Is cyber security a trade? This question resonates deeply in today’s digital age, where the lines between physical and virtual worlds blur. The answer, undeniably, is a resounding yes. Cybersecurity has evolved from a niche field into a vital pillar of our interconnected world, demanding a dedicated workforce to protect our digital lives and assets. This journey delves into the multifaceted world of cyber security, exploring its evolution, the surging demand for skilled professionals, the diverse educational pathways, and the profound economic and ethical implications that shape its landscape.
From the early days of hacking to the sophisticated cyberattacks of today, the threat landscape has continuously evolved. Technological advancements have brought about new opportunities but also introduced vulnerabilities that cybercriminals exploit. This has led to a global demand for cybersecurity professionals who can navigate the intricate world of digital security and safeguard our data, infrastructure, and privacy.
The Evolution of Cybersecurity

Cybersecurity has evolved significantly since its inception, driven by technological advancements and the ever-changing landscape of cyber threats. From its early days of protecting physical systems to today’s complex digital defenses, cybersecurity has become a critical component of modern society.
Early Days of Cybersecurity
The early days of cybersecurity were primarily focused on protecting physical systems from unauthorized access. The first computer viruses emerged in the 1970s, and the development of the internet in the 1980s brought new challenges to cybersecurity. The early 1990s saw the rise of hacking groups, which targeted computer systems for malicious purposes. These early threats were relatively simple compared to the sophisticated cyberattacks we see today.
The Rise of Sophisticated Cyberattacks
The nature of cyber threats has evolved dramatically over time. Early attacks were often opportunistic, targeting vulnerabilities in systems for personal gain. However, as technology advanced, so did the sophistication of cyberattacks. Organized crime groups, nation-states, and other actors began to leverage cyberattacks for financial gain, espionage, and other malicious purposes.
The Impact of Technological Advancements
Technological advancements have had a profound impact on the cybersecurity landscape. The widespread adoption of cloud computing, mobile devices, and the Internet of Things (IoT) has created new attack surfaces for cybercriminals. The increasing interconnectedness of our digital world has also made it easier for attackers to spread malware and launch large-scale cyberattacks.
Key Milestones and Events
- 1971: The first computer virus, known as the “Creeper virus,” was created. This virus was designed to replicate itself on computers and spread to other systems.
- 1980s: The development of the internet led to a significant increase in cyber threats. Hackers began to exploit vulnerabilities in internet-connected systems.
- 1990s: The rise of organized crime groups and nation-state actors using cyberattacks for financial gain and espionage.
- 2000s: The emergence of sophisticated malware, such as worms, trojans, and ransomware, which targeted individuals and organizations.
- 2010s: The widespread adoption of cloud computing, mobile devices, and the Internet of Things (IoT) created new attack surfaces for cybercriminals.
The Demand for Cybersecurity Professionals
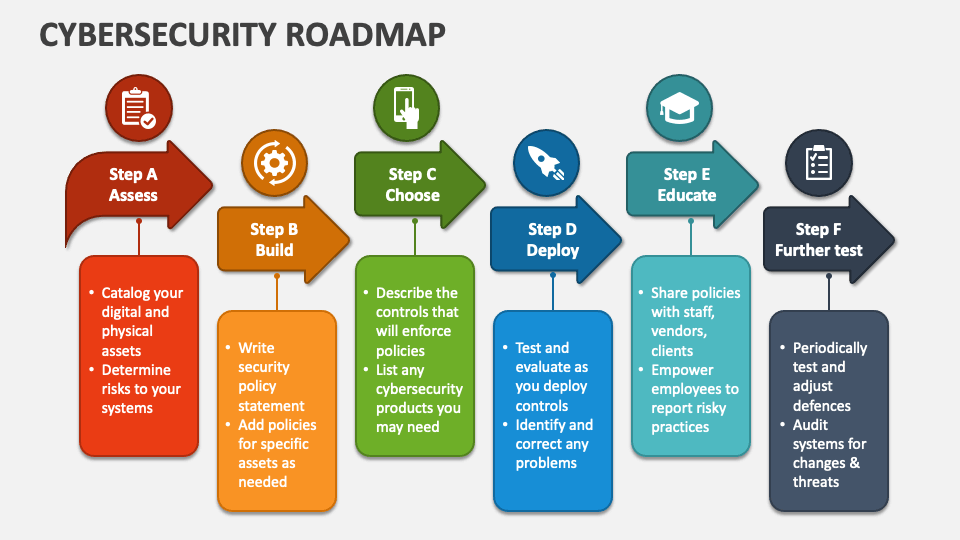
The cybersecurity industry is experiencing unprecedented growth, fueled by the increasing reliance on technology and the constant threat of cyberattacks. This demand for skilled cybersecurity professionals is expected to continue for years to come, making it a highly sought-after and rewarding career path.
Current and Projected Growth of Cybersecurity Jobs
The demand for cybersecurity professionals is booming, with a significant increase in job openings and a projected shortage of qualified candidates in the coming years. This trend is driven by several factors, including the increasing sophistication of cyberattacks, the growing reliance on digital technologies, and the rising awareness of cybersecurity risks.According to the U.S. Bureau of Labor Statistics (BLS), the employment of information security analysts is projected to grow by 33% from 2020 to 2030, much faster than the average for all occupations.
This growth is expected to be driven by the increasing use of computers and the growing volume of sensitive data stored electronically.
- Cybersecurity Ventures predicts that by 2025, there will be a global shortage of 3.5 million cybersecurity professionals. This shortage highlights the critical need for individuals to pursue careers in cybersecurity to address the growing threat landscape.
- The International Information System Security Certification Consortium (ISC)² estimates that the global cybersecurity workforce will need to grow by 62% by 2022 to meet the demand for qualified professionals. This growth is expected to be driven by the increasing use of cloud computing, the Internet of Things (IoT), and other emerging technologies.
Diversity of Cybersecurity Roles and Responsibilities
The cybersecurity field encompasses a wide range of roles and responsibilities, each requiring specialized skills and knowledge. Some of the most common cybersecurity roles include:
- Security Analyst: Security analysts are responsible for identifying, analyzing, and mitigating security threats. They monitor security systems, investigate security incidents, and develop security policies and procedures. They often specialize in specific areas, such as network security, endpoint security, or cloud security.
- Security Engineer: Security engineers design, implement, and maintain security systems. They are responsible for ensuring the security of networks, applications, and data. They often work with other IT professionals to develop and implement security solutions.
- Penetration Tester: Penetration testers, also known as ethical hackers, are responsible for simulating real-world cyberattacks to identify vulnerabilities in systems. They use their knowledge of hacking techniques to test security controls and recommend improvements.
- Security Architect: Security architects are responsible for designing and implementing the overall security strategy for an organization. They work with other IT professionals to ensure that security controls are in place to protect the organization’s assets.
- Security Manager: Security managers are responsible for overseeing the organization’s cybersecurity program. They develop and implement security policies, procedures, and standards. They also manage the security team and work with other departments to ensure that security risks are mitigated.
Skills and Qualifications Required for a Successful Career in Cybersecurity
A successful career in cybersecurity requires a combination of technical skills, soft skills, and certifications. Some of the most important skills and qualifications include:
- Technical Skills: Cybersecurity professionals need to have a strong understanding of computer networks, operating systems, and security protocols. They should also be proficient in using security tools and technologies, such as firewalls, intrusion detection systems, and antivirus software.
- Problem-Solving Skills: Cybersecurity professionals need to be able to identify and solve complex security problems. They should be able to think critically and creatively to develop effective solutions.
- Communication Skills: Cybersecurity professionals need to be able to communicate effectively with both technical and non-technical audiences. They should be able to explain complex security concepts in a clear and concise way.
- Certifications: Certifications can demonstrate your expertise and knowledge in specific areas of cybersecurity. Some of the most popular cybersecurity certifications include the Certified Information Systems Security Professional (CISSP), Certified Ethical Hacker (CEH), and CompTIA Security+.
The Educational Pathways in Cybersecurity
The cybersecurity field offers a diverse range of educational pathways for aspiring professionals. Whether you’re a recent graduate or a seasoned professional seeking a career change, there are options to equip you with the necessary skills and knowledge. This section explores the various educational options, compares and contrasts their strengths and weaknesses, and Artikels a hypothetical roadmap for a cybersecurity career.
Degree Programs
A degree program provides a comprehensive understanding of cybersecurity principles and practices. Bachelor’s and master’s degrees are commonly sought after in the industry. These programs cover a broad range of topics, including network security, cryptography, ethical hacking, and incident response.
- Bachelor’s Degree: A four-year bachelor’s degree in cybersecurity, computer science, or a related field provides a solid foundation in cybersecurity fundamentals. It equips graduates with the technical skills and theoretical knowledge necessary for entry-level cybersecurity roles.
- Master’s Degree: A master’s degree in cybersecurity offers advanced specialization in specific areas, such as digital forensics, security analysis, or cybersecurity management. It can enhance career prospects and open doors to leadership positions.
Certifications
Cybersecurity certifications validate an individual’s expertise in specific areas of cybersecurity. They demonstrate proficiency in particular technologies, tools, or methodologies.
- Vendor-Specific Certifications: These certifications are offered by technology vendors and focus on their specific products or services. Examples include the Cisco Certified Network Associate Security (CCNA Security) and CompTIA Security+.
- Industry-Recognized Certifications: These certifications are developed by professional organizations and cover broader cybersecurity concepts. Examples include the Certified Information Systems Security Professional (CISSP) and the Certified Ethical Hacker (CEH).
Boot Camps
Cybersecurity boot camps are intensive, short-term programs designed to provide practical skills and hands-on experience. They typically focus on specific cybersecurity domains, such as ethical hacking, penetration testing, or incident response.
- Strengths: Boot camps offer a fast-paced and practical learning experience, often leading to immediate job opportunities. They are also relatively affordable compared to traditional degree programs.
- Weaknesses: Boot camps may not provide the same depth of knowledge as a degree program. They may also lack the theoretical foundation needed for advanced cybersecurity roles.
Hypothetical Educational Roadmap
For someone interested in pursuing a cybersecurity career, a hypothetical educational roadmap could involve:
- Obtain a Bachelor’s Degree: Begin with a bachelor’s degree in cybersecurity, computer science, or a related field. This provides a strong foundation in core cybersecurity principles and technologies.
- Gain Practical Experience: Supplement your degree with internships or entry-level cybersecurity roles to gain practical experience and build your skills.
- Pursue Relevant Certifications: Obtain industry-recognized certifications, such as CompTIA Security+ or CISSP, to validate your expertise and enhance your career prospects.
- Consider a Master’s Degree: If you aspire to specialize in a specific area of cybersecurity or pursue advanced roles, consider pursuing a master’s degree.
- Stay Updated: The cybersecurity landscape is constantly evolving. Continuously learn and stay updated on emerging threats, technologies, and best practices.
The Economic Impact of Cybersecurity

Cybersecurity is not merely a technical concern; it has profound economic implications that impact individuals, businesses, and governments alike. The financial ramifications of cyberattacks are substantial, leading to significant losses and disruptions. Conversely, investing in robust cybersecurity measures offers substantial economic benefits, including reduced risk, enhanced productivity, and a competitive advantage.
The Financial Impact of Cyberattacks
Cyberattacks pose a significant financial threat to individuals, businesses, and governments. The cost of cybercrime is estimated to be in the trillions of dollars annually, encompassing various forms of attacks, such as data breaches, ransomware, and phishing scams.
- Individuals: Cyberattacks can lead to identity theft, financial fraud, and reputational damage. Victims may experience significant financial losses, including stolen funds, credit card fraud, and expenses related to recovering their identity.
- Businesses: Cyberattacks can disrupt operations, damage reputation, and lead to substantial financial losses. The costs include lost revenue, downtime, legal expenses, regulatory fines, and the expense of restoring data and systems.
- Governments: Cyberattacks can compromise critical infrastructure, disrupt government services, and undermine national security. The economic impact includes the cost of responding to attacks, repairing damaged systems, and protecting sensitive information.
The Economic Benefits of Cybersecurity Investments, Is cyber security a trade
Investing in cybersecurity measures can significantly reduce the risk of cyberattacks and their associated financial consequences. By implementing robust security practices, organizations can protect their assets, ensure business continuity, and enhance their reputation.
- Reduced Risk: By investing in cybersecurity, organizations can significantly reduce the likelihood and impact of cyberattacks. This includes implementing strong passwords, multi-factor authentication, firewalls, intrusion detection systems, and regular security audits.
- Increased Productivity: Secure systems and networks contribute to increased productivity by minimizing downtime, reducing the risk of data loss, and improving employee confidence.
- Enhanced Reputation: Organizations with strong cybersecurity practices build trust with customers, partners, and investors. A solid cybersecurity reputation enhances brand value and strengthens customer loyalty.
Cybersecurity as a Driver of Innovation and Economic Growth
Cybersecurity is not just a cost; it is an investment that can drive innovation and economic growth. By fostering a secure digital environment, cybersecurity enables the development of new technologies, business models, and industries.
- Emerging Technologies: Cybersecurity is essential for the development and deployment of emerging technologies, such as artificial intelligence (AI), blockchain, and the Internet of Things (IoT). These technologies rely on secure data exchange and processing, which are critical for their success.
- Digital Transformation: Cybersecurity is a key enabler of digital transformation, enabling businesses to adopt new technologies, automate processes, and improve efficiency.
- Economic Growth: A secure digital environment attracts investment, fosters innovation, and creates new jobs, contributing to economic growth.
The Ethical Considerations in Cybersecurity
The realm of cybersecurity, while focused on safeguarding digital assets, is not devoid of ethical dilemmas. As technology evolves, so too do the ethical complexities faced by cybersecurity professionals, requiring them to navigate delicate issues surrounding data privacy, surveillance, and the potential weaponization of their skills.
Data Privacy and Surveillance
Data privacy and surveillance are at the forefront of ethical discussions in cybersecurity. The increasing reliance on digital systems and the vast amounts of personal data collected and processed by organizations present significant challenges. Cybersecurity professionals must grapple with the delicate balance between protecting sensitive information and facilitating legitimate security measures.
- Data Minimization: This principle suggests collecting only the necessary data for a specific purpose, minimizing the potential for misuse or unauthorized access.
- Transparency and Consent: Individuals should be informed about how their data is collected, used, and protected. Clear and concise consent mechanisms are crucial for ethical data handling.
- Data Retention: Establishing clear guidelines for data retention is essential to prevent the accumulation of unnecessary data and reduce the risk of breaches.
Weaponization of Technology
The potential for weaponization of cybersecurity tools poses significant ethical challenges. Malicious actors can exploit vulnerabilities in systems and networks to disrupt critical infrastructure, steal sensitive data, or spread misinformation.
- Responsible Disclosure: Cybersecurity professionals have a responsibility to disclose vulnerabilities to vendors and organizations in a responsible manner, allowing them to address the issue before malicious actors can exploit it.
- Dual-Use Technologies: Cybersecurity tools can be used for both defensive and offensive purposes. Ethical considerations must guide the development and deployment of these tools to ensure they are not misused.
- Cyberwarfare: The use of cyberattacks as a tool of warfare raises serious ethical concerns. International agreements and regulations are needed to establish clear boundaries and prevent escalation.
Hypothetical Scenario: Ethical Conflict
Imagine a scenario where a cybersecurity professional discovers a vulnerability in a critical infrastructure system, such as a power grid. This vulnerability could be exploited by a nation-state to disrupt power supply and cause widespread chaos. The professional faces a difficult choice:
- Report the vulnerability to the authorities, potentially triggering a diplomatic incident.
- Attempt to patch the vulnerability quietly, potentially leaving the system vulnerable to future attacks.
- Contact the organization responsible for the system and urge them to take immediate action.
This scenario highlights the complex ethical considerations that cybersecurity professionals face. Their actions can have far-reaching consequences, requiring them to weigh the potential benefits and risks of their choices.
The Future of Cybersecurity
The cybersecurity landscape is constantly evolving, driven by the rapid advancements in technology and the increasing sophistication of cyberattacks. Predicting the future of cybersecurity requires understanding the emerging trends and challenges, the impact of disruptive technologies, and the potential for innovative solutions.
The Impact of Emerging Technologies on Cybersecurity
The rise of artificial intelligence (AI), blockchain, and other emerging technologies will have a profound impact on cybersecurity. These technologies can enhance security measures but also create new vulnerabilities.
- AI in Cybersecurity: AI-powered tools can automate threat detection, analysis, and response, improving efficiency and accuracy. However, AI can also be used by attackers to create more sophisticated and targeted attacks.
- Blockchain in Cybersecurity: Blockchain technology offers enhanced security features, such as immutability and transparency, which can be used to secure sensitive data and transactions. However, blockchain vulnerabilities can still be exploited by attackers.
The Potential for New Cybersecurity Tools and Strategies
The future of cybersecurity will likely involve the development of new tools and strategies to address emerging threats. These innovations will leverage emerging technologies, such as AI and blockchain, to enhance security measures.
- Quantum Computing: Quantum computing has the potential to break current encryption algorithms, requiring the development of new, quantum-resistant encryption methods.
- Zero Trust Security: Zero-trust security models assume that no user or device can be trusted by default, requiring strict verification and authorization for access.
- Biometric Authentication: Biometric authentication methods, such as facial recognition and fingerprint scanning, can enhance security by providing more robust user verification.
As we venture deeper into the digital age, the importance of cybersecurity will only intensify. The ever-evolving threat landscape demands a robust and adaptable workforce. Investing in cybersecurity education and training is not just a matter of protecting our digital lives, but also of fostering innovation and driving economic growth. By understanding the complexities of cyber security, we can navigate the digital frontier with confidence, ensuring a safe and secure future for all.
Key Questions Answered: Is Cyber Security A Trade
What are some common cybersecurity jobs?
The cybersecurity field offers a wide range of roles, including security analysts, ethical hackers, penetration testers, incident responders, and cybersecurity engineers.
What are the most important skills for a cybersecurity professional?
Essential skills include strong technical expertise in networking, operating systems, and programming, as well as analytical thinking, problem-solving, and communication skills.
Is a cybersecurity career challenging?
Yes, cybersecurity can be a demanding field, requiring constant learning and adaptation to evolving threats. However, it is also incredibly rewarding, offering the opportunity to make a real difference in protecting people and organizations.
What are some ethical considerations in cybersecurity?
Ethical dilemmas in cybersecurity include balancing data privacy with security, the use of surveillance technologies, and the potential for weaponizing cybersecurity tools.





