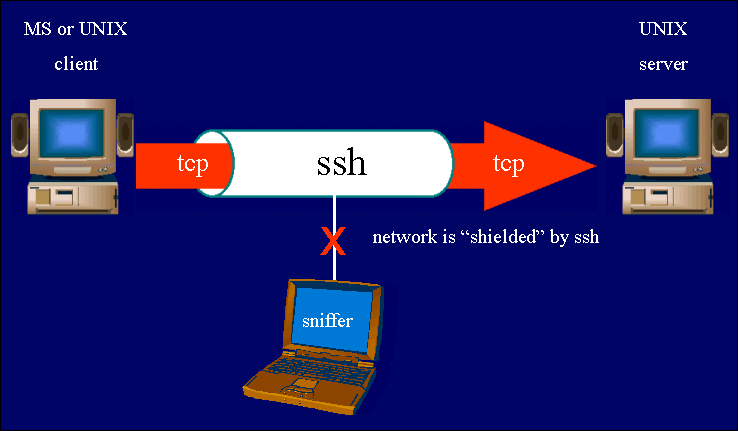
Which protocol adds security to remote connections – SSH, or Secure Shell, is the protocol that adds security to remote connections, establishing a secure channel for communication between devices. Imagine connecting to a server across the globe, accessing files, or running commands – all while ensuring your data remains protected from prying eyes. SSH encrypts all data exchanged, preventing eavesdropping and ensuring data integrity.
In a world where data breaches are commonplace, understanding the importance of secure remote connections is paramount. SSH, with its robust encryption and authentication mechanisms, has become the go-to protocol for secure remote access, empowering users to confidently navigate the digital landscape.
Introduction to Remote Connections and Security: Which Protocol Adds Security To Remote Connections
Remote connections allow users to access resources, applications, and data located on a different computer or network. This capability has revolutionized the way we work, learn, and interact with the digital world. Remote connections are a cornerstone of modern technology, enabling individuals and businesses to collaborate, access resources, and manage systems from anywhere in the world.The importance of security in remote connections cannot be overstated.
Remote connections are inherently vulnerable to various security threats, such as unauthorized access, data breaches, and malware infections. These vulnerabilities can have severe consequences, including financial losses, reputational damage, and legal repercussions.
Vulnerabilities in Unsecured Remote Connections
Unsecured remote connections present a wide range of vulnerabilities that malicious actors can exploit. Here are some common examples:
- Man-in-the-middle attacks: Attackers intercept communication between two parties, potentially stealing sensitive information or injecting malicious code.
- Credential theft: Attackers can capture usernames and passwords transmitted over unsecured connections.
- Data interception: Sensitive data, such as financial records, personal information, or confidential business documents, can be intercepted by attackers.
- Malware infection: Attackers can inject malicious software into remote systems through unsecured connections, compromising data and system security.
Common Remote Connection Protocols
Remote connection protocols are the backbone of modern computing, allowing users to access and manage systems from anywhere in the world. They offer a wide range of features and security levels, catering to diverse needs and applications. Understanding these protocols is crucial for ensuring secure and efficient remote access.
SSH (Secure Shell)
SSH is a widely used protocol that provides secure remote access to computer systems. It encrypts all communication between the client and server, making it highly secure against eavesdropping and data interception. SSH is commonly used for:
- Remote command execution: Users can execute commands on a remote server as if they were directly logged in.
- Secure file transfer: SSH’s SFTP (Secure File Transfer Protocol) allows users to securely transfer files between local and remote systems.
- Remote system administration: SSH provides a secure and reliable way to manage remote servers and other network devices.
SSH is a highly versatile protocol that is widely adopted in various industries, including web development, system administration, and cloud computing. Its strong security features make it a preferred choice for sensitive operations.
Telnet
Telnet is an older remote access protocol that transmits data in plain text. It lacks encryption, making it highly vulnerable to security risks. Telnet is generally considered insecure and should be avoided for sensitive operations.
- Legacy applications: Telnet might be used for legacy applications or devices that lack support for more secure protocols.
- Limited security: Telnet transmits data in plain text, making it susceptible to eavesdropping and data interception.
- Outdated technology: Telnet is considered an outdated protocol and is not recommended for modern use cases.
Due to its security vulnerabilities, Telnet is largely replaced by SSH in modern systems. It’s mainly used for compatibility with legacy applications or devices.
RDP (Remote Desktop Protocol)
RDP is a protocol developed by Microsoft that allows users to access and control a remote computer’s desktop. It provides a graphical interface and supports various features, including:
- Remote desktop access: Users can access and control a remote computer’s desktop as if they were physically sitting in front of it.
- Application sharing: RDP allows users to share and run applications on a remote computer.
- File transfer: Users can transfer files between their local computer and the remote system.
RDP is commonly used for remote administration, providing access to applications and resources on a remote computer. It is particularly popular for managing Windows-based systems.
Comparison of Remote Connection Protocols
| Protocol | Security | Features | Use Cases |
|---|---|---|---|
| SSH | Highly secure with encryption | Remote command execution, secure file transfer, remote system administration | System administration, web development, cloud computing |
| Telnet | Insecure, no encryption | Basic remote access | Legacy applications, compatibility with older devices |
| RDP | Secure with encryption, but vulnerabilities exist | Remote desktop access, application sharing, file transfer | Remote administration, accessing Windows-based systems |
Choosing the right remote connection protocol depends on the specific security requirements, desired features, and compatibility with the target system. SSH is generally the preferred choice for secure remote access, while RDP provides a graphical interface for managing Windows systems. Telnet is generally avoided due to its security vulnerabilities.
Secure Remote Connection Protocols
In the realm of remote connections, security is paramount. To safeguard sensitive data during transmission, specialized protocols have emerged, employing robust encryption and authentication mechanisms. These protocols ensure that only authorized individuals can access the data, while protecting it from unauthorized interception and manipulation.
Secure Shell (SSH)
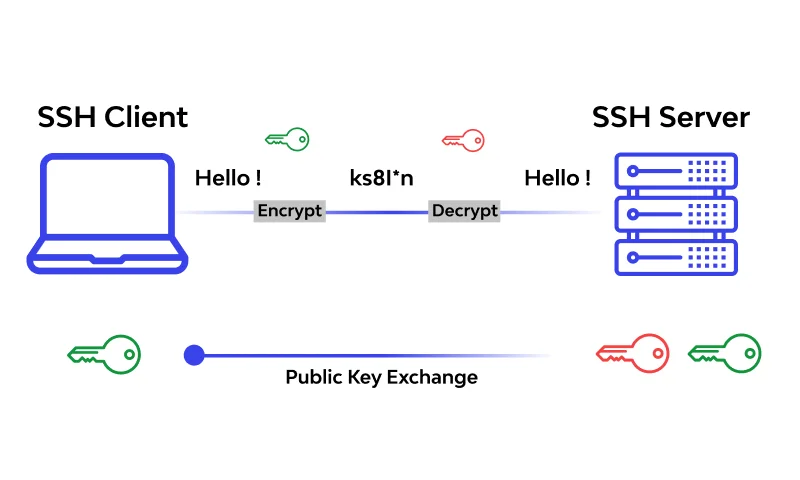
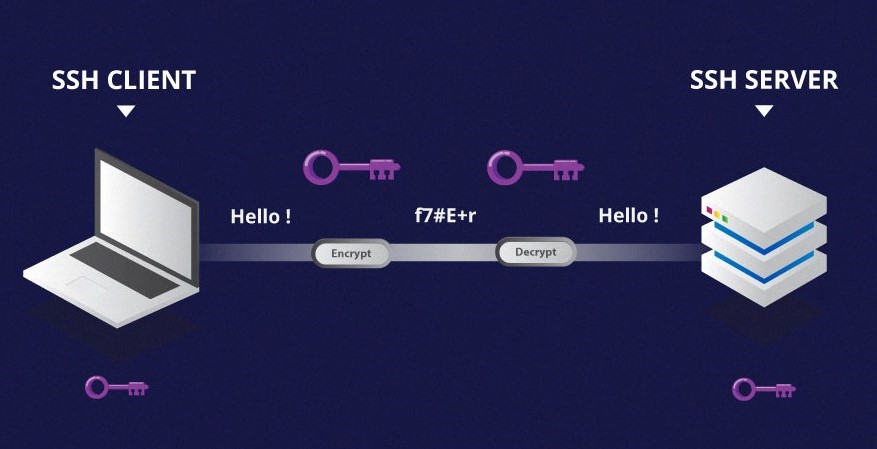
SSH is a widely used protocol for secure remote login and data transfer. It provides a secure channel for communication between a client and a server, employing cryptographic algorithms to encrypt all data transmitted. SSH leverages public-key cryptography for authentication, allowing users to securely connect to remote servers without sharing their passwords.
SSH utilizes a combination of symmetric and asymmetric encryption to ensure data confidentiality and integrity.
Hypertext Transfer Protocol Secure (HTTPS)
HTTPS is a secure version of the HTTP protocol, commonly used for web browsing. It uses Transport Layer Security (TLS) or Secure Sockets Layer (SSL) to encrypt communication between a web browser and a web server. This encryption ensures that sensitive data, such as login credentials and credit card information, is protected from eavesdropping and tampering.
HTTPS utilizes a combination of symmetric and asymmetric encryption to ensure data confidentiality and integrity.
Secure Copy Protocol (SCP)
SCP is a secure file transfer protocol that builds upon the SSH protocol. It allows users to securely copy files between a client and a server, ensuring that the data is encrypted during transmission. SCP leverages the authentication and encryption mechanisms of SSH, providing a secure and reliable method for transferring files.
SCP utilizes the same security mechanisms as SSH, ensuring secure file transfer.
Secure File Transfer Protocol (SFTP)
SFTP is another secure file transfer protocol that leverages the SSH protocol. It provides a secure and reliable method for transferring files, offering features such as file browsing, directory manipulation, and file permissions management. SFTP uses the same encryption and authentication mechanisms as SSH, ensuring secure file transfer.
SFTP utilizes the same security mechanisms as SSH, ensuring secure file transfer.
Key Concepts in Secure Remote Connections
Secure remote connections rely on a foundation of cryptographic techniques and security principles to ensure the confidentiality, integrity, and authenticity of data transmitted over networks. These key concepts underpin the robustness and trustworthiness of secure protocols.
Encryption, Which protocol adds security to remote connections
Encryption is the process of transforming data into an unreadable format, called ciphertext, using an algorithm and a key. Only individuals with the correct decryption key can access the original data.
Encryption protects data from unauthorized access during transmission, ensuring confidentiality.
For example, in HTTPS (Hypertext Transfer Protocol Secure), the data exchanged between a web browser and a website is encrypted using TLS (Transport Layer Security) or SSL (Secure Sockets Layer) protocols.
Authentication
Authentication verifies the identity of the parties involved in a remote connection. It ensures that the communicating entities are who they claim to be.
Authentication helps prevent impersonation and unauthorized access.
Examples of authentication methods include:
- Password-based authentication: Users provide a username and password to verify their identity.
- Public key infrastructure (PKI): Digital certificates issued by trusted authorities bind public keys to entities, enabling verification of identity.
- Multi-factor authentication (MFA): Requires users to provide multiple forms of authentication, such as a password and a one-time code generated by a mobile app.
Authorization
Authorization determines what actions a user or entity is permitted to perform after authentication. It grants access to specific resources or functionalities based on predefined rules and permissions.
Authorization controls access to sensitive data and prevents unauthorized actions.
For instance, in a secure remote access system, authorized users might have access to specific folders or applications, while others might be restricted.
Key Exchange
Key exchange protocols enable secure sharing of cryptographic keys between parties without compromising their confidentiality.
Secure key exchange ensures that keys are not intercepted or compromised during transmission.
Examples of key exchange protocols include:
- Diffie-Hellman key exchange: A widely used algorithm for generating a shared secret key between two parties over an insecure channel.
- Elliptic curve cryptography (ECC): An alternative to traditional public-key cryptography that offers improved efficiency and security for key exchange.
Digital Signatures
Digital signatures are cryptographic mechanisms that provide authentication and integrity verification for digital documents or messages. They use a private key to generate a unique signature, which can be verified using the corresponding public key.
Digital signatures ensure the authenticity and integrity of data, preventing tampering and forgery.
For example, digital signatures are used in secure email communication to verify the sender’s identity and ensure that the message hasn’t been altered during transmission.
Comparing Secure Remote Connection Protocols
The world of secure remote connections is filled with a variety of protocols, each with its own strengths and weaknesses. Understanding the differences between these protocols is crucial for choosing the best one for your specific needs.
Comparison of Secure Remote Connection Protocols
Comparing the security features of different protocols is essential for selecting the most appropriate one for a particular scenario. Here’s a breakdown of the key features and strengths of SSH and HTTPS:
| Feature | SSH | HTTPS |
|---|---|---|
| Authentication | Strong authentication methods, including public-key cryptography, passwords, and multi-factor authentication | Typically uses certificate-based authentication, relying on trusted certificate authorities |
| Encryption | Provides strong encryption for both data and control information, ensuring confidentiality and integrity | Uses TLS/SSL encryption, ensuring secure communication over the internet |
| Data Integrity | Uses cryptographic hashing to verify data integrity, preventing unauthorized modifications | Employs digital signatures and hashing to guarantee data integrity |
| Protocol Flexibility | Offers a wide range of functionalities, including remote command execution, file transfer, and port forwarding | Primarily designed for secure web communication, but can be used for other applications |
| Performance | Can be slightly slower than HTTPS due to the overhead of encryption and authentication | Generally faster than SSH, particularly for web traffic |
| Complexity | Can be more complex to configure and manage, especially for advanced features | Simpler to implement and use, particularly for web-based applications |
Advantages and Disadvantages of Different Protocols
Choosing the right protocol depends on the specific requirements of the connection. Let’s examine the advantages and disadvantages of SSH and HTTPS in different scenarios:
SSH
Advantages
- Provides robust security for remote access and management, including secure shell access and file transfer.
- Offers a wider range of functionalities, enabling tasks like remote command execution and port forwarding.
- Ideal for scenarios requiring strong authentication and data integrity, such as accessing sensitive servers or managing critical infrastructure.
Disadvantages
- Can be more complex to set up and manage compared to HTTPS.
- May be slower than HTTPS due to the overhead of encryption and authentication.
- Not as widely supported as HTTPS for web-based applications.
HTTPS
Advantages
- Widely supported by web browsers and applications, making it suitable for secure web communication.
- Generally faster than SSH, especially for web traffic.
- Simpler to implement and use, making it a good choice for web-based applications and services.
Disadvantages
Best Practices for Secure Remote Connections
Securing remote connections is crucial for protecting sensitive data and ensuring the integrity of your systems. Implementing best practices can significantly enhance the security of your remote connections and mitigate potential risks.
Strong Passwords and Authentication Methods
Strong passwords are fundamental for secure remote connections. Employing robust authentication methods further strengthens the security of your remote access.
- Use strong passwords: A strong password should be at least 12 characters long, include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable words or personal information.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security by requiring users to provide two or more forms of authentication. This can include a password, a one-time code from a mobile app, or a biometric scan.
- Avoid using the same password for multiple accounts: Using the same password for different accounts can compromise all accounts if one password is compromised.
- Implement password managers: Password managers can help you generate and store strong passwords for all your accounts, making it easier to manage and remember them.
Regularly Updating Software and Security Patches
Keeping your software up-to-date is essential for mitigating security vulnerabilities. Regular updates include security patches that fix known weaknesses in software, making your systems less susceptible to attacks.
- Enable automatic updates: Configure your devices and software to automatically install updates as they become available.
- Install updates promptly: Do not delay installing updates, as they can patch critical security vulnerabilities.
- Stay informed about security threats: Keep yourself informed about the latest security threats and vulnerabilities.
Secure Connection Configuration
Properly configuring your secure remote connection protocols is crucial for ensuring secure communication.
- Use strong encryption: Choose the highest level of encryption supported by your protocol.
- Enable authentication: Ensure that your remote connection protocol requires authentication to prevent unauthorized access.
- Limit access: Configure your remote connection to only allow access from authorized devices and users.
- Use a secure VPN: Consider using a Virtual Private Network (VPN) to encrypt your traffic and mask your IP address.
Best Practices for Secure Remote Connections
- Use a secure connection: Always use a secure connection (HTTPS) when accessing remote systems.
- Be cautious of suspicious links: Do not click on suspicious links in emails or messages.
- Be aware of phishing attacks: Phishing attacks attempt to trick users into revealing sensitive information.
- Use a strong antivirus: Install and maintain a reputable antivirus program on all your devices.
- Keep your operating system and software up-to-date: Install security updates and patches as soon as they are available.
- Be aware of your surroundings: Be mindful of your surroundings when accessing sensitive information from a public location.
Security Threats to Remote Connections
Remote connections, while offering convenience and flexibility, also introduce vulnerabilities that malicious actors can exploit to compromise data and system security. Understanding these threats is crucial to implementing effective mitigation strategies and safeguarding your network and sensitive information.
Man-in-the-Middle Attacks
Man-in-the-middle (MitM) attacks are a significant threat to remote connections. In a MitM attack, an attacker intercepts the communication between two parties, such as a client and a server, without either party’s knowledge. The attacker can then eavesdrop on the communication, modify the data being exchanged, or even impersonate one of the parties.
How MitM Attacks Work
- The attacker establishes a connection with both the client and the server, acting as a proxy between them.
- The attacker intercepts all data sent between the client and server, potentially modifying it before forwarding it to the intended recipient.
- The attacker can use this intercepted data to steal sensitive information, such as login credentials, credit card details, or confidential documents.
Mitigation Strategies
- Use Strong Encryption: Employing strong encryption protocols, such as TLS/SSL, ensures that data is scrambled during transmission, making it unreadable to attackers.
- Verify Digital Certificates: Ensure that the website or server you are connecting to has a valid digital certificate issued by a trusted Certificate Authority (CA). This verifies the identity of the server and helps prevent MitM attacks.
- Use VPNs: Virtual Private Networks (VPNs) encrypt all traffic passing through them, making it difficult for attackers to intercept and decrypt data.
Brute-Force Attacks
Brute-force attacks involve systematically trying different combinations of usernames and passwords until the correct one is found. These attacks can be automated and can target remote access services, such as SSH or RDP.
How Brute-Force Attacks Work
- Attackers use automated scripts to try a large number of possible password combinations.
- They can target weak passwords or accounts with predictable usernames and passwords.
- Successful brute-force attacks grant attackers access to the system, allowing them to steal data, install malware, or launch further attacks.
Mitigation Strategies
- Use Strong Passwords: Employ complex passwords with a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using common words or personal information.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide more than one piece of identification, such as a password and a code from a mobile device.
- Implement Account Lockouts: Configure account lockout policies to automatically lock out accounts after a certain number of failed login attempts.
- Use Password Managers: Password managers securely store and manage your passwords, reducing the risk of using weak or reused passwords.
Future Trends in Secure Remote Connections
The landscape of secure remote connections is constantly evolving, driven by technological advancements and the changing demands of a globalized and increasingly digital world. Emerging trends are shaping the future of remote connection security, promising enhanced protection, improved usability, and new opportunities for collaboration.
The Rise of Zero Trust Security
Zero trust security is a fundamental shift in security philosophy that assumes no user or device can be trusted by default. This approach emphasizes continuous verification and authentication, enforcing strict access controls based on real-time risk assessments. In the context of remote connections, zero trust principles will play a crucial role in securing remote access, preventing unauthorized access, and mitigating the risks associated with remote work.
- Multi-factor authentication (MFA): Zero trust architectures rely heavily on MFA, requiring users to provide multiple forms of authentication before granting access. This can include passwords, biometrics, or one-time codes, significantly enhancing security by making it more difficult for attackers to gain unauthorized access.
- Contextual access control: Access decisions are based on factors such as user identity, device location, network conditions, and time of day. This dynamic approach helps ensure that only authorized users can access the appropriate resources from trusted locations, reducing the risk of unauthorized access.
- Continuous monitoring and threat detection: Zero trust environments continuously monitor user activity and network traffic, detecting and responding to potential threats in real-time. This proactive approach helps identify and mitigate security vulnerabilities before they can be exploited.
As we delve deeper into the realm of secure remote connections, SSH emerges as the champion, offering a robust and reliable solution. Its ability to encrypt data, authenticate users, and maintain data integrity makes it an indispensable tool for anyone who values secure remote access. Whether you’re a system administrator, developer, or simply someone who needs to connect to remote resources, SSH provides the peace of mind knowing your data is safe.
FAQ Insights
What are the main benefits of using SSH?
SSH offers several key benefits, including:
- Strong encryption to protect data during transmission.
- Secure authentication to verify user identities.
- Ability to tunnel other protocols over SSH for added security.
- Widely supported across various operating systems and platforms.
How does SSH encryption work?
SSH utilizes public-key cryptography. The server generates a public and private key pair. The public key is shared with clients, while the private key remains secure on the server. When a client connects, the server uses the client’s public key to authenticate them, and the client uses the server’s public key to encrypt data. Only the server’s private key can decrypt the data, ensuring secure communication.
What are some common use cases for SSH?
SSH is widely used for:
- Remotely managing servers and devices.
- Transferring files securely between systems.
- Running commands on remote servers.
- Securing web traffic using SSH tunnels.






