What is NIDS in cyber security? Think of it like this: your computer’s a fancy new car, but it’s parked on a busy street. You gotta keep an eye out for those sneaky thieves who wanna steal your data, right? That’s where NIDS comes in, like a trusty guard dog, sniffing out any suspicious activity trying to get into your network.
NIDS stands for Network Intrusion Detection System. It’s a crucial part of cybersecurity, acting as a watchful guardian, analyzing network traffic to identify potential threats like malware, hacking attempts, and unauthorized access. It’s like a super-smart security camera, but instead of recording, it alerts you when something fishy is going down.
Introduction to NIDS: What Is Nids In Cyber Security
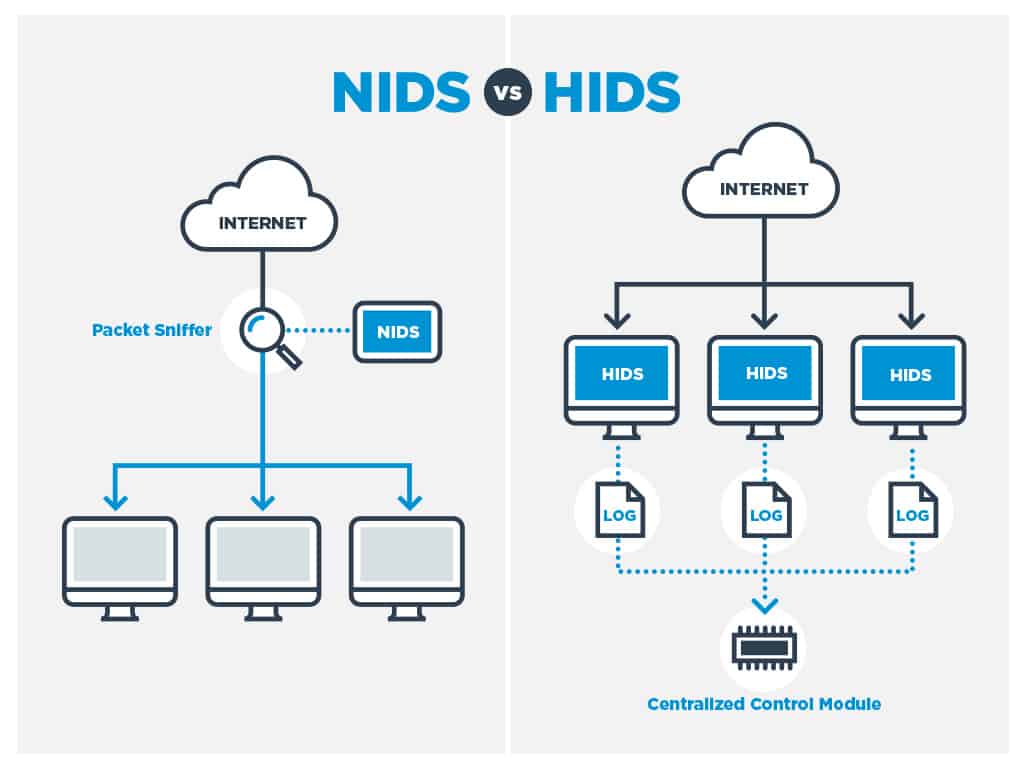
A Network Intrusion Detection System (NIDS) is a crucial cybersecurity tool that acts as a vigilant guardian, constantly monitoring network traffic for suspicious activity. It’s like having a dedicated security team working 24/7, analyzing the flow of data to detect potential threats and alert you to any suspicious behavior.NIDS plays a vital role in safeguarding your network by identifying malicious activities that might otherwise slip past traditional security measures.
It’s designed to detect and alert you to potential attacks, helping you take immediate action to protect your systems and data.
History of NIDS
NIDS technology has evolved significantly over the years, reflecting the ever-changing landscape of cyber threats. Early NIDS systems were primarily rule-based, relying on predefined signatures to identify known attacks. However, with the emergence of sophisticated and evolving attack methods, NIDS systems have advanced to incorporate more sophisticated techniques, including anomaly detection and machine learning.
- Early NIDS: The first NIDS systems emerged in the 1980s, primarily focused on detecting known vulnerabilities and attacks. They relied heavily on signature-based detection, analyzing network traffic for patterns that matched predefined attack signatures.
- Evolution of NIDS: As cyberattacks became more sophisticated, NIDS systems evolved to incorporate anomaly detection techniques. These systems analyze network traffic for deviations from established patterns, identifying potentially malicious activity that might not be recognized by traditional signature-based methods.
- Modern NIDS: Today’s NIDS systems leverage advanced technologies like machine learning and artificial intelligence to further enhance their capabilities. They can analyze vast amounts of data, learn from past attacks, and identify new and emerging threats in real-time.
How NIDS Works
NIDS (Network Intrusion Detection Systems) work by continuously monitoring network traffic for suspicious activities. They act as vigilant guards, analyzing the flow of data to detect potential threats and alert administrators about potential intrusions.
Types of NIDS
NIDS employ different techniques to identify malicious activity. These techniques can be broadly categorized into three types:
- Signature-based NIDS: These systems use predefined patterns, known as signatures, to identify known threats. Signatures are essentially fingerprints of malicious activities, such as specific commands or data sequences used by malware. When a signature is detected in the network traffic, the NIDS raises an alert, indicating a potential intrusion. Signature-based NIDS are effective in detecting known attacks but may struggle with novel or zero-day attacks that don’t have predefined signatures.
- Anomaly-based NIDS: These systems focus on identifying deviations from normal network behavior. They establish a baseline of “normal” traffic patterns and flag any significant departures from this baseline as suspicious. Anomaly-based NIDS are adept at detecting unknown attacks that don’t have signatures but may generate false positives when legitimate traffic deviates from the established baseline.
- Hybrid NIDS: These systems combine the strengths of both signature-based and anomaly-based approaches. They utilize predefined signatures to detect known threats and simultaneously monitor network traffic for unusual patterns. Hybrid NIDS offer a comprehensive approach to intrusion detection, balancing the advantages of both techniques while minimizing their limitations.
NIDS Architecture
A typical NIDS architecture consists of three key components:
- Sensors: Sensors are the front-line components of a NIDS. They capture and analyze network traffic flowing through the network. Sensors can be deployed in various locations, such as network switches, routers, or dedicated security appliances.
- Analyzers: Analyzers are responsible for processing the captured network traffic data. They apply the detection techniques (signature-based, anomaly-based, or hybrid) to identify suspicious activity. Analyzers use algorithms and rule sets to analyze the data and generate alerts when potential threats are detected.
- Reporting: Reporting components provide visibility into the NIDS activity. They generate reports that summarize the detected threats, including details such as the type of attack, the source and destination of the attack, and the time of occurrence. These reports are crucial for security analysts to understand the threat landscape, investigate incidents, and improve security posture.
NIDS Detection Methods

NIDS employ various methods to identify malicious activity. These techniques can be broadly categorized into signature-based and anomaly-based approaches. Each method has its own strengths and weaknesses, and the choice of technique often depends on the specific security needs and the environment in which the NIDS is deployed.
Signature Matching
Signature matching is a common intrusion detection technique. It involves comparing network traffic against a database of known attack signatures. These signatures are essentially patterns or characteristics associated with specific types of attacks.
- Signatures can include specific byte sequences, protocol anomalies, or even specific attack patterns.
- When a signature match is found, the NIDS triggers an alert, indicating a potential intrusion attempt.
For example, a signature for a denial-of-service attack might look for a large number of SYN packets originating from the same IP address in a short period.
Signature matching is effective at detecting known attacks, but it has limitations:
- Limited against zero-day attacks: Signature-based NIDS are ineffective against new attacks that haven’t been documented and haven’t yet been added to the signature database.
- False positives: Signature matching can sometimes trigger alerts for legitimate traffic that happens to match a known attack signature. This can lead to false positives and alert fatigue.
- Large signature database: Maintaining a comprehensive and up-to-date signature database can be challenging and resource-intensive.
Anomaly Detection
Anomaly detection takes a different approach. Instead of relying on pre-defined signatures, it analyzes network traffic to identify deviations from normal behavior.
- This method establishes a baseline of normal traffic patterns based on historical data.
- Any significant departure from this baseline is flagged as an anomaly, suggesting a potential intrusion attempt.
For instance, an anomaly detection system might detect a sudden spike in traffic volume from a specific IP address or unusual communication patterns between different systems.
Anomaly detection offers several potential benefits:
- Detection of unknown attacks: Anomaly detection can identify attacks that don’t have specific signatures, including zero-day attacks.
- Reduced false positives: Anomaly detection systems are generally less prone to false positives compared to signature-based systems.
- Adaptability to changing environments: Anomaly detection algorithms can adapt to changes in network traffic patterns, making them more effective in dynamic environments.
NIDS Deployment and Configuration
Deploying a NIDS involves several steps, including selecting the right NIDS for your network, configuring it, and placing it strategically to maximize its effectiveness. It is crucial to understand the different aspects of deployment and configuration to ensure your NIDS provides robust security for your network.
NIDS Deployment Steps
NIDS deployment requires a methodical approach to ensure successful integration into your network environment. Here are the key steps involved:
- Network Assessment: The first step is to assess your network infrastructure, identifying critical assets, traffic patterns, and potential vulnerabilities. This analysis helps determine the appropriate NIDS type and deployment strategy.
- NIDS Selection: Based on your network assessment, choose a NIDS that aligns with your requirements. Consider factors like performance, features, ease of management, and compatibility with your existing infrastructure.
- Hardware and Software Setup: Install the chosen NIDS on dedicated hardware or a virtual machine, ensuring sufficient processing power and memory for optimal performance. Configure the NIDS according to your network topology and security policies.
- Network Integration: Integrate the NIDS into your network by configuring network devices like switches and routers to forward traffic to the NIDS for inspection. This may involve setting up SPAN ports or mirroring traffic to the NIDS.
- Rule Configuration: Define a set of rules that define the network traffic patterns you want to monitor and detect. These rules can be based on specific protocols, ports, signatures, and other characteristics.
- Testing and Optimization: After deployment, thoroughly test the NIDS by simulating various attack scenarios to ensure it correctly identifies and responds to threats. Adjust the configuration as needed to optimize performance and detection capabilities.
- Monitoring and Maintenance: Regularly monitor the NIDS for alerts, logs, and performance metrics. Keep the NIDS updated with the latest security signatures and patches to maintain its effectiveness against emerging threats.
NIDS Placement Considerations
The placement of a NIDS significantly impacts its effectiveness. Here are some key considerations for optimal placement:
- Network Segmentation: Place NIDS at strategic points within your network, such as at the perimeter, between network segments, or in front of critical assets. This approach allows you to monitor traffic flows and detect threats at various stages of the network.
- Traffic Volume: Consider the traffic volume at the chosen placement point. High-traffic areas may require a more powerful NIDS to handle the workload efficiently.
- Performance Impact: Ensure that placing the NIDS does not significantly impact network performance. If the NIDS is too slow, it may hinder legitimate traffic and compromise network availability.
NIDS Configuration Best Practices
Proper configuration is essential for ensuring the NIDS operates effectively and does not generate excessive false positives. Here are some best practices for NIDS configuration:
- Rule Optimization: Carefully craft and refine the NIDS rules to strike a balance between comprehensive threat detection and minimizing false positives.
- Alert Thresholds: Set appropriate alert thresholds to avoid overwhelming security personnel with excessive notifications. Configure the NIDS to prioritize alerts based on severity and potential impact.
- Logging and Reporting: Configure the NIDS to generate detailed logs and reports for analysis and incident response. This information can be used to identify trends, investigate security incidents, and improve security posture.
- Integration with Security Tools: Integrate the NIDS with other security tools, such as intrusion prevention systems (IPS), firewalls, and SIEM systems, to create a comprehensive security solution.
NIDS Deployment Challenges
Deploying a NIDS effectively can present some challenges:
- Performance Impact: NIDS can sometimes impact network performance, especially when handling high traffic volumes. Choosing a powerful NIDS and optimizing its configuration can mitigate this issue.
- False Positives: NIDS can sometimes generate false positives, leading to unnecessary alerts and potentially disrupting operations. Careful rule configuration and ongoing monitoring can help minimize false positives.
- Complexity: Configuring and managing a NIDS can be complex, requiring specialized knowledge and expertise. Consider using a managed NIDS service or consulting with security professionals for assistance.
- Evasion Techniques: Attackers are constantly developing new evasion techniques to bypass NIDS detection. It is crucial to stay informed about emerging threats and update the NIDS with the latest security signatures and patches.
Benefits of NIDS
Implementing a NIDS in your cybersecurity strategy offers significant advantages that can enhance your threat detection and response capabilities, strengthen your security posture, and ensure compliance with relevant regulations.
Enhanced Threat Detection
NIDS are designed to detect malicious activity by analyzing network traffic for suspicious patterns. They provide a comprehensive overview of network activity, allowing security professionals to identify potential threats that might otherwise go unnoticed. By analyzing network traffic in real-time, NIDS can detect a wide range of attacks, including:
- Exploits: NIDS can detect attempts to exploit vulnerabilities in systems and applications, such as buffer overflows and SQL injection attacks.
- Malware: They can identify malicious software, such as viruses, worms, and trojans, by recognizing their characteristic patterns in network traffic.
- Denial-of-Service (DoS) Attacks: NIDS can detect and block DoS attacks that aim to overwhelm a system with traffic, making it unavailable to legitimate users.
- Unauthorized Access: NIDS can detect unauthorized access attempts, such as brute-force attacks and unauthorized logins.
Improved Incident Response
NIDS play a crucial role in incident response by providing early warning of attacks and enabling rapid containment. By detecting suspicious activity in real-time, NIDS can trigger alerts that notify security teams of potential threats. This allows security professionals to investigate incidents promptly and take appropriate action to mitigate the damage.
Compliance and Regulatory Requirements
In many industries, organizations are required to comply with specific regulations and standards that mandate the implementation of security controls, including intrusion detection systems. NIDS can help organizations meet these compliance requirements by providing evidence of their security posture and demonstrating their ability to detect and respond to threats.
For example, the Payment Card Industry Data Security Standard (PCI DSS) requires organizations to implement intrusion detection and prevention systems to protect cardholder data. NIDS can help organizations comply with this requirement by providing a layer of security that monitors network traffic for suspicious activity.
Limitations and Considerations
While NIDS offers valuable protection, it’s crucial to understand its limitations and how it fits within a comprehensive security strategy. NIDS isn’t a silver bullet and may not be suitable for all situations.
NIDS rely on analyzing network traffic patterns and signatures, which can lead to false positives. This occurs when the NIDS flags legitimate traffic as malicious, causing unnecessary alerts and potential disruptions.
False Positives, What is nids in cyber security
False positives can be a significant problem with NIDS, as they can overwhelm security teams with irrelevant alerts, leading to alert fatigue and potentially missing genuine threats.
- Signature Mismatches: NIDS signatures are based on known attack patterns. When new attack techniques emerge, the NIDS might not have a signature for them, resulting in false negatives (missing attacks) or false positives (misidentifying legitimate traffic).
- Network Traffic Complexity: NIDS analyze large volumes of network traffic. This can lead to false positives when complex traffic patterns, like those generated by legitimate applications, resemble attack patterns.
- Configuration Errors: Incorrectly configured NIDS rules or thresholds can trigger false positives.
Performance Impacts
NIDS can impact network performance by consuming network bandwidth and processing resources.
- High Traffic Volumes: Analyzing large amounts of network traffic can strain NIDS resources, potentially impacting network latency and performance.
- Intrusive Monitoring: NIDS often need to inspect all network traffic, which can add overhead and slow down network operations.
- Resource Consumption: NIDS require processing power and memory, which can impact the performance of other network devices or applications.
Comparison with Other Security Tools
NIDS are part of a layered security approach and work best when integrated with other security tools.
- Firewalls: Firewalls act as a first line of defense, blocking unauthorized access to the network. They work at the network layer and are typically used for perimeter security. NIDS, on the other hand, operate at the application layer and analyze traffic patterns for malicious activity.
- Intrusion Prevention Systems (IPS): IPS are similar to NIDS but also have the capability to block malicious traffic in real-time. They work by analyzing network traffic and taking proactive steps to prevent attacks.
- Endpoint Security: Endpoint security tools focus on protecting individual devices, such as workstations and servers. They use techniques like antivirus software, anti-malware, and host-based intrusion detection to prevent and detect threats at the endpoint level.
Situations Where NIDS May Not Be Effective
NIDS are most effective in identifying known attacks, but they may not be suitable for all security scenarios.
- Zero-Day Attacks: NIDS rely on signatures, which means they may not be able to detect new attacks (zero-day attacks) for which signatures are not yet available.
- Encrypted Traffic: NIDS cannot analyze encrypted traffic without decrypting it. This poses a challenge for securing modern networks, where encryption is becoming increasingly common.
- Internal Threats: NIDS are primarily designed to detect external threats. They may not be effective in detecting attacks originating from within the network, such as those launched by malicious insiders.
Examples of NIDS Technologies
Now that you understand the basics of NIDS, let’s explore some popular and widely used NIDS solutions. These solutions come in both software and hardware forms, offering various features and deployment options to fit different security needs.
Popular NIDS Solutions
Here’s a table highlighting some notable NIDS solutions, showcasing their key features and deployment options:
| Vendor | Product Name | Features | Deployment Options |
|---|---|---|---|
| Snort | Snort | Open-source, signature-based, anomaly detection, protocol analysis, intrusion prevention, real-time traffic analysis | Software, hardware appliances, virtual machines |
| Suricata | Suricata | Open-source, high-performance, signature-based, anomaly detection, protocol analysis, intrusion prevention | Software, hardware appliances, virtual machines |
| Bro | Bro | Open-source, network security monitoring, protocol analysis, anomaly detection, flow analysis, real-time reporting | Software, virtual machines |
| Cisco | Cisco Intrusion Detection System (IDS) | Proprietary, signature-based, anomaly detection, protocol analysis, intrusion prevention, network forensics | Hardware appliances, virtual machines |
| Fortinet | FortiGate | Proprietary, unified threat management (UTM), signature-based, anomaly detection, intrusion prevention, firewall, VPN | Hardware appliances, virtual machines |
| IBM | QRadar | Proprietary, security information and event management (SIEM), intrusion detection, log analysis, threat intelligence, vulnerability assessment | Software, hardware appliances, cloud-based |
| Trend Micro | Deep Security | Proprietary, endpoint security, intrusion prevention, anti-malware, vulnerability assessment, application control | Software, virtual machines, cloud-based |
So, there you have it! NIDS is like your network’s personal bodyguard, keeping a watchful eye on everything that’s going on. It’s not perfect, but it’s a powerful tool in your cybersecurity arsenal, giving you a heads-up when trouble is brewing. Just remember, NIDS is just one part of a larger security strategy, so don’t get too cocky, and always stay vigilant!
FAQ
What are some common examples of NIDS technologies?
Popular NIDS solutions include Snort, Suricata, and Bro. These are like the top dogs in the security world, known for their robust features and wide-scale use.
How does NIDS differ from an Intrusion Prevention System (IPS)?
While NIDS acts as a watchdog, alerting you to threats, an IPS is more proactive, blocking suspicious traffic before it can cause damage. Think of it as the difference between a security guard who yells at a thief and a security guard who physically stops the thief from entering the building.
Can NIDS be used to protect personal computers?
While NIDS is primarily used for networks, there are some specialized tools designed for personal computers. However, most home users rely on antivirus software and firewalls for protection.
Is NIDS a foolproof solution?
No, NIDS isn’t a magic bullet. It’s a powerful tool, but it has limitations. It can sometimes miss threats or generate false alarms, so it’s important to use it alongside other security measures.






