security Mode: Select the appropriate port security mode for your network environment. Common modes include:
- Static Mode: This mode allows you to manually configure MAC addresses for authorized devices. It provides a high level of security but requires manual configuration for each device.
- Dynamic Mode: In this mode, the switch dynamically learns the MAC addresses of connected devices. It simplifies configuration but may require additional security measures to prevent MAC address spoofing.
- Set Maximum MAC Address Limit: Limit the number of MAC addresses allowed on a port to prevent MAC flooding attacks.
- Configure Port Security Violation Action: Determine the action to be taken when a violation occurs. Options include:
- Shutdown: Disconnect the port from the network.
- Restrict: Block traffic from the violating device.
- Log: Record the violation in the switch’s log files.
- Use Strong Authentication Methods: Employ robust authentication methods like 802.1x for secure access control.
Troubleshooting Port Security Issues
Troubleshooting port security issues can be challenging. The following tips can help you resolve common problems:
- Verify Configuration: Ensure that the port security settings are correctly configured and match your network requirements.
- Check Switch Logs: Analyze the switch logs for any port security violations or errors.
- Test Connectivity: Verify that authorized devices can access the network while unauthorized devices are blocked.
- Use Network Monitoring Tools: Employ network monitoring tools to analyze traffic patterns and identify any suspicious activity related to port security.
Best Practices for Implementing and Managing Port Security
Implementing port security effectively requires a holistic approach. Here are best practices to ensure ongoing effectiveness:
- Regularly Review Configuration: Periodically review and update port security settings to reflect changes in network topology and security requirements.
- Implement Security Awareness Training: Educate users about port security policies and best practices to minimize security risks.
- Use a Secure Configuration Management System: Employ a secure configuration management system to track changes and maintain consistency across network devices.
- Monitor Network Activity: Continuously monitor network activity for any suspicious behavior that could indicate port security vulnerabilities.
Port Security in Different Network Environments
Port security, a crucial aspect of network security, plays a vital role in protecting networks from unauthorized access and malicious activities. Implementing port security in different network environments requires a tailored approach, considering the specific challenges and constraints of each environment. This section delves into the unique considerations for implementing port security in corporate networks, data centers, and wireless networks, analyzing its impact on network performance and scalability, and outlining a comprehensive port security strategy for a specific network environment.
Port Security in Corporate Networks
Corporate networks often face a complex interplay of security needs and performance demands. Implementing port security in corporate networks necessitates careful planning and execution to balance security measures with operational efficiency.
- User Authentication and Access Control: Corporate networks typically have a diverse user base with varying levels of access privileges. Port security plays a crucial role in enforcing access control policies, ensuring that only authorized users can connect to specific network resources. Implementing robust user authentication mechanisms, such as multi-factor authentication, is essential to prevent unauthorized access.
- Network Segmentation: Segmenting the corporate network into logical zones with different security levels is essential for mitigating the impact of security breaches. Port security can be leveraged to restrict communication between different network segments, preventing unauthorized access and data leakage.
- Device Control and Management: Corporate networks often have a large number of devices, including laptops, desktops, mobile devices, and servers. Port security can be used to control the types of devices that can connect to the network, ensuring that only authorized and managed devices are allowed access.
Port Security in Data Centers
Data centers are the heart of many organizations, housing critical infrastructure and sensitive data. Implementing port security in data centers is crucial for maintaining data integrity, ensuring high availability, and preventing unauthorized access.
- Data Integrity and Confidentiality: Data centers are responsible for storing and processing sensitive data, making data integrity and confidentiality paramount. Port security helps prevent unauthorized access to data, ensuring that only authorized personnel can access critical data.
- High Availability and Redundancy: Data centers are designed for high availability and redundancy to ensure uninterrupted service. Port security plays a role in maintaining network stability by preventing unauthorized connections that could disrupt network traffic.
- Compliance and Security Audits: Data centers often operate under strict compliance requirements, such as PCI DSS and HIPAA. Port security helps meet these compliance standards by ensuring that only authorized devices and users can access sensitive data.
Port Security in Wireless Networks
Wireless networks, while offering convenience and flexibility, pose unique security challenges. Implementing port security in wireless networks requires a comprehensive approach to address the vulnerabilities associated with wireless communication.
- Wireless Access Point Security: Wireless access points are the gateway to the wireless network. Implementing strong security measures on access points, such as WPA2/3 encryption and robust authentication protocols, is crucial for preventing unauthorized access.
- Client Device Authentication: Authenticating client devices connecting to the wireless network is essential to prevent unauthorized access. Port security mechanisms can be used to enforce device authentication, ensuring that only authorized devices can access the network.
- Wireless Network Segmentation: Segmenting the wireless network into logical zones with different security levels is essential for mitigating the impact of security breaches. Port security can be used to restrict communication between different wireless network segments.
Impact of Port Security on Network Performance and Scalability
Port security can have an impact on network performance and scalability. While it enhances security, it can also introduce overhead and potentially affect network speed.
- Performance Overhead: Port security mechanisms, such as MAC address filtering and port security policies, can introduce a small amount of processing overhead. However, this overhead is generally minimal and does not significantly impact network performance.
- Scalability Considerations: Implementing port security on a large network can require significant configuration and management effort. Scalability challenges can arise when managing a large number of ports and devices, requiring robust tools and automation for effective port security management.
Designing a Port Security Strategy
Designing a port security strategy involves a comprehensive approach that considers the specific requirements and constraints of the network environment.
- Network Security Assessment: A thorough network security assessment is the first step in designing a port security strategy. This assessment identifies potential vulnerabilities and security risks, providing a foundation for implementing appropriate port security measures.
- Port Security Policy Development: Defining a clear and comprehensive port security policy is crucial. This policy should Artikel the specific security requirements, access control rules, and enforcement mechanisms for the network.
- Implementation and Monitoring: Implementing the port security strategy requires careful configuration and testing. Continuous monitoring is essential to ensure that the port security mechanisms are functioning as intended and to detect any potential security breaches.
In conclusion, port security is a critical aspect of network security, ensuring the integrity and confidentiality of data. By implementing robust port security measures, organizations can significantly reduce their vulnerability to various threats, including unauthorized access, data breaches, and denial-of-service attacks. Understanding the different mechanisms, configuring them effectively, and adhering to best practices are crucial for maximizing the effectiveness of port security and safeguarding network infrastructure.
As technology evolves and threats become more sophisticated, staying informed about the latest port security advancements and adapting to evolving needs is essential for maintaining a secure and reliable network environment.
Answers to Common Questions
What are the common port security vulnerabilities?
Common port security vulnerabilities include misconfigurations, weak authentication methods, and outdated security protocols. These vulnerabilities can expose networks to various threats, such as unauthorized access, data breaches, and denial-of-service attacks.
How can I monitor port security effectiveness?
Monitoring port security effectiveness involves regularly reviewing security logs, analyzing network traffic patterns, and conducting vulnerability assessments. By proactively monitoring these aspects, organizations can identify potential issues and address them before they escalate.
What are the benefits of implementing port security?
Implementing port security offers numerous benefits, including enhanced network security, reduced vulnerability to attacks, improved data confidentiality, and increased compliance with security regulations.








