Is Security Onion a SIEM? This question arises frequently as organizations seek comprehensive security solutions. While not a traditional commercial SIEM, Security Onion offers a powerful open-source platform that incorporates many SIEM functionalities. It excels in collecting, analyzing, and responding to security events, providing a robust defense against evolving threats.
Security Onion’s architecture, built on a foundation of open-source tools like Snort, Suricata, and Elasticsearch, empowers organizations to build a comprehensive security monitoring system. Its capabilities extend beyond basic intrusion detection, offering advanced features like log analysis, threat hunting, and incident response.
Security Onion Overview
Security Onion is an open-source, free, and comprehensive security distribution designed for intrusion detection, incident response, and security monitoring. It is a Linux distribution that bundles a variety of security tools, including network traffic analysis, intrusion detection, and log management.
Core Functionalities of Security Onion
Security Onion offers a suite of capabilities that cater to security professionals across various domains. These include:
- Network Intrusion Detection and Prevention: Security Onion utilizes tools like Snort, Suricata, and Bro to detect and prevent malicious network activity. These tools analyze network traffic in real-time, identifying suspicious patterns and potential threats.
- Log Management and Analysis: Security Onion incorporates tools like Elasticsearch, Logstash, and Kibana (ELK stack) to collect, index, and analyze security logs from various sources within your network. This centralized log management system facilitates comprehensive threat investigation and incident response.
- Security Information and Event Management (SIEM): Security Onion functions as a rudimentary SIEM, consolidating security data from multiple sources and providing a platform for correlation and analysis. This enables security teams to gain a holistic view of security events and potential threats across the network.
- Threat Intelligence Integration: Security Onion can integrate with threat intelligence feeds, allowing it to correlate observed events with known indicators of compromise (IOCs). This integration enhances threat detection capabilities and facilitates timely response to emerging threats.
- Forensics and Incident Response: Security Onion provides tools and workflows to assist in incident response and forensic analysis. It captures and stores network traffic, enabling security teams to reconstruct attack timelines and gather evidence for incident investigations.
Architecture and Key Components
Security Onion’s architecture is designed to be robust and scalable, catering to various network sizes and security needs. It leverages a combination of open-source tools and technologies, organized into distinct layers:
- Network Tap/Span Port: Network traffic is captured through a tap or span port, providing a mirror image of the network traffic without disrupting the network’s primary function.
- Packet Capture and Analysis: Security Onion employs tools like tcpdump and Wireshark for capturing network packets and performing initial analysis. This data is then processed by intrusion detection systems (IDS) for further analysis.
- Intrusion Detection Systems (IDS): Security Onion leverages multiple IDS engines, including Snort, Suricata, and Bro. These engines analyze network traffic for known attack signatures, suspicious patterns, and potential threats.
- Log Collection and Aggregation: Security Onion utilizes tools like rsyslog and syslog-ng to collect security logs from various network devices and systems. These logs are then aggregated and processed by the ELK stack for analysis and storage.
- ELK Stack: The ELK stack, comprising Elasticsearch, Logstash, and Kibana, serves as the central platform for log management and analysis. Elasticsearch stores the collected logs, Logstash preprocesses and enriches the data, and Kibana provides a user-friendly interface for visualization and analysis.
- Alerting and Reporting: Security Onion offers various alerting mechanisms, including email notifications, SMS alerts, and integration with external ticketing systems. It also provides reporting capabilities to generate comprehensive security reports and dashboards.
Primary Use Cases and Target Audience
Security Onion is designed to serve a wide range of use cases and audiences within the security domain. Here are some key areas where Security Onion excels:
- Network Security Monitoring: Security Onion is ideal for monitoring network traffic for suspicious activity, identifying potential threats, and gaining visibility into network behavior. It is commonly used in organizations of all sizes, from small businesses to large enterprises.
- Intrusion Detection and Prevention: Security Onion’s IDS capabilities enable organizations to detect and prevent known attacks and emerging threats. It is valuable for organizations that require robust security measures to protect their networks and critical assets.
- Incident Response: Security Onion provides tools and workflows to assist security teams in investigating security incidents, collecting evidence, and reconstructing attack timelines. This makes it an essential tool for incident response teams.
- Security Research and Development: Security Onion is used by security researchers and developers to test new security tools, analyze attack patterns, and contribute to the advancement of security technologies.
- Education and Training: Security Onion is an excellent platform for security professionals to learn and practice security analysis, intrusion detection, and incident response techniques. Its open-source nature allows for experimentation and hands-on experience.
SIEM Capabilities of Security Onion
Security Onion is a powerful open-source platform designed for security monitoring and incident response. While it offers a wide range of security tools, it also excels as a Security Information and Event Management (SIEM) system.
SIEM solutions are crucial for security teams to effectively analyze and manage security data from various sources, identify threats, and respond promptly to incidents. Security Onion’s robust SIEM capabilities make it a valuable asset for organizations of all sizes.
Log Collection and Aggregation
Security Onion provides a centralized platform for collecting and aggregating security logs from diverse sources, including:
- Network devices: Firewalls, intrusion detection systems (IDS), routers, switches
- Operating systems: Linux, Windows, macOS
- Security applications: Antivirus, endpoint detection and response (EDR), web application firewalls (WAF)
- Cloud services: AWS, Azure, Google Cloud
The platform supports various log formats, including syslog, CEF, and LEF, ensuring compatibility with a wide range of security tools. This centralized collection simplifies log management, enabling security teams to analyze and correlate events across different systems and applications.
Real-time Threat Detection
Security Onion leverages powerful open-source security tools, such as Snort, Suricata, and Bro, to detect malicious activities in real-time. These tools analyze network traffic and system logs, identifying suspicious patterns and potential threats.
- Signature-based detection: Snort and Suricata use predefined rules to identify known attack patterns and malware signatures. These rules are constantly updated to keep pace with evolving threats.
- Anomaly detection: Bro uses statistical analysis and behavioral modeling to identify unusual activities that may indicate an attack. This approach helps detect zero-day threats and attacks that evade traditional signature-based detection methods.
Security Onion’s real-time threat detection capabilities allow security teams to proactively identify and respond to threats before they cause significant damage.
Correlation and Analysis
Security Onion provides robust correlation and analysis capabilities to help security teams understand the context of security events and identify potential threats.
- Correlation rules: Security Onion allows users to define correlation rules that trigger alerts when specific events occur in a sequence or combination. These rules can help identify sophisticated attacks that involve multiple stages or systems.
- Search and filtering: The platform provides powerful search and filtering capabilities to quickly find specific events and analyze patterns in security data. This enables security teams to investigate incidents and identify root causes.
- Dashboards and visualizations: Security Onion offers customizable dashboards and visualizations to provide a comprehensive overview of security events and trends. These dashboards help security teams identify critical security issues and monitor the overall security posture of their organization.
By correlating and analyzing security events, Security Onion helps security teams prioritize incidents, reduce false positives, and improve their overall incident response time.
Incident Response
Security Onion provides a comprehensive set of tools to help security teams investigate and respond to security incidents.
- Alerting and notifications: The platform supports various alert mechanisms, including email, SMS, and Slack notifications, to promptly notify security teams of potential threats.
- Incident tracking: Security Onion provides a built-in incident tracking system to manage and document security incidents. This helps security teams track the progress of investigations, document findings, and improve their overall incident response process.
- Forensics and analysis: Security Onion includes various tools for forensics and analysis, such as Wireshark and tcpdump, to help security teams investigate security incidents and collect evidence.
By providing a comprehensive set of incident response tools, Security Onion empowers security teams to quickly and effectively handle security incidents and minimize the impact of attacks.
Comparison with Other SIEM Solutions, Is security onion a siem
Security Onion, being an open-source solution, offers a cost-effective alternative to commercial SIEM solutions. While it lacks the advanced features and enterprise-grade support of commercial SIEMs, it provides a powerful and flexible platform for security monitoring and incident response.
- Features and capabilities: Security Onion offers a comprehensive set of SIEM features, including log collection, threat detection, correlation, analysis, and incident response. However, commercial SIEM solutions often provide more advanced features, such as machine learning, threat intelligence integration, and automated remediation.
- Scalability and performance: Security Onion is highly scalable and can handle large volumes of security data. However, commercial SIEM solutions may offer better performance and scalability for organizations with extremely high data volumes.
- Support and maintenance: Security Onion relies on a community-driven support model, which may not provide the same level of support as commercial SIEM solutions. Commercial SIEM solutions often offer dedicated support teams and enterprise-grade service level agreements (SLAs).
- Cost: Security Onion is a free and open-source solution, making it an attractive option for organizations with limited budgets. Commercial SIEM solutions can be expensive, with high licensing fees and ongoing maintenance costs.
The choice between Security Onion and commercial SIEM solutions depends on the specific needs and resources of an organization. Security Onion is an excellent choice for organizations seeking a cost-effective and powerful open-source SIEM solution, while commercial SIEM solutions may be more suitable for organizations with high security requirements and a larger budget.
Data Collection and Ingestion
Security Onion’s data collection and ingestion capabilities are crucial for its SIEM functionality. It leverages various methods to gather security data from diverse sources, ensuring comprehensive visibility across your network.
Data Collection Methods
Security Onion employs a range of methods to collect security data, including:
- Network Traffic Capture: Security Onion utilizes tools like Snort, Suricata, and Bro to capture network traffic and analyze it for suspicious activities. These tools are deployed as network intrusion detection systems (NIDS) and can capture data from various network interfaces, including physical and virtual network adapters.
- Log Collection: Security Onion can collect logs from various sources, including:
- Operating System Logs: Logs from operating systems like Windows, Linux, and macOS provide insights into system events, user activities, and security-related events.
- Security Software Logs: Logs from security software such as antivirus, firewalls, and intrusion prevention systems (IPS) offer valuable information about detected threats and security incidents.
- Application Logs: Logs from applications, including web servers, databases, and custom applications, can reveal potential vulnerabilities and security breaches.
- Cloud Platform Logs: Logs from cloud platforms like AWS, Azure, and Google Cloud provide insights into cloud resource usage, security events, and potential threats.
- Syslog Collection: Security Onion can collect syslog messages from various network devices, including routers, switches, and firewalls. These messages provide valuable information about network activity, security events, and device configurations.
- Data Source Integration: Security Onion can integrate with various data sources, including:
- Databases: Security Onion can collect data from databases such as MySQL, PostgreSQL, and MongoDB, enabling analysis of database events and potential security threats.
- Active Directory: Security Onion can integrate with Active Directory, providing visibility into user authentication, group membership, and other directory-related information.
- Other SIEMs: Security Onion can ingest data from other SIEMs, allowing for consolidation and correlation of security data from multiple sources.
Supported Data Formats and Protocols
Security Onion supports a wide range of data formats and protocols for data ingestion, ensuring compatibility with various security tools and data sources. Some of the supported formats and protocols include:
- Log Formats:
- Syslog: A widely used standard protocol for transmitting log messages over a network.
- CEF (Common Event Format): A standardized format for exchanging security events between different security devices and applications.
- LEEF (Log Event Extended Format): A format used by ArcSight for exchanging security events.
- JSON (JavaScript Object Notation): A lightweight data-interchange format used for transmitting structured data.
- Protocols:
- TCP: A connection-oriented protocol used for reliable data transmission.
- UDP: A connectionless protocol used for fast and efficient data transmission.
- HTTP: A protocol used for transmitting data over the World Wide Web.
Data Source Strengths and Limitations
The choice of data sources for Security Onion depends on the specific security needs and requirements of an organization. Each data source has its own strengths and limitations:
| Data Source | Strengths | Limitations |
|---|---|---|
| Network Traffic Capture | Provides comprehensive visibility into network activity, including malicious traffic and potential threats. Enables detection of network-based attacks and suspicious behavior. | High bandwidth requirements, potentially leading to performance issues. Requires careful configuration to avoid capturing unnecessary data. |
| Log Collection | Offers insights into system events, user activities, and security-related events. Can provide valuable information about detected threats and security incidents. | Can be overwhelming with large volumes of data. Requires careful analysis and correlation to identify meaningful insights. |
| Syslog Collection | Provides valuable information about network activity, security events, and device configurations. Can be used to monitor network health and performance. | Limited information compared to other data sources. Requires careful configuration to ensure proper logging and data collection. |
| Data Source Integration | Enables consolidation and correlation of security data from multiple sources. Provides a holistic view of security events and potential threats. | Can be complex to configure and manage. Requires careful planning and coordination to ensure data consistency and integrity. |
Alerting and Incident Response
Security Onion provides robust alerting and incident response capabilities, enabling users to detect and respond to potential security threats effectively. The platform leverages various tools and techniques to generate alerts based on suspicious activity, allowing security analysts to investigate and take appropriate actions.
Alert Configuration and Types
Security Onion offers a flexible and customizable alerting system. Users can define alerts based on specific events, patterns, or anomalies observed within the collected network traffic. This allows for tailoring the alerting system to meet the unique security needs of an organization.
- Snort Rules: Security Onion uses Snort, an open-source intrusion detection system (IDS), to analyze network traffic and generate alerts based on predefined rules. Snort rules can be customized or downloaded from online repositories to detect various threats, such as malware, exploits, and network reconnaissance attempts. The rules are configured within the Snort rule editor and are associated with specific alert actions.
- Suricata Rules: Similar to Snort, Suricata is another open-source IDS that Security Onion utilizes. Suricata rules, like Snort rules, are customizable and can be used to detect a wide range of threats. The Suricata rule editor allows users to define and manage their rules, similar to the Snort rule editor.
- Bro Scripts: Bro is a powerful network security monitoring tool that Security Onion integrates. Bro scripts can be used to analyze network traffic and generate alerts based on specific patterns or behaviors. These scripts provide flexibility in defining custom alerts and can be used to detect sophisticated attacks that might not be covered by traditional Snort or Suricata rules.
- Elasticsearch Queries: Security Onion utilizes Elasticsearch for storing and analyzing security data. Elasticsearch allows users to create custom queries to identify specific events or patterns within the collected data. These queries can be used to generate alerts based on specific criteria, such as unusual login attempts, suspicious file transfers, or unusual network activity.
Alert Actions
When an alert is triggered, Security Onion can perform various actions to notify security analysts and initiate incident response procedures. The platform offers a range of alert actions that can be customized to fit different security needs.
- Email Notifications: Security Onion can send email notifications to designated recipients when an alert is triggered. These emails can include details about the alert, such as the source and destination IP addresses, the time of the event, and the associated Snort or Suricata rule. This allows security analysts to be promptly notified of potential security threats.
- Syslog Logging: Security Onion can log alerts to a syslog server, providing a centralized record of security events. Syslog logging allows for aggregation and analysis of security data from multiple sources, including Security Onion itself. This provides a comprehensive view of security events across the network.
- Database Storage: Security Onion can store alert data in a database, such as MySQL or PostgreSQL. This allows for efficient storage and retrieval of alert information, enabling security analysts to perform detailed analysis and reporting. Database storage also enables the use of powerful query tools to extract insights from the alert data.
- Integration with Other Tools: Security Onion can integrate with other security tools, such as incident response platforms or security information and event management (SIEM) systems. This allows for seamless integration of alerts into existing security workflows and facilitates automated incident response actions.
Incident Response Workflow
Security Onion provides a structured workflow for incident response, helping security analysts to effectively investigate and mitigate security threats. The workflow typically involves the following steps:
- Alert Detection: The process starts with the detection of an alert, which can be triggered by Snort, Suricata, Bro scripts, or Elasticsearch queries.
- Alert Investigation: Once an alert is triggered, security analysts investigate the alert to gather more information about the potential threat. This includes analyzing the alert details, reviewing network traffic logs, and examining related system logs.
- Threat Assessment: Based on the investigation, security analysts assess the severity of the threat and determine the appropriate response. This may involve identifying the attacker, understanding the attack method, and determining the potential impact of the attack.
- Incident Response: Security analysts implement appropriate incident response actions based on the threat assessment. This may include blocking malicious IP addresses, isolating infected systems, or taking other steps to mitigate the threat.
- Post-Incident Analysis: After the incident is resolved, security analysts perform a post-incident analysis to understand the root cause of the attack and identify any vulnerabilities that may have been exploited. This information is used to improve security measures and prevent future attacks.
Analysis and Investigation
Security Onion provides a comprehensive set of tools and techniques for analyzing security events, enabling security analysts to delve deep into potential threats and conduct thorough investigations. This section explores the capabilities of Security Onion in this domain, highlighting its key features and functionalities.
Analyzing Security Events
Security Onion leverages various tools and techniques to analyze security events, including:
- Elasticsearch: Elasticsearch is a powerful search and analytics engine that provides a central repository for all collected security data. Security analysts can use Elasticsearch to query and analyze security events, identify patterns, and gain insights into potential threats.
- Kibana: Kibana is a visualization and dashboarding tool that complements Elasticsearch. Security analysts can use Kibana to create interactive dashboards, visualize security data, and gain a comprehensive understanding of security trends and anomalies.
- Snorby: Snorby is a web-based interface for managing and analyzing alerts generated by Snort. It allows security analysts to view alerts, investigate suspicious activity, and take appropriate actions.
- Bro: Bro is a network security monitoring tool that provides deep packet inspection capabilities. It can generate detailed logs and reports that provide valuable insights into network traffic patterns and potential security threats.
- Suricata: Suricata is a high-performance intrusion detection system that can be used to detect and analyze malicious activity. It provides a rich set of rules and signatures for identifying known threats and can be customized to detect emerging threats.
Facilitating Threat Hunting and Incident Investigation
Security Onion facilitates threat hunting and incident investigation through its comprehensive data collection and analysis capabilities.
- Threat Hunting: Security Onion allows security analysts to proactively search for potential threats by analyzing security data for unusual patterns and indicators of compromise (IOCs). The combination of Elasticsearch, Kibana, and other tools enables analysts to conduct complex searches and identify potential threats that might have otherwise gone unnoticed.
- Incident Investigation: In the event of a security incident, Security Onion provides the tools and data necessary for a thorough investigation. Analysts can use Snorby, Bro, and other tools to reconstruct the timeline of events, identify the source of the attack, and determine the impact of the incident. The detailed logs and reports generated by Security Onion provide valuable evidence for incident response and remediation.
Key Features and Functionalities of Security Onion’s Analysis Tools
| Tool | Features and Functionalities ||—|—|| Elasticsearch | Centralized data repository, powerful search and analytics capabilities, real-time data ingestion, supports various data formats, scalable architecture || Kibana | Visualization and dashboarding tool, interactive dashboards, customizable visualizations, data exploration and analysis, integration with Elasticsearch || Snorby | Web-based interface for managing and analyzing Snort alerts, alert filtering and categorization, incident investigation, customizable reports || Bro | Network security monitoring tool, deep packet inspection, protocol analysis, real-time traffic monitoring, log generation || Suricata | High-performance intrusion detection system, signature-based detection, custom rules, anomaly detection, real-time alerting |
Reporting and Visualization
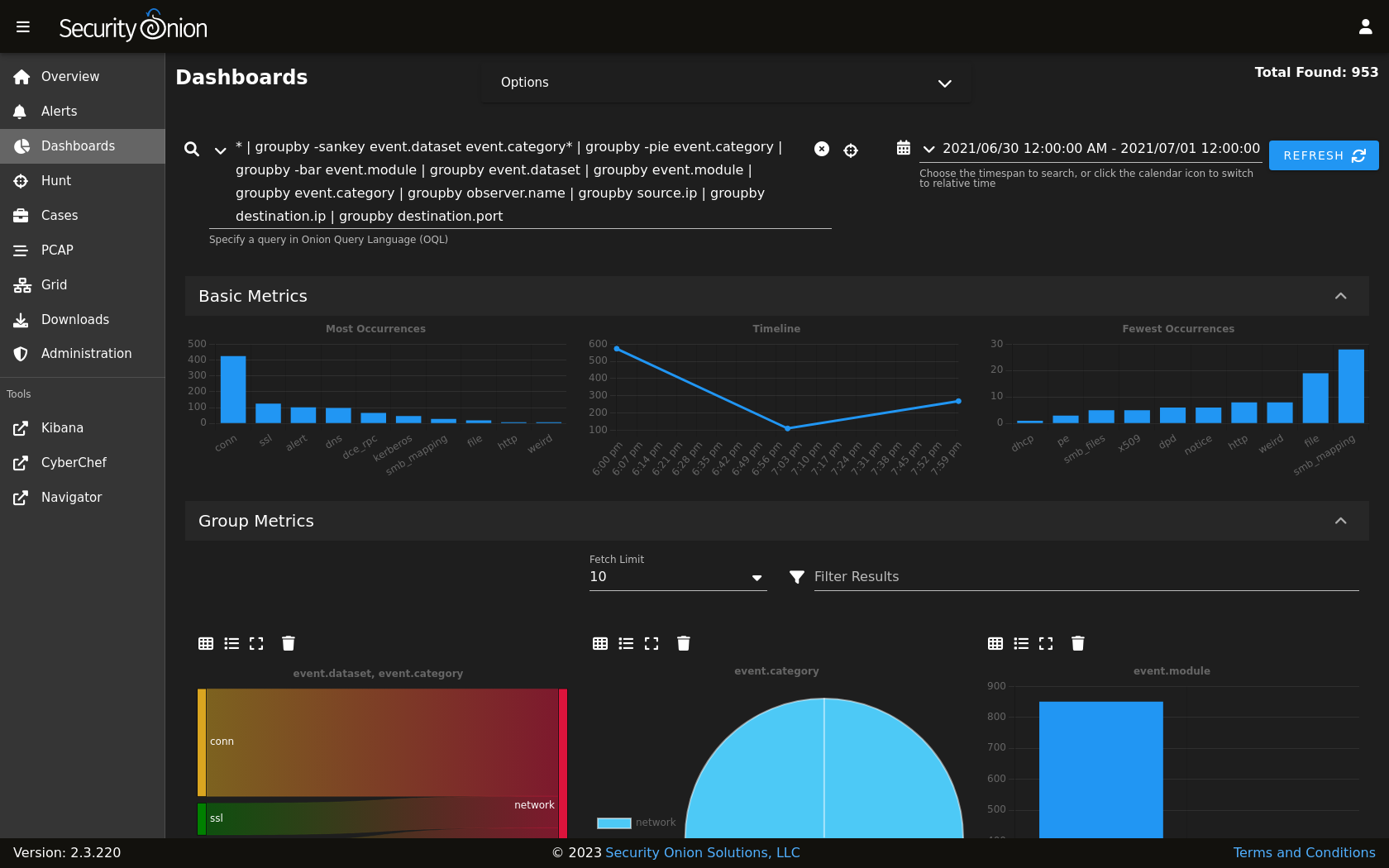
Security Onion offers robust reporting and visualization capabilities to facilitate comprehensive security analysis and incident investigation. It leverages various tools and technologies to provide insightful data representations, helping security analysts understand trends, identify anomalies, and make informed decisions.
Report Types and Relevance
Security Onion provides a diverse range of report types, each serving a specific purpose in security analysis. These reports offer valuable insights into various aspects of network security, enabling analysts to effectively monitor, investigate, and respond to security incidents.
- Network Traffic Analysis Reports: These reports provide insights into network traffic patterns, including bandwidth usage, top talkers, and protocol distribution. They help identify potential anomalies, excessive bandwidth consumption, or suspicious communication patterns.
- Security Event Logs Reports: These reports summarize security events from various sources, such as firewalls, intrusion detection systems (IDS), and host-based security tools. They help identify security incidents, track system vulnerabilities, and monitor security posture.
- Vulnerability Assessment Reports: These reports provide detailed information about identified vulnerabilities in systems and applications, including their severity, exploitability, and remediation recommendations. They help prioritize security patching and vulnerability management efforts.
- Incident Response Reports: These reports document the details of security incidents, including the timeline of events, affected systems, and mitigation actions taken. They help track incident response activities, analyze incident trends, and improve future response strategies.
- Custom Reports: Security Onion allows analysts to create custom reports based on specific requirements. This flexibility enables tailored reporting for specific security needs and facilitates in-depth analysis of specific data points.
Report Customization and Export
Security Onion provides various options for customizing and exporting reports to suit specific needs. This flexibility allows analysts to tailor reports for different audiences, including technical teams, management, and external stakeholders.
- Report Filtering: Security Onion enables filtering reports based on specific criteria, such as time range, event type, source IP address, or destination port. This allows analysts to focus on relevant data and generate targeted reports.
- Report Formatting: Reports can be formatted in various ways, including tabular, graphical, and textual formats. This enables analysts to choose the most appropriate format for presenting data effectively.
- Report Export Options: Reports can be exported in various formats, including PDF, CSV, and HTML. This allows analysts to share reports with others, integrate them into other systems, or archive them for future reference.
Integration and Extensibility

Security Onion is not a standalone system, but rather a powerful platform designed to work seamlessly with other security tools and platforms. This inherent flexibility enhances its capabilities and allows for a tailored security posture that aligns with specific organizational needs.
Integration with Other Security Tools
Security Onion’s integration capabilities are a cornerstone of its strength. It can integrate with various security tools and platforms, facilitating data sharing, collaborative analysis, and automated response actions. This interoperability enhances the overall security posture by creating a cohesive ecosystem where different tools work in concert to address security challenges.
- SIEMs: Security Onion can integrate with other SIEMs, such as Splunk, Elasticsearch, and Logstash, to share data and leverage their analysis capabilities. This allows for a consolidated view of security events across multiple platforms.
- Threat Intelligence Platforms: Integrating with threat intelligence platforms like MISP or OpenCTI enables Security Onion to enrich its analysis with external threat information, improving its ability to identify and respond to known threats.
- Vulnerability Scanners: Integrating with vulnerability scanners like Nessus or OpenVAS allows Security Onion to correlate vulnerability information with security events, providing a comprehensive view of potential security risks.
- Incident Response Platforms: Security Onion can integrate with incident response platforms like TheHive or Phantom to automate incident response tasks, such as containment and remediation, based on detected threats.
- Cloud Security Platforms: Security Onion can be deployed in cloud environments and integrate with cloud security platforms like AWS GuardDuty or Azure Security Center, providing a unified view of security events across on-premises and cloud infrastructure.
Plugins and Extensions
Security Onion boasts a vibrant community that actively develops and maintains plugins and extensions, extending its functionality to meet specific security needs. These plugins and extensions are typically open-source and freely available, fostering collaboration and innovation within the Security Onion ecosystem.
- Custom Alerts and Rules: Plugins can be developed to create custom alerts and rules tailored to specific security threats or organizational policies. This allows for proactive detection of emerging threats and ensures timely response.
- Data Enrichment: Plugins can be used to enrich data collected by Security Onion with external information, such as threat intelligence feeds, network context, or asset information. This provides deeper insights into security events and facilitates more accurate analysis.
- Integration with Third-Party Tools: Plugins can be developed to integrate Security Onion with specific third-party tools, such as security orchestration and automation platforms, or custom scripts for automated response actions.
- Visualization and Reporting: Plugins can enhance Security Onion’s reporting and visualization capabilities, allowing for customized dashboards, reports, and visualizations tailored to specific security needs.
Integration Points and Use Cases
| Tool | Integration Points | Use Cases |
|---|---|---|
| Splunk | Syslog, Elasticsearch | Centralized logging and analysis, correlation of security events across multiple platforms. |
| MISP | Threat intelligence feeds | Enrichment of security events with threat intelligence, identification of known threats. |
| Nessus | Vulnerability scan data | Correlation of vulnerability information with security events, prioritization of security risks. |
| TheHive | Incident response platform | Automation of incident response tasks, such as containment and remediation. |
| AWS GuardDuty | Cloud security platform | Unified view of security events across on-premises and cloud infrastructure, detection of cloud-specific threats. |
Security Onion vs. Traditional SIEMs: Is Security Onion A Siem

Security Onion and traditional SIEMs are both essential tools for security monitoring and incident response. They differ significantly in their approach, features, and target audience. Understanding these differences can help you determine which solution best suits your organization’s needs.
Comparison of Security Onion and Traditional SIEMs
The following table provides a concise comparison of Security Onion and traditional SIEMs across key features:
| Feature | Security Onion | Traditional SIEM |
|---|---|---|
| Cost | Open-source and free | Commercial, often with licensing fees |
| Deployment | Virtual machine or physical server | On-premise or cloud-based |
| Scalability | Scalable with distributed deployments | Scalable, but may require additional hardware or licensing |
| Features | Focused on security monitoring, incident response, and threat hunting | Comprehensive security information management, including compliance, reporting, and analytics |
| Customization | Highly customizable with open-source tools and scripting | Limited customization, typically through configuration options |
| Support | Community-driven support forums and documentation | Vendor-provided support, often with varying levels of service |
Advantages of Security Onion
- Cost-effective: Security Onion is an open-source solution, making it significantly more affordable than commercial SIEMs. Organizations with limited budgets can leverage Security Onion to establish robust security monitoring capabilities without significant upfront investment.
- Flexibility and Customization: Security Onion’s open-source nature allows for extensive customization and integration with other tools. Security teams can tailor the solution to their specific needs and workflows, enhancing its effectiveness and efficiency.
- Community-Driven Support: A vibrant community of security professionals contributes to Security Onion’s development and provides support through forums and documentation. This collaborative approach ensures ongoing improvements and readily available resources for users.
Advantages of Traditional SIEMs
- Comprehensive Security Information Management: Traditional SIEMs offer a broader range of features beyond security monitoring, including compliance reporting, security analytics, and vulnerability management. They provide a centralized platform for managing security data and insights.
- Vendor Support: Commercial SIEMs come with vendor-provided support, offering technical assistance, updates, and troubleshooting. This can be crucial for organizations seeking a managed solution with guaranteed uptime and expertise.
- Scalability and Performance: Traditional SIEMs are designed for large-scale deployments and can handle vast amounts of data. They often leverage advanced technologies and architectures to ensure performance and scalability.
Disadvantages of Security Onion
- Complexity: Setting up and configuring Security Onion can be complex, requiring technical expertise in Linux, security tools, and open-source technologies. This can be a barrier for organizations with limited technical resources.
- Limited Support: While the community provides support, it may not be as comprehensive or readily available as vendor-provided support for commercial SIEMs. This can be challenging for organizations seeking immediate assistance or specialized expertise.
- Fewer Features: Security Onion focuses primarily on security monitoring and incident response. It may lack the comprehensive features of traditional SIEMs, such as compliance reporting, vulnerability management, and advanced analytics.
Disadvantages of Traditional SIEMs
- High Cost: Commercial SIEMs can be expensive, with upfront licensing fees, ongoing maintenance costs, and potentially additional fees for features or support.
- Limited Customization: Traditional SIEMs typically offer limited customization options, making it challenging to tailor the solution to specific needs and workflows. This can lead to inefficiencies and potential limitations in functionality.
- Vendor Lock-in: Relying on a commercial SIEM can lead to vendor lock-in, making it difficult to switch to alternative solutions in the future. This can limit flexibility and potentially increase costs over time.
Potential Use Cases for Security Onion
- Small and Medium-Sized Businesses (SMBs): Security Onion’s affordability and open-source nature make it an attractive option for SMBs with limited budgets and technical resources. It provides a cost-effective way to establish basic security monitoring and incident response capabilities.
- Organizations with Limited IT Staff: Security Onion’s community-driven support and extensive documentation can be beneficial for organizations with limited IT staff. It empowers them to manage and maintain the solution effectively.
- Threat Hunting and Advanced Security Analysis: Security Onion’s focus on security monitoring and incident response, combined with its customizable nature, makes it suitable for threat hunting and advanced security analysis. It allows security teams to investigate suspicious activity and identify potential threats in depth.
In conclusion, while Security Onion may not be a traditional commercial SIEM, it offers a compelling alternative for organizations seeking a powerful, open-source solution. Its comprehensive features, flexibility, and community support make it a valuable tool for security professionals seeking to enhance their threat detection and response capabilities. Whether you’re a small organization or a large enterprise, Security Onion provides a solid foundation for building a robust security monitoring system.
General Inquiries
Is Security Onion free to use?
Yes, Security Onion is an open-source platform and is completely free to use.
What are the system requirements for Security Onion?
Security Onion has specific hardware and software requirements. Refer to their official documentation for detailed information.
How does Security Onion compare to commercial SIEMs in terms of features?
Security Onion offers a wide range of SIEM features, including log collection, analysis, alerting, and incident response. While it may not have the same breadth of features as some commercial SIEMs, it provides a powerful open-source alternative.
Is Security Onion suitable for large enterprises?
Yes, Security Onion can be scaled to handle large volumes of security data. Its architecture allows for distributed deployment and integration with other security tools.






