How do phishing simulations contribute to enterprise security? In an era of increasingly sophisticated cyber threats, organizations are constantly seeking ways to strengthen their defenses. Phishing simulations, a powerful tool for bolstering cybersecurity, offer a proactive approach to mitigating the risks associated with these attacks. These simulations, designed to mimic real-world phishing attempts, provide a valuable opportunity for organizations to assess their employees’ susceptibility to social engineering tactics and identify vulnerabilities in their security practices.
By exposing employees to realistic phishing scenarios, simulations provide a controlled environment for learning and improvement. They not only highlight the importance of vigilance and caution but also serve as a catalyst for training and education, empowering employees to recognize and avoid phishing attacks. Phishing simulations, therefore, play a crucial role in enhancing enterprise security by equipping employees with the knowledge and skills necessary to safeguard sensitive information and protect their organization from the devastating consequences of a successful phishing attack.
Understanding Phishing Simulations

Phishing simulations are a crucial component of any robust cybersecurity strategy. These simulations, designed to mimic real-world phishing attacks, help organizations educate their employees about phishing threats and build their resilience against these attacks. By understanding the purpose, types, and impact of phishing simulations, organizations can effectively mitigate the risks posed by phishing attacks.
Types of Phishing Simulations
Phishing simulations are not a one-size-fits-all approach. Organizations can leverage different types of simulations to target specific vulnerabilities and create realistic scenarios.
- Email Phishing Simulations: These are the most common type of phishing simulations, where employees receive emails designed to appear legitimate but contain malicious links or attachments. These simulations can be tailored to mimic specific phishing campaigns, such as those targeting login credentials or financial information.
- SMS Phishing Simulations: With the rise of mobile devices, SMS phishing attacks are becoming increasingly prevalent. These simulations mimic SMS messages that appear to be from legitimate sources, but contain malicious links or requests for sensitive information.
- Social Media Phishing Simulations: Social media platforms are another fertile ground for phishing attacks. These simulations can involve fake accounts, malicious links, or phishing attempts disguised as promotions or contests.
Benefits of Phishing Simulations
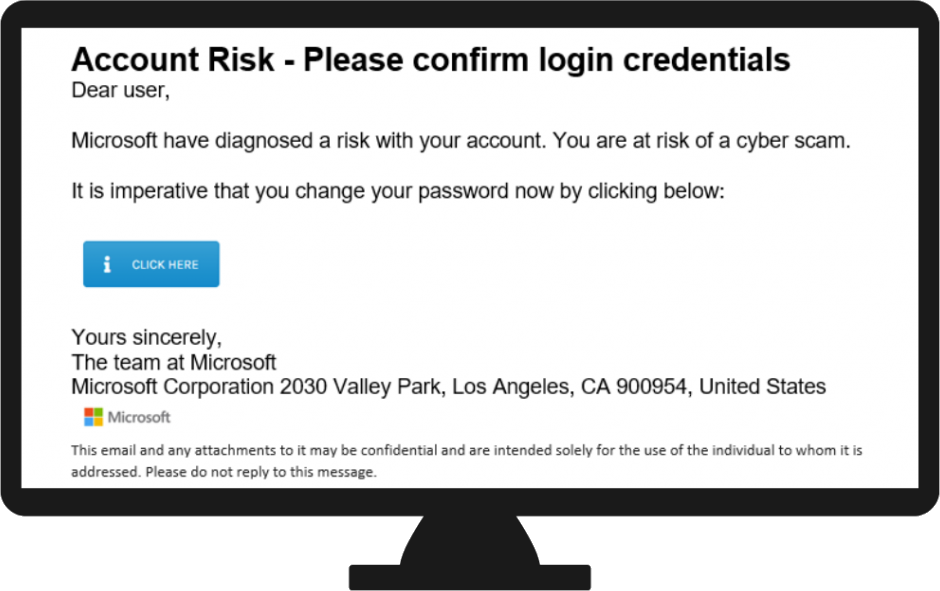
Phishing simulations offer a powerful tool for bolstering enterprise security by providing insights into vulnerabilities and fostering a proactive approach to cybersecurity. By mimicking real-world phishing attacks, organizations can gain valuable information about employee awareness, security practices, and the effectiveness of their existing security controls.
Identifying Vulnerabilities
Phishing simulations serve as a crucial tool for identifying weaknesses in employee awareness and security practices. By sending realistic phishing emails, organizations can gauge how effectively their employees can recognize and report suspicious emails. The results of these simulations provide a clear picture of the organization’s vulnerability to phishing attacks, highlighting areas where training and education are needed. For example, a high click-through rate on a simulated phishing email might indicate a lack of awareness about phishing threats, while a low reporting rate could point to inadequate processes for reporting suspicious activity.
Improving User Education and Training
Phishing simulations play a vital role in enhancing user education and training, empowering employees to become the first line of defense against phishing attacks. Through these simulations, employees gain practical experience in identifying phishing emails, understanding the tactics used by attackers, and learning the proper procedures for reporting suspicious activity. By providing regular and realistic simulations, organizations can continuously reinforce these critical skills, fostering a culture of security awareness among their workforce.
Implementing Phishing Simulations
Successfully implementing phishing simulations requires a well-defined strategy and a careful approach. It’s not simply about sending out fake emails and hoping for the best. It’s about creating a learning experience that empowers employees to be vigilant against real phishing attacks.
Designing and Launching a Phishing Simulation Campaign
Designing and launching a phishing simulation campaign requires a structured approach. Here’s a breakdown of the key steps:
- Define Objectives and Scope: Start by clearly defining the goals of your simulation. Are you aiming to assess employee awareness, test security controls, or both? Determine the target audience, the types of phishing attacks to simulate, and the overall scope of the campaign.
- Choose a Simulation Platform: Select a reputable phishing simulation platform that aligns with your needs and budget. Consider features like ease of use, reporting capabilities, and customization options. Look for a platform that provides comprehensive analytics and insights into employee behavior.
- Develop Realistic Phishing Emails: Crafting convincing phishing emails is crucial for a successful simulation. Use real-world attack techniques and tailor the content to resonate with your employees. Include elements like urgency, authority, and social engineering tactics to make the emails seem legitimate.
- Pre-Simulation Training: Before launching the simulation, provide employees with some basic phishing awareness training. This can help them identify common phishing tactics and understand the importance of reporting suspicious emails. This pre-training serves as a foundation for the simulation.
- Launch the Simulation: Once your simulation is ready, launch it strategically. Consider factors like timing, frequency, and the number of employees involved. A phased approach, starting with a small group and gradually expanding, can be effective. This allows for adjustments and refinements as needed.
- Monitor and Analyze Results: Track employee engagement and analyze the simulation data. Identify the most successful phishing emails, the click-through rates, and the employees who fell for the scams. Use this information to identify areas for improvement and adjust future simulations accordingly.
- Provide Feedback and Remediation: After the simulation, provide clear and constructive feedback to employees. Highlight their strengths and weaknesses and offer specific recommendations for improving their phishing awareness. Consider offering follow-up training or resources to address any identified gaps in knowledge or skills.
Checklist for Creating Realistic and Effective Simulations
Creating realistic and effective simulations is key to maximizing their impact. Here’s a checklist of key considerations:
- Use Real-World Attack Tactics: Don’t rely on generic phishing templates. Research current phishing trends and incorporate common attack vectors like spoofed emails, social engineering, and malware delivery. This ensures the simulation reflects the threats employees face in the real world.
- Personalize Emails: Tailor phishing emails to specific departments or job roles. Use relevant language, subject lines, and attachments that resonate with the target audience. This increases the likelihood that employees will find the emails believable.
- Include a Variety of Phishing Techniques: Don’t limit yourself to just one type of phishing attack. Use a mix of techniques like spear phishing, whaling, and social engineering to challenge employees and expose them to different threats. This broadens their understanding of phishing tactics.
- Set Clear Expectations: Communicate the purpose and expectations of the simulation to employees upfront. Explain that it’s a learning opportunity and that there are no penalties for falling for the scams. This helps to create a safe and supportive environment for learning. Emphasize the importance of reporting any suspicious emails, regardless of whether they are part of the simulation or not.
- Provide Timely Feedback: Don’t delay providing feedback to employees after the simulation. The sooner they receive information about their performance, the more likely they are to retain the lessons learned. Provide detailed reports and insights into their behavior, and offer recommendations for improvement.
The Importance of Clear Communication and Feedback
Clear communication and timely feedback are essential for the success of any phishing simulation. Here’s why:
- Builds Trust: Open and transparent communication helps to build trust with employees. By explaining the purpose and benefits of the simulation, you demonstrate that you’re committed to their security and well-being.
- Encourages Participation: Clear communication ensures that employees understand the simulation and are motivated to participate. This leads to more accurate data and a more effective learning experience.
- Reinforces Lessons Learned: Feedback provides employees with a valuable opportunity to reflect on their actions and understand the consequences of their choices. It helps to reinforce the lessons learned and improve their phishing awareness over time.
- Identifies Gaps in Training: Analyzing the simulation data can reveal areas where employees need additional training or support. This allows you to tailor future training programs to address specific needs and improve overall security awareness.
Measuring the Effectiveness of Phishing Simulations

The true value of phishing simulations lies in their ability to drive positive change within your organization. To gauge this impact, you need to measure the success of your phishing simulation campaigns. By analyzing key metrics and understanding how employees respond to simulations, you can fine-tune your training and security initiatives for maximum effectiveness.
Key Metrics for Measuring Success
Tracking the right metrics is crucial to understanding the effectiveness of your phishing simulations. These metrics can be categorized into two main areas: employee engagement and improvement.
- Phishing Simulation Click Rates: This metric measures the percentage of employees who click on a phishing link in a simulation. A high click rate indicates a need for more training, while a low click rate suggests employees are becoming more vigilant.
- Phishing Simulation Completion Rates: This metric tracks the percentage of employees who complete the phishing simulation. A high completion rate indicates good employee engagement and a willingness to participate in the training.
- Time to Report Phishing Attempts: This metric measures the time it takes employees to report a suspected phishing attempt. A shorter reporting time indicates a faster response and potentially less damage.
- Number of Phishing Reports: This metric tracks the number of phishing attempts reported by employees. A high number of reports indicates that employees are actively looking for phishing attempts and reporting them, which is a positive sign.
- Employee Feedback: This metric measures employee satisfaction with the phishing simulations and their perceived value in improving security awareness.
Analyzing Simulation Results
Analyzing simulation results involves more than just looking at the numbers. It’s about understanding the trends, identifying areas for improvement, and tailoring future training accordingly.
- Identifying Patterns: Analyze the data to identify any patterns in employee behavior. For example, are certain departments or job roles more susceptible to phishing attempts? Are there specific types of phishing attacks that are more effective?
- Tailoring Training: Use the data to tailor your training to address the specific needs of your employees. If a particular department is more susceptible to phishing, provide them with targeted training on that specific type of attack.
- Measuring Improvement: Track the metrics over time to see if there is any improvement in employee behavior. If you see a decrease in click rates and an increase in reporting times, it indicates that your training is having a positive impact.
- Continual Improvement: Phishing simulation campaigns should be an ongoing process. By continually monitoring the results and making adjustments to your training, you can keep your employees one step ahead of cybercriminals.
Best Practices for Phishing Simulations: How Do Phishing Simulations Contribute To Enterprise Security
Phishing simulations are a critical component of any comprehensive cybersecurity strategy. To maximize their effectiveness, it’s crucial to implement best practices that ensure simulations are ethical, engaging, and ultimately contribute to a stronger security posture.
Creating Ethical and Engaging Simulations, How do phishing simulations contribute to enterprise security
Ethical considerations are paramount when designing phishing simulations. Striking a balance between realistic scenarios and avoiding unnecessary stress or anxiety for employees is essential. Here are some best practices to consider:
- Clear Communication and Transparency: Inform employees about the purpose and nature of the simulations. Transparency builds trust and encourages active participation.
- Realistic but Not Deceptive: Design simulations that mirror real-world phishing attacks but avoid using misleading or deceptive tactics that could cause undue alarm.
- Focus on Education: Emphasize the learning aspect of the simulations. Provide clear feedback and educational resources to help employees understand the threats and best practices for avoiding them.
- Variety and Innovation: Introduce different types of phishing attacks (e.g., email, SMS, social media) and vary the scenarios to keep employees engaged and prevent them from becoming complacent.
- Gamification: Incorporate gamification elements, such as points, badges, and leaderboards, to enhance employee engagement and create a sense of friendly competition.
Ensuring Employee Privacy and Data Security
Protecting employee privacy and data security during phishing simulations is crucial. Implementing safeguards ensures that simulations are conducted ethically and responsibly.
- Data Anonymization: Use anonymized data or fictional information in simulations to avoid exposing sensitive employee details.
- Limited Scope: Restrict the scope of the simulations to specific departments or groups to minimize the potential impact on sensitive data.
- Data Retention and Disposal: Establish clear policies for data retention and disposal after the simulation to ensure proper handling of sensitive information.
- Compliance with Regulations: Ensure that simulations comply with relevant privacy regulations (e.g., GDPR, CCPA) to protect employee data.
Regular and Ongoing Phishing Simulations
Regular phishing simulations are essential to maintain a strong security posture. Consistent exposure to simulated attacks helps employees develop vigilance and improve their ability to identify and report real threats.
- Frequency: Conduct simulations on a regular basis, ideally every few months, to reinforce security awareness and keep employees on their toes.
- Variety of Scenarios: Introduce different types of phishing attacks and scenarios to challenge employees’ skills and keep them engaged.
- Targeted Approach: Tailor simulations to specific departments or roles based on their unique security risks and responsibilities.
- Post-Simulation Analysis: Analyze the results of each simulation to identify areas for improvement and adjust future simulations accordingly.
Phishing simulations are not merely a compliance exercise; they are an integral component of a comprehensive security strategy. By simulating real-world threats, these exercises provide invaluable insights into employee behavior and security vulnerabilities, enabling organizations to make informed decisions regarding training, security controls, and overall risk mitigation. As the threat landscape continues to evolve, the importance of phishing simulations will only grow, ensuring that organizations are equipped to effectively counter the ever-present threat of phishing attacks.
FAQ Insights
What are the different types of phishing simulations?
Phishing simulations can be categorized into various types, including email phishing, SMS phishing, social media phishing, and voice phishing. Each type mimics a specific attack vector, allowing organizations to assess their vulnerability across multiple channels.
How often should phishing simulations be conducted?
The frequency of phishing simulations should be determined based on the organization’s risk profile and industry regulations. A good starting point is to conduct simulations at least quarterly, but more frequent simulations may be necessary for organizations with high-risk profiles or in industries with strict compliance requirements.
What should be done after a phishing simulation?
After a phishing simulation, it is essential to provide clear and timely feedback to employees. This feedback should include details about the simulation, the types of attacks used, and the results of the simulation. It is also important to provide employees with guidance on how to improve their security practices and to reinforce the importance of reporting suspicious emails or messages.
How can phishing simulations be made more effective?
To maximize the effectiveness of phishing simulations, organizations should ensure that the simulations are realistic, engaging, and relevant to the employees’ roles and responsibilities. They should also incorporate a variety of attack vectors and use different tactics to challenge employees’ security awareness.






