What is a corporate security – What is corporate security? In a world where digital threats are ever-evolving and physical vulnerabilities abound, securing your business is paramount. Corporate security encompasses a multifaceted approach to safeguarding your organization’s assets, reputation, and operations from various risks.
It’s a dynamic field that has evolved alongside the changing landscape of technology and business practices. From physical security measures to cybersecurity protocols, the scope of corporate security is vast, demanding a comprehensive and proactive approach.
Defining Corporate Security
Corporate security is a multifaceted field encompassing the protection of a company’s assets, people, and reputation from various threats. It’s not just about physical security measures like guards and fences; it involves a comprehensive approach to safeguarding all aspects of an organization’s operations.
The Evolution of Corporate Security
Corporate security has evolved significantly over time, adapting to changing threats and technological advancements. In the past, physical security was the primary focus, with emphasis on preventing theft and vandalism. Today, however, the landscape is far more complex, with cyberattacks, data breaches, and terrorism posing serious risks to businesses.
- The rise of the internet and digital technologies has led to a surge in cyber threats, such as data breaches, ransomware attacks, and phishing scams.
- The increasing interconnectedness of businesses through global supply chains has made them vulnerable to disruptions from natural disasters, political instability, and other unforeseen events.
- The growing awareness of social responsibility and environmental concerns has prompted companies to prioritize ethical and sustainable practices, which can impact their security posture.
Types of Corporate Security Threats
Corporate security threats can be categorized into several broad types:
- Physical Security Threats: These involve physical intrusions, theft, vandalism, and other acts of violence against company property and personnel. Examples include break-ins, robberies, assaults, and workplace violence.
- Cybersecurity Threats: These threats target an organization’s digital infrastructure, data, and systems. Examples include malware infections, data breaches, phishing attacks, and denial-of-service attacks.
- Internal Threats: These threats originate from within an organization, such as disgruntled employees, rogue insiders, or accidental data leaks.
- External Threats: These threats come from outside the organization, such as competitors, activists, criminals, or foreign governments.
- Reputational Threats: These threats can damage a company’s image and brand, leading to financial losses and customer churn. Examples include negative media coverage, social media campaigns, and product recalls.
Key Components of Corporate Security: What Is A Corporate Security
A robust corporate security program is not a single entity but a complex tapestry woven from various interconnected threads. These threads, or components, work in harmony to safeguard an organization’s assets, reputation, and operational continuity. This section delves into the essential pillars that form the foundation of a comprehensive corporate security strategy.
Physical Security
Physical security encompasses the measures taken to protect an organization’s physical assets, facilities, and personnel from unauthorized access, damage, or theft. This includes:
- Access Control: Implementing systems like security guards, keycard access, and surveillance cameras to restrict entry to authorized personnel. Best practices include conducting regular security audits, implementing multi-factor authentication, and ensuring proper training for security personnel.
- Perimeter Security: Fortifying the exterior of buildings and facilities with fences, gates, lighting, and intrusion detection systems to deter unauthorized entry. Best practices involve using high-quality materials, installing sensors with advanced detection capabilities, and regularly maintaining security infrastructure.
- Environmental Security: Protecting facilities from natural disasters, environmental hazards, and other threats like fire, flood, and extreme weather conditions. Best practices include implementing disaster recovery plans, conducting regular drills, and ensuring compliance with relevant building codes and regulations.
Cybersecurity
Cybersecurity focuses on protecting an organization’s digital assets, including data, networks, and systems, from cyberattacks, data breaches, and other malicious activities. Key aspects include:
- Network Security: Implementing firewalls, intrusion detection systems, and other network security measures to prevent unauthorized access and protect against cyberattacks. Best practices involve regularly updating security software, segmenting networks, and implementing strong password policies.
- Data Security: Implementing measures to protect sensitive data from unauthorized access, use, disclosure, modification, or destruction. Best practices include encrypting data at rest and in transit, implementing data loss prevention solutions, and conducting regular data security audits.
- Endpoint Security: Protecting individual devices like laptops, smartphones, and tablets from malware, ransomware, and other threats. Best practices include installing anti-virus software, using strong passwords, and regularly updating operating systems and applications.
Information Security
Information security focuses on protecting an organization’s confidential information, including trade secrets, intellectual property, and customer data, from unauthorized access, use, disclosure, modification, or destruction. Key components include:
- Data Classification: Categorizing data based on its sensitivity and value to the organization. Best practices involve creating clear data classification policies, training employees on data handling procedures, and regularly reviewing data classification assignments.
- Access Control: Implementing access control measures to restrict access to sensitive information to authorized personnel. Best practices include using role-based access control, implementing multi-factor authentication, and auditing access logs regularly.
- Data Encryption: Encrypting sensitive data to protect it from unauthorized access even if it is stolen or intercepted. Best practices involve using strong encryption algorithms, implementing encryption at rest and in transit, and ensuring proper key management.
Security Awareness Training
Security awareness training is crucial for fostering a culture of security within an organization. It involves educating employees on security threats, policies, and best practices to help them identify and mitigate risks. Key elements include:
- Phishing Awareness: Training employees to recognize and avoid phishing scams, which often target sensitive information. Best practices include providing realistic phishing simulations, emphasizing the importance of verifying emails and links, and promoting reporting suspicious activities.
- Password Security: Educating employees on the importance of creating strong passwords and using different passwords for different accounts. Best practices include promoting the use of password managers, emphasizing the importance of not sharing passwords, and implementing password complexity requirements.
- Data Security Best Practices: Training employees on proper data handling procedures, including how to identify and report security incidents. Best practices include providing clear guidelines on data sharing, access control, and data disposal, and conducting regular security awareness campaigns.
Incident Response
Incident response involves having a plan in place to address security incidents and breaches promptly and effectively. Key elements include:
- Incident Response Plan: Developing a comprehensive plan outlining the steps to be taken in the event of a security incident. Best practices include defining roles and responsibilities, establishing communication channels, and conducting regular incident response drills.
- Incident Detection and Analysis: Implementing systems and processes to detect and analyze security incidents promptly. Best practices include using security monitoring tools, setting up alerts for suspicious activities, and conducting regular security assessments.
- Incident Containment and Remediation: Taking steps to contain the damage caused by a security incident and restore normal operations. Best practices include isolating affected systems, containing the spread of malware, and implementing remediation measures to address vulnerabilities.
Business Continuity and Disaster Recovery
Business continuity and disaster recovery planning focuses on ensuring that an organization can continue operating in the event of a major disruption, such as a natural disaster, cyberattack, or other emergency. Key elements include:
- Business Impact Analysis: Identifying critical business functions and assessing the potential impact of disruptions. Best practices include conducting regular business impact analyses, identifying critical dependencies, and developing recovery time objectives (RTOs).
- Disaster Recovery Plan: Developing a plan outlining the steps to be taken to restore critical business functions after a disaster. Best practices include identifying recovery sites, establishing data backup procedures, and conducting regular disaster recovery drills.
- Business Continuity Plan: Developing a plan outlining how to maintain essential business operations during a disruption. Best practices include identifying alternative communication channels, establishing backup systems, and providing training for employees on business continuity procedures.
Security Governance, Risk Management, and Compliance
Security governance, risk management, and compliance are essential for ensuring that security measures are aligned with organizational objectives and legal requirements. Key elements include:
- Security Policies and Procedures: Establishing clear security policies and procedures that define acceptable use of IT resources, data handling practices, and incident response procedures. Best practices include regularly reviewing and updating policies, providing training on policies, and ensuring compliance with policies.
- Risk Management: Identifying, assessing, and mitigating security risks. Best practices include conducting regular risk assessments, prioritizing risks based on likelihood and impact, and implementing controls to mitigate risks.
- Compliance: Ensuring compliance with relevant laws, regulations, and industry standards. Best practices include staying informed about relevant regulations, implementing controls to ensure compliance, and conducting regular audits to verify compliance.
Physical Security Measures
Physical security measures are the tangible safeguards implemented to protect a corporation’s assets, employees, and facilities from unauthorized access, theft, damage, and other threats. They serve as the first line of defense against physical intrusions, creating a barrier against potential risks. These measures are essential for maintaining a safe and secure environment for employees and visitors, protecting sensitive information and assets, and ensuring business continuity.
Physical Security Technologies
Physical security technologies play a crucial role in enhancing a corporation’s overall security posture. They provide a combination of surveillance, detection, and access control capabilities, enabling proactive measures to deter and respond to threats.
- Access Control Systems: These systems restrict unauthorized entry into designated areas by verifying user identity and granting access based on pre-defined permissions. Examples include key card systems, biometric scanners, and multi-factor authentication.
- Surveillance Systems: These systems utilize cameras, sensors, and monitoring software to detect and record activities within and around a facility. They can include closed-circuit television (CCTV) systems, motion detectors, and intrusion detection systems.
- Perimeter Security: Perimeter security measures create a physical barrier around the facility, preventing unauthorized entry and providing early warning of potential intrusions. These measures can include fences, gates, lighting, and alarm systems.
- Security Lighting: Proper lighting can deter crime and make it easier to identify potential threats. Security lighting should be strategically placed to illuminate high-risk areas and ensure visibility at night.
- Security Guards: Security guards provide a visible deterrent and can respond to security incidents in real-time. They can also conduct patrols, monitor access points, and enforce security protocols.
- Emergency Response Systems: These systems are designed to facilitate rapid response to security incidents. They can include fire alarms, emergency evacuation plans, and communication systems.
| Technology | Functionality | Benefits |
|---|---|---|
| Access Control Systems | Restrict unauthorized access to designated areas by verifying user identity. | Enhanced security, reduced risk of theft, improved accountability, and increased compliance with regulations. |
| Surveillance Systems | Monitor and record activities within and around a facility, providing evidence in case of incidents. | Increased situational awareness, early detection of threats, deterrence of criminal activity, and improved investigation capabilities. |
| Perimeter Security | Create a physical barrier around the facility, preventing unauthorized entry and providing early warning of potential intrusions. | Reduced risk of unauthorized access, increased security awareness, and improved response time to security incidents. |
| Security Lighting | Illuminate high-risk areas, deterring crime and making it easier to identify potential threats. | Improved visibility, enhanced security awareness, and reduced risk of crime. |
| Security Guards | Provide a visible deterrent, respond to security incidents, and enforce security protocols. | Increased security presence, rapid response to incidents, and enhanced security awareness. |
| Emergency Response Systems | Facilitate rapid response to security incidents, ensuring safety and minimizing damage. | Improved safety, reduced risk of injuries, and faster response to emergencies. |
Risk Assessment and Vulnerability Analysis
Risk assessment and vulnerability analysis are essential components of physical security planning. They help identify potential threats and vulnerabilities, allowing corporations to prioritize security measures and allocate resources effectively.
“A risk assessment involves identifying potential threats, analyzing their likelihood and impact, and determining appropriate mitigation strategies.”
“Vulnerability analysis focuses on identifying weaknesses in the physical security infrastructure, such as access points, perimeter defenses, and surveillance systems.”
By conducting thorough risk assessments and vulnerability analyses, corporations can develop a comprehensive physical security plan that addresses specific threats and vulnerabilities. This proactive approach helps minimize risks, protect assets, and ensure a safe and secure environment for all stakeholders.
Cybersecurity and Data Protection
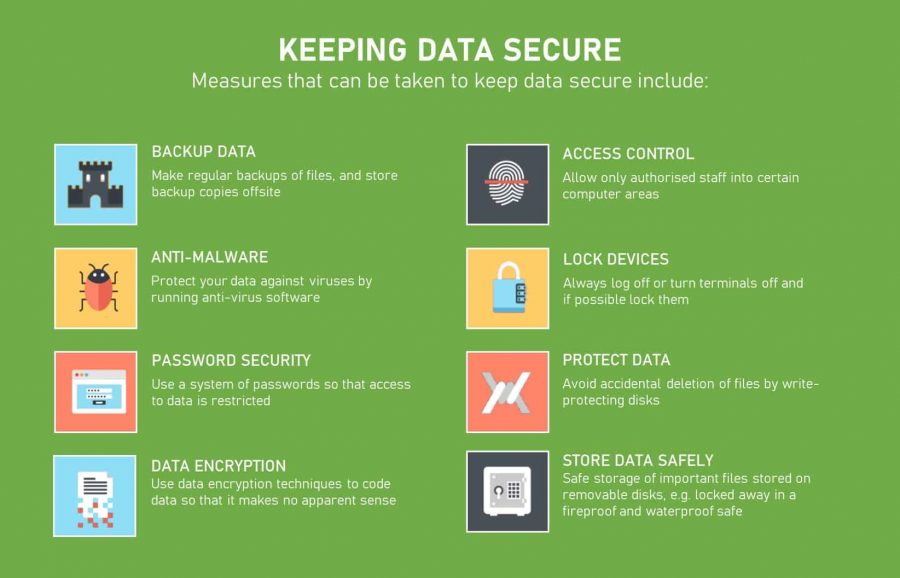
In the contemporary digital landscape, where corporations heavily rely on technology for operations, communication, and data storage, cybersecurity has become an indispensable aspect of corporate security. Data breaches, ransomware attacks, and other cyber threats pose significant risks to businesses, impacting their financial stability, reputation, and customer trust. Consequently, safeguarding sensitive data and mitigating cyber risks is paramount for corporations to ensure their continued success and resilience in the digital age.
Common Cybersecurity Threats and Vulnerabilities, What is a corporate security
Cybersecurity threats and vulnerabilities are constantly evolving, making it challenging for corporations to stay ahead of malicious actors. These threats can originate from various sources, including internal employees, external hackers, and nation-state actors. Understanding the common cybersecurity threats and vulnerabilities facing corporations is crucial for developing effective defense strategies.
- Malware: Malicious software designed to infiltrate computer systems and steal data, disrupt operations, or gain unauthorized access. Examples include viruses, worms, trojans, and ransomware.
- Phishing Attacks: Deceptive emails or messages designed to trick users into revealing sensitive information, such as login credentials or financial details.
- Social Engineering: Manipulative tactics used to gain access to confidential information or systems by exploiting human psychology.
- Denial-of-Service (DoS) Attacks: Attempts to overwhelm a system with traffic, rendering it unavailable to legitimate users.
- Data Breaches: Unauthorized access to sensitive data, leading to theft, misuse, or disclosure of confidential information.
- Insider Threats: Malicious actions by employees or contractors who have access to sensitive data or systems.
- Zero-Day Exploits: Vulnerabilities in software or systems that are unknown to developers and security vendors, allowing attackers to exploit them before patches are available.
Best Practices for Safeguarding Sensitive Data and Mitigating Cyber Risks
Implementing robust cybersecurity measures is essential for corporations to protect their data and systems from cyber threats. These measures encompass various aspects, including technological safeguards, employee training, and security policies.
- Strong Passwords and Multi-Factor Authentication: Encouraging employees to use strong, unique passwords and implementing multi-factor authentication for sensitive accounts significantly enhances security.
- Regular Security Audits and Vulnerability Assessments: Conducting regular security audits and vulnerability assessments helps identify weaknesses in systems and applications, allowing for timely remediation.
- Data Encryption: Encrypting sensitive data at rest and in transit prevents unauthorized access and protects it from data breaches.
- Network Security: Implementing firewalls, intrusion detection systems, and other network security measures to prevent unauthorized access and malicious traffic.
- Employee Security Awareness Training: Educating employees about cybersecurity threats and best practices is crucial to minimize the risk of human error and social engineering attacks.
- Incident Response Plan: Having a comprehensive incident response plan in place to handle cyber incidents effectively and minimize damage.
- Regular Software Updates and Patches: Keeping software and operating systems up to date with the latest security patches is essential to address vulnerabilities and prevent exploits.
- Data Backup and Recovery: Implementing regular data backups and disaster recovery plans ensures that data can be restored in case of a cyber incident or system failure.
Human Security and Risk Management
Human security is a critical aspect of corporate security, recognizing that people are the most valuable asset and the most vulnerable target. It encompasses measures to protect employees, visitors, and other stakeholders from physical harm, threats, and security breaches. Effective human security strategies involve a comprehensive approach that integrates security awareness training, incident response protocols, and robust risk management practices.
Employee Training and Awareness
Employee training and awareness programs play a crucial role in fostering a security-conscious culture within an organization. By equipping employees with the knowledge and skills to identify and mitigate security risks, organizations can significantly enhance their overall security posture.
- Security Awareness Training: Organizations should provide regular security awareness training to all employees, covering topics such as phishing scams, social engineering, data security best practices, and incident reporting procedures. This training should be tailored to the specific roles and responsibilities of employees and delivered through interactive methods such as simulations, quizzes, and case studies.
- Phishing Simulations: Phishing simulations are a valuable tool for testing employee awareness and susceptibility to phishing attacks. By sending realistic phishing emails, organizations can identify employees who are more likely to click on malicious links or open attachments. This allows for targeted training and remediation efforts to address individual vulnerabilities.
- Security Best Practices: Employees should be trained on security best practices, such as using strong passwords, enabling multi-factor authentication, avoiding public Wi-Fi networks, and reporting suspicious activity. These simple steps can significantly reduce the risk of security breaches.
- Incident Reporting Procedures: Clear and concise incident reporting procedures are essential for timely detection and response to security incidents. Employees should be trained on how to report suspicious activity, security breaches, and data leaks, ensuring that incidents are promptly investigated and addressed.
Security Risk Management
Effective security risk management is a continuous process that involves identifying, assessing, and mitigating potential security threats. By proactively addressing security risks, organizations can reduce their vulnerability to attacks and minimize the impact of security incidents.
- Risk Assessment: Organizations should conduct regular risk assessments to identify potential security threats and vulnerabilities. This process should involve analyzing internal and external factors that could impact the organization’s security, such as employee negligence, cyberattacks, natural disasters, and regulatory compliance requirements.
- Risk Mitigation: Once security risks have been identified, organizations should develop and implement mitigation strategies to reduce their impact. These strategies may involve implementing technical controls, such as firewalls and intrusion detection systems, or implementing administrative controls, such as access control policies and security awareness training.
- Incident Response Plan: A well-defined incident response plan is essential for responding to security incidents effectively. The plan should Artikel the steps to be taken in the event of a security breach, including incident notification, containment, investigation, remediation, and recovery. Regular testing and drills should be conducted to ensure that the plan is effective and that employees are familiar with their roles and responsibilities.
- Continuous Monitoring: Security monitoring is an ongoing process that involves continuously monitoring the organization’s security systems and networks for suspicious activity. This can involve using security information and event management (SIEM) tools, intrusion detection systems, and other security monitoring technologies.
Legal and Regulatory Considerations
Corporate security is not merely a matter of internal policy; it’s deeply intertwined with a complex web of laws and regulations designed to protect individuals, businesses, and national interests. These legal frameworks provide the foundation for responsible security practices, ensuring that companies operate ethically and comply with societal expectations.
The Legal Landscape
The legal landscape governing corporate security is diverse and multifaceted, encompassing various areas such as data privacy, cybersecurity, physical security, and intellectual property protection. Understanding these legal requirements is crucial for organizations to navigate the complex security environment effectively.
Data Privacy Laws
Data privacy laws are fundamental to safeguarding sensitive information and protecting individuals’ rights. They govern how companies collect, use, store, and disclose personal data.
Key Data Privacy Laws
- General Data Protection Regulation (GDPR): This comprehensive European Union regulation applies to organizations processing personal data of individuals within the EU, regardless of the organization’s location. GDPR mandates strict data protection principles, including consent, data minimization, and the right to be forgotten.
- California Consumer Privacy Act (CCPA): This California law grants consumers the right to know what personal data is collected, the right to delete data, and the right to opt out of the sale of personal data.
- Health Insurance Portability and Accountability Act (HIPAA): This US law protects sensitive health information, requiring organizations handling protected health information (PHI) to implement strong security measures.
Cybersecurity Regulations
Cybersecurity regulations focus on protecting critical infrastructure and sensitive data from cyberattacks. They establish security standards, reporting requirements, and breach notification protocols.
Key Cybersecurity Regulations
- National Institute of Standards and Technology (NIST) Cybersecurity Framework: This voluntary framework provides a roadmap for organizations to improve their cybersecurity posture. It encompasses five core functions: Identify, Protect, Detect, Respond, and Recover.
- Payment Card Industry Data Security Standard (PCI DSS): This set of security standards applies to organizations that process, store, or transmit credit card data. PCI DSS mandates specific security controls to protect cardholder data.
- General Data Protection Regulation (GDPR): GDPR also includes provisions related to cybersecurity, requiring organizations to implement appropriate technical and organizational measures to protect personal data from unauthorized access, processing, or disclosure.
Implications of Non-Compliance
Non-compliance with security regulations can have significant consequences for organizations. These consequences can include:
- Financial penalties: Many security regulations carry hefty fines for violations.
- Reputational damage: Data breaches and security incidents can severely damage an organization’s reputation, leading to loss of customer trust and market share.
- Legal liability: Organizations may face lawsuits from individuals whose data has been compromised or from regulatory bodies for non-compliance.
- Loss of business: Non-compliance can lead to suspension of licenses, restrictions on operations, or even the closure of a business.
Emerging Trends in Corporate Security

The field of corporate security is constantly evolving, driven by technological advancements, changing threat landscapes, and evolving regulatory environments. Staying ahead of the curve is crucial for organizations to protect their assets, employees, and reputation. This section will delve into some of the most prominent emerging trends in corporate security and their implications.
The Impact of Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are revolutionizing various industries, and corporate security is no exception. These technologies are transforming how organizations approach security by enhancing threat detection, automating security tasks, and improving decision-making.AI and ML algorithms can analyze vast amounts of data from various sources, such as network logs, security cameras, and employee behavior, to identify patterns and anomalies that might indicate a security breach.
This proactive approach enables organizations to detect threats early and respond swiftly. For example, AI-powered security systems can analyze video footage from surveillance cameras to detect suspicious activities like unauthorized access or unusual behavior, triggering alerts and enabling security personnel to intervene promptly. Moreover, AI and ML can automate repetitive security tasks, such as vulnerability scanning and incident response, freeing up security professionals to focus on more strategic initiatives.
AI and ML are also playing a crucial role in improving decision-making by providing insights into security risks and vulnerabilities. For example, AI-powered risk assessment tools can analyze data from various sources to identify potential threats and prioritize security measures based on their likelihood and impact.
“AI and ML are transforming the way we approach security, enabling us to be more proactive, efficient, and effective in protecting our organizations.”
[Insert name of a cybersecurity expert or researcher]
In conclusion, corporate security is a crucial element of any successful business. It requires a multifaceted strategy that addresses physical, digital, and human vulnerabilities. By implementing robust security measures, fostering a culture of awareness, and staying informed about emerging threats, organizations can mitigate risks and protect their assets, reputation, and future.
FAQ
What are the most common types of corporate security threats?
Common threats include data breaches, cyberattacks, physical theft, fraud, insider threats, and natural disasters.
How can I ensure my employees are aware of security risks?
Implement regular security training programs, conduct awareness campaigns, and establish clear policies and procedures for employees to follow.
What are some best practices for managing security incidents?
Develop a comprehensive incident response plan, have a dedicated team to handle incidents, and conduct regular drills to test your plan’s effectiveness.






