A Category IV security risk represents a significant threat to an organization’s operations, reputation, and financial stability. These risks, often characterized by their potential for widespread disruption and severe consequences, demand a comprehensive and proactive approach to mitigation. Understanding the nature of these risks, identifying potential vulnerabilities, and implementing robust security measures are essential for safeguarding sensitive data, protecting critical systems, and ensuring business continuity.
Category IV risks can manifest in various forms, ranging from sophisticated cyberattacks targeting critical infrastructure to data breaches exposing sensitive customer information. The impact of such incidents can be devastating, leading to financial losses, reputational damage, legal liabilities, and even loss of life. Therefore, organizations must prioritize the identification, assessment, and mitigation of these risks to minimize their exposure and ensure their resilience in the face of adversity.
Understanding Category IV Security Risks
Category IV security risks are the most severe type of risk in information security frameworks, representing threats with a high likelihood of occurrence and a significant potential impact on an organization’s operations, reputation, and financial stability. These risks demand immediate attention and proactive mitigation strategies to prevent catastrophic consequences.
Real-World Scenarios Illustrating Category IV Risks
The severity of Category IV risks is best understood through real-world scenarios. These risks are often associated with:
- Data Breaches: A major data breach, involving the theft of sensitive information such as customer data, financial records, or intellectual property, can lead to significant financial losses, reputational damage, legal penalties, and loss of customer trust. For example, the Equifax data breach in 2017 compromised the personal information of over 147 million individuals, resulting in billions of dollars in fines and settlements, and severe reputational damage for the credit reporting agency.
- System Failures: Critical system failures, such as a power outage or a major software malfunction, can disrupt business operations, causing significant financial losses and impacting customer service. For example, the 2019 power outage in New York City affected major financial institutions and businesses, resulting in billions of dollars in losses and causing significant disruptions in the city’s economy.
- Cyberattacks: Advanced persistent threats (APTs), ransomware attacks, and distributed denial-of-service (DDoS) attacks can cripple an organization’s infrastructure, disrupt critical operations, and cause significant financial losses. For example, the NotPetya ransomware attack in 2017 affected businesses worldwide, causing billions of dollars in damage and disrupting operations for months.
- Natural Disasters: Natural disasters such as earthquakes, floods, or hurricanes can cause significant damage to an organization’s infrastructure, disrupting operations and leading to financial losses. For example, Hurricane Katrina in 2005 caused widespread damage to businesses in New Orleans, resulting in billions of dollars in losses and disrupting operations for years.
Identifying Category IV Risks

Identifying and assessing Category IV security risks is a critical step in safeguarding sensitive data and systems. These risks are complex and can have far-reaching consequences, making it crucial to employ a multi-faceted approach to their identification and mitigation.
Risk Assessment Tools and Techniques
A variety of tools and techniques can be used to identify and assess Category IV security risks. These tools and techniques help organizations systematically evaluate their security posture and prioritize mitigation efforts.
- Vulnerability Scanning: This process involves using automated tools to scan systems and applications for known vulnerabilities. Vulnerability scanners can identify weaknesses that could be exploited by attackers, including those related to Category IV risks.
- Threat Modeling: Threat modeling is a structured process for identifying potential threats and vulnerabilities within a system or application. This technique helps organizations understand the potential impact of different attack scenarios, including those related to Category IV risks.
- Risk Assessment Frameworks: Several established risk assessment frameworks provide a standardized approach to identifying and assessing risks. These frameworks often include specific guidance for evaluating Category IV risks, such as the NIST Cybersecurity Framework (CSF) and the ISO 27001 standard.
Examples of Risk Assessment Tools
Several risk assessment tools are available to help organizations identify and assess Category IV security risks. These tools often combine automated scanning capabilities with expert analysis to provide a comprehensive assessment of an organization’s security posture.
- Nessus: Nessus is a popular vulnerability scanner that can identify a wide range of vulnerabilities, including those related to Category IV risks. Nessus provides detailed reports and remediation recommendations, helping organizations prioritize their security efforts.
- QualysGuard: QualysGuard is another comprehensive vulnerability management platform that offers vulnerability scanning, asset discovery, and compliance reporting. QualysGuard can help organizations identify and manage Category IV risks across their entire IT infrastructure.
- IBM Security AppScan: IBM Security AppScan is a web application security testing tool that can identify vulnerabilities in web applications, including those related to Category IV risks. AppScan provides a detailed analysis of potential vulnerabilities and recommendations for remediation.
Regular Risk Assessments
Regular risk assessments are essential for identifying emerging Category IV threats and ensuring that an organization’s security controls remain effective. As technology evolves and threat actors develop new attack methods, organizations must adapt their security posture to stay ahead of emerging risks.
- Continuous Monitoring: Continuous monitoring involves collecting and analyzing security data in real-time to detect and respond to threats as they emerge. This approach is particularly important for identifying and mitigating Category IV risks, which often involve sophisticated attacks that can be difficult to detect using traditional methods.
- Threat Intelligence: Threat intelligence involves gathering information about current and emerging threats from various sources, including security vendors, government agencies, and industry groups. By staying informed about the latest threats, organizations can better identify and mitigate Category IV risks.
- Security Awareness Training: Security awareness training helps employees understand their role in protecting sensitive data and systems. This training can help reduce the risk of human error, which can be a significant factor in Category IV incidents.
Mitigating Category IV Risks: A Category Iv Security Risk
Category IV security risks are a serious threat to any organization, with the potential to cause significant financial losses, reputational damage, and even legal repercussions. Fortunately, there are a number of strategies that can be employed to mitigate these risks, both proactively and reactively.
Preventative Measures
Preventative measures aim to reduce the likelihood of Category IV risks materializing in the first place. These measures can include:
- Strong Access Control: Implementing robust access control mechanisms is crucial. This involves using multi-factor authentication, restricting access to sensitive data based on the principle of least privilege, and regularly reviewing and updating access permissions. For example, a hospital could implement strong access control measures for patient medical records, ensuring only authorized personnel have access.
- Data Encryption: Encrypting sensitive data at rest and in transit significantly reduces the risk of unauthorized access or data breaches. This can involve encrypting databases, files, and communication channels. For example, a financial institution could encrypt customer financial data stored in its databases to protect against unauthorized access.
- Security Awareness Training: Educating employees about security best practices and common threats can significantly reduce the likelihood of human error or social engineering attacks. Training should cover topics like phishing, malware, and password security. For example, a company could conduct regular security awareness training for employees to help them identify and avoid phishing emails.
- Regular Security Audits: Conducting regular security audits helps identify vulnerabilities and weaknesses in security systems and processes. Audits should cover both technical and non-technical aspects of security, and should be performed by qualified professionals. For example, a software company could conduct regular security audits of its software development processes to identify potential vulnerabilities.
- Vulnerability Management: Proactively identifying and patching vulnerabilities in software and hardware is essential to prevent attackers from exploiting them. This involves using vulnerability scanners, maintaining up-to-date software patches, and following a well-defined vulnerability management process. For example, a university could implement a vulnerability management program to regularly scan its network and systems for vulnerabilities and promptly patch them.
Reactive Measures
Reactive measures focus on minimizing the impact of a Category IV risk if it does occur. These measures can include:
- Incident Response Plan: Having a well-defined incident response plan is critical for effectively responding to security incidents. The plan should Artikel the steps to be taken in the event of a breach, including containment, investigation, and recovery. For example, a retail company could have an incident response plan in place to deal with a data breach, outlining steps for notifying customers, containing the breach, and recovering lost data.
- Data Backup and Recovery: Regular backups of critical data and systems are essential for quickly restoring operations in the event of a disaster or data loss. Backups should be stored securely and tested regularly to ensure their effectiveness. For example, a financial services company could have a robust data backup and recovery plan in place to ensure business continuity in the event of a ransomware attack.
- Business Continuity and Disaster Recovery: Implementing business continuity and disaster recovery plans ensures that critical business functions can continue to operate even in the face of major disruptions. These plans should include strategies for restoring operations, communicating with stakeholders, and mitigating financial losses. For example, a manufacturing company could have a business continuity plan in place to ensure production can continue even if a natural disaster disrupts its main facility.
- Forensics and Investigation: In the event of a security incident, it is essential to conduct a thorough investigation to determine the root cause, the extent of the damage, and the potential impact on the organization. This involves using forensic tools and techniques to collect and analyze evidence. For example, a law firm could engage a forensic investigation team to investigate a data breach and identify the source of the attack.
- Legal and Regulatory Compliance: Organizations must comply with relevant legal and regulatory requirements regarding data security and privacy. This includes following industry standards and best practices, and reporting security incidents to the appropriate authorities. For example, a healthcare provider must comply with HIPAA regulations regarding the protection of patient health information.
Mitigation Strategies for Common Category IV Risks
| Risk | Potential Impact | Mitigation Strategies ||——————————————-|———————————————-|————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————————–|| Data Breaches | Loss of sensitive data, financial losses, reputational damage, legal repercussions | Strong access control: Restrict access to sensitive data based on the principle of least privilege, use multi-factor authentication, and regularly review and update access permissions.
Data encryption: Encrypt data at rest and in transit. Security awareness training: Educate employees about security best practices and common threats. Vulnerability management: Proactively identify and patch vulnerabilities in software and hardware. Incident response plan: Have a plan in place to respond to data breaches effectively. Data backup and recovery: Regularly back up critical data and systems to ensure quick recovery.
|| Ransomware Attacks | Data encryption, system downtime, financial losses, reputational damage | Strong access control: Restrict access to sensitive data and systems.
Data encryption: Encrypt data at rest and in transit. Security awareness training: Educate employees about ransomware attacks and how to avoid them. Vulnerability management: Proactively identify and patch vulnerabilities in software and hardware. Data backup and recovery: Regularly back up critical data and systems to ensure quick recovery. Incident response plan: Have a plan in place to respond to ransomware attacks effectively.
Business continuity and disaster recovery: Implement plans to ensure business continuity in the event of a ransomware attack. || Denial of Service (DoS) Attacks | Website downtime, business disruption, financial losses | Network security: Implement firewalls, intrusion detection systems, and other network security measures to prevent DoS attacks.
Load balancing: Distribute traffic across multiple servers to prevent a single server from being overwhelmed. DDoS mitigation services: Use specialized services to protect against large-scale DoS attacks. Incident response plan: Have a plan in place to respond to DoS attacks effectively. || Malware Infections | Data theft, system damage, business disruption, financial losses | Strong access control: Restrict access to sensitive data and systems.
Antivirus software: Install and maintain up-to-date antivirus software on all devices. Security awareness training: Educate employees about malware and how to avoid it. Vulnerability management: Proactively identify and patch vulnerabilities in software and hardware. Incident response plan: Have a plan in place to respond to malware infections effectively. Data backup and recovery: Regularly back up critical data and systems to ensure quick recovery.
|| Insider Threats | Data theft, sabotage, reputational damage, legal repercussions | Strong access control: Restrict access to sensitive data and systems based on the principle of least privilege.
Security awareness training: Educate employees about the importance of data security and the consequences of insider threats. Background checks: Conduct thorough background checks on all employees, especially those with access to sensitive data. Data loss prevention (DLP) solutions: Implement DLP solutions to monitor and prevent sensitive data from leaving the organization. Incident response plan: Have a plan in place to respond to insider threats effectively.
|| Social Engineering Attacks | Data theft, system compromise, financial losses, reputational damage | Security awareness training: Educate employees about social engineering attacks and how to avoid them.
Strong access control: Restrict access to sensitive data and systems. Multi-factor authentication: Implement multi-factor authentication to prevent unauthorized access. Incident response plan: Have a plan in place to respond to social engineering attacks effectively. || Supply Chain Attacks | Data theft, system compromise, financial losses, reputational damage | Vendor security assessments: Conduct thorough security assessments of all vendors, especially those with access to sensitive data or systems.
Secure software development practices: Implement secure software development practices to reduce the risk of vulnerabilities in software used by the organization. Incident response plan: Have a plan in place to respond to supply chain attacks effectively. || Physical Security Breaches | Data theft, system damage, business disruption, financial losses | Physical security controls: Implement physical security controls, such as access control systems, surveillance cameras, and security guards, to protect data centers and other sensitive locations.
Data encryption: Encrypt data at rest and in transit to protect against physical theft. Incident response plan: Have a plan in place to respond to physical security breaches effectively. |
Responding to Category IV Security Incidents
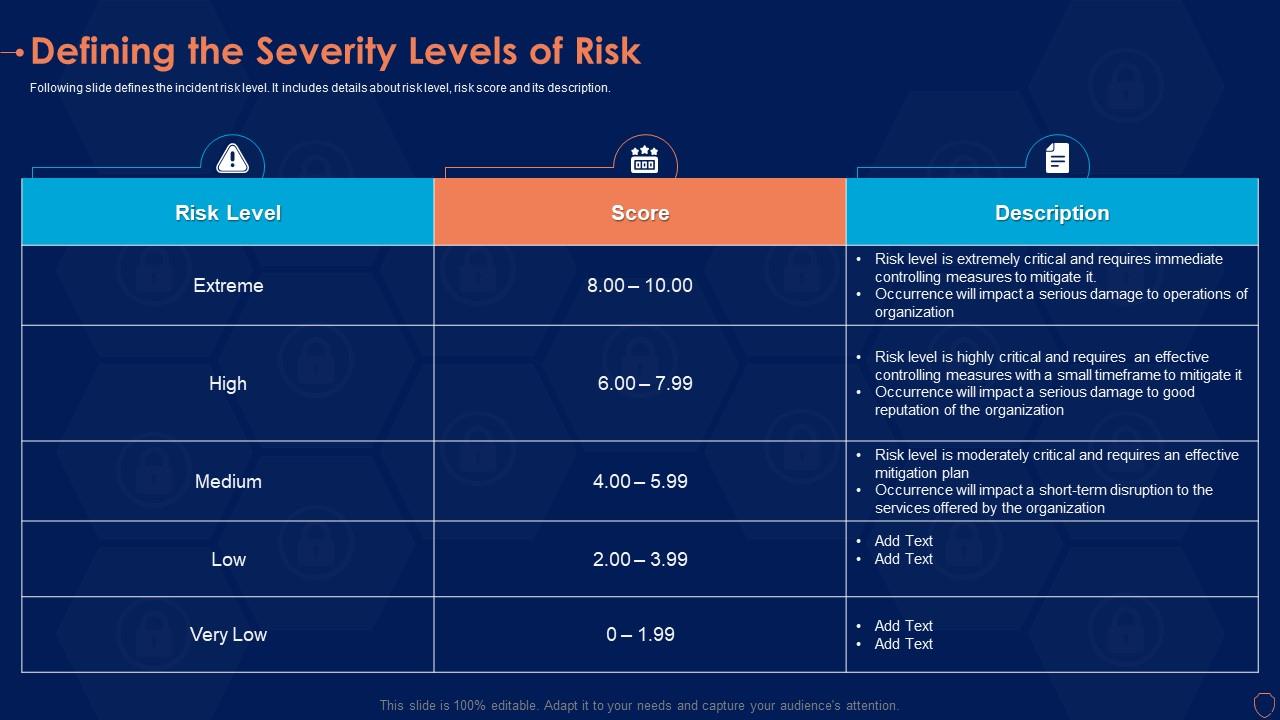
Category IV security incidents, due to their potential for significant impact, demand a structured and rapid response. These incidents require the mobilization of specialized resources and expertise to minimize damage and restore normalcy.
Incident Response Process, A category iv security risk
A well-defined incident response process is crucial for effectively handling Category IV security incidents. The following flowchart Artikels the key steps involved:
Incident Detection: This stage involves the identification of the incident, often through automated security systems, user reports, or system anomalies. Incident Analysis: Once an incident is detected, the next step is to analyze its nature, scope, and potential impact. This includes determining the affected systems, data, and individuals. Containment: Containment aims to limit the spread of the incident and prevent further damage.
This may involve isolating infected systems, blocking network traffic, or disabling compromised accounts. Eradication: This stage involves removing the root cause of the incident, such as malware, unauthorized access, or configuration errors. Recovery: The recovery phase focuses on restoring affected systems and data to their pre-incident state. This may involve data recovery, system reconfiguration, and security hardening. Post-Incident Analysis: The final step involves analyzing the incident to identify weaknesses in security controls and implement corrective measures.
This helps to prevent similar incidents from occurring in the future.
Incident Documentation
Detailed incident documentation is essential for several reasons:
- Provides a historical record of the incident, including timelines, actions taken, and outcomes.
- Facilitates post-incident analysis and identification of root causes.
- Supports legal and regulatory compliance requirements.
- Provides valuable insights for improving security controls and incident response procedures.
Post-Incident Analysis
Post-incident analysis involves a thorough review of the incident to identify weaknesses in security controls and implement corrective measures. This analysis typically includes:
- Reviewing incident logs and security monitoring data.
- Analyzing the attacker’s tactics, techniques, and procedures (TTPs).
- Identifying vulnerabilities exploited by the attacker.
- Evaluating the effectiveness of existing security controls.
- Developing recommendations for improving security posture.
Post-incident analysis is a crucial step in the incident response process, as it helps to prevent similar incidents from occurring in the future. By learning from past incidents, organizations can strengthen their security posture and better protect themselves from future threats.
Best Practices for Category IV Risk Management

Category IV risks are the most severe and pose the greatest threat to an organization’s security, operations, and reputation. Effective management of these risks requires a comprehensive and proactive approach that involves all levels of the organization.
Key Considerations for a Comprehensive Category IV Risk Management Program
Developing a robust Category IV risk management program requires careful consideration of various factors. This program should be designed to identify, assess, mitigate, and respond to these high-impact risks effectively.
- Establish a Clear Risk Management Framework: A well-defined framework provides a structured approach to risk management, ensuring consistency and accountability throughout the organization. This framework should Artikel roles, responsibilities, processes, and procedures for managing Category IV risks.
- Identify and Prioritize Category IV Risks: Organizations must proactively identify potential Category IV risks by conducting comprehensive threat assessments, reviewing past incidents, and staying informed about emerging threats. Prioritizing these risks based on their likelihood and impact is crucial to allocating resources effectively.
- Implement Robust Mitigation Strategies: Effective mitigation strategies are essential to reduce the likelihood and impact of Category IV risks. These strategies may include implementing advanced security controls, enhancing incident response capabilities, and conducting regular security audits.
- Foster a Culture of Security Awareness: A strong security culture is fundamental to successful Category IV risk management. This culture should encourage employees to report suspicious activities, follow security protocols, and stay informed about potential threats.
- Develop a Comprehensive Incident Response Plan: A well-defined incident response plan is critical for handling Category IV security incidents effectively. This plan should Artikel procedures for containing the incident, mitigating its impact, and recovering from the event.
- Conduct Regular Risk Assessments: Regularly assessing Category IV risks is essential to identify emerging threats, evaluate the effectiveness of mitigation strategies, and adapt to changing circumstances. These assessments should involve a comprehensive review of the organization’s security posture and threat landscape.
- Maintain Strong Communication and Collaboration: Effective communication and collaboration are essential for successful Category IV risk management. This includes sharing information about threats and vulnerabilities, coordinating response efforts, and maintaining transparency with stakeholders.
Examples of Successful Category IV Risk Management Strategies
Numerous organizations have implemented successful strategies for managing Category IV risks. Here are some examples:
- Financial Institutions: Banks and other financial institutions often face significant Category IV risks related to fraud, cyberattacks, and data breaches. They employ sophisticated security technologies, such as multi-factor authentication, encryption, and intrusion detection systems, to mitigate these risks. They also invest heavily in employee training and awareness programs to enhance their security posture.
- Healthcare Organizations: Healthcare organizations are particularly vulnerable to Category IV risks, given the sensitive nature of patient data. They prioritize data security by implementing robust access controls, encryption, and data loss prevention technologies. They also conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
- Government Agencies: Government agencies are often targeted by sophisticated cyberattacks due to the critical nature of their data and operations. They implement advanced security measures, including network segmentation, threat intelligence sharing, and incident response capabilities, to mitigate these risks. They also work closely with cybersecurity experts and intelligence agencies to stay ahead of emerging threats.
Effectively managing Category IV security risks requires a multi-layered approach that encompasses proactive prevention, robust detection mechanisms, and swift incident response capabilities. By implementing a comprehensive risk management framework, organizations can significantly reduce their vulnerability to high-impact threats, safeguarding their assets, protecting their reputation, and ensuring the long-term sustainability of their operations.
Essential Questionnaire
What are some common examples of Category IV security risks?
Common examples include:
- Large-scale data breaches exposing sensitive customer information
- Distributed denial-of-service (DDoS) attacks targeting critical infrastructure
- Malware infections disrupting business operations
- Insider threats compromising sensitive data
- Advanced persistent threats (APTs) targeting sensitive data and systems
How can I identify and assess Category IV risks within my organization?
You can use a variety of methods for identifying and assessing Category IV risks, including:
- Threat modeling: This technique involves identifying potential threats and vulnerabilities within your organization’s systems and data.
- Vulnerability scanning: Automated tools can scan your systems for known vulnerabilities and weaknesses.
- Penetration testing: Ethical hackers simulate real-world attacks to identify security weaknesses.
- Risk assessment frameworks: Frameworks like NIST Cybersecurity Framework and ISO 27001 provide guidance on identifying and managing risks.
What are some effective mitigation strategies for Category IV risks?
Effective mitigation strategies include:
- Implementing strong access controls and authentication mechanisms
- Deploying intrusion detection and prevention systems
- Regularly patching vulnerabilities and updating software
- Educating employees on security best practices and phishing awareness
- Developing and testing incident response plans






