How to link a GPO to a security group sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with practical worship guide style and brimming with originality from the outset.
Mastering the art of linking Group Policy Objects (GPOs) to security groups is essential for effectively managing user and computer settings within your organization. By understanding the relationship between these two fundamental components, you can leverage the power of GPOs to enforce security policies, configure software settings, and streamline system administration tasks. This guide will walk you through the process of linking GPOs to security groups, providing practical steps, illustrative examples, and best practices to ensure successful implementation.
Understanding GPOs and Security Groups
Group Policy Objects (GPOs) and security groups are fundamental components of Active Directory (AD) that play crucial roles in managing and controlling user and computer settings within a network. Understanding their relationship is essential for effective network administration.
Purpose of Group Policy Objects
GPOs are powerful administrative tools that define and enforce settings for users and computers within an AD domain. They enable administrators to centrally manage a wide range of configurations, including:
- User Settings: GPOs can control user preferences, such as desktop backgrounds, start menu configurations, and software installations. They also define user security settings, such as password complexity requirements and access permissions.
- Computer Settings: GPOs manage system configurations, including network settings, security policies, and software updates. They can enforce specific security configurations and ensure consistent system behavior across all computers in the domain.
GPOs are organized hierarchically within an AD domain, allowing for targeted application of settings to specific organizational units (OUs) or groups of users and computers. This hierarchical structure ensures flexibility and granular control over network configurations.
The Role of Security Groups
Security groups are fundamental to controlling access to resources within an AD domain. They act as containers for users and computers, allowing administrators to define and manage access permissions for various network resources.
- Resource Access Control: Security groups are used to define who can access specific resources, such as shared folders, printers, or applications. By adding users or computers to a security group, administrators can grant them access to the resources associated with that group.
- Simplified Management: Security groups streamline user and computer management by providing a central point for managing access permissions. Instead of assigning permissions individually, administrators can assign permissions to groups, which simplifies the process of managing access for multiple users or computers.
Relationship between GPOs and Security Groups
The relationship between GPOs and security groups is crucial for effective network administration. GPOs can be linked to security groups, allowing administrators to apply specific settings to users or computers based on their group membership.
The ability to link GPOs to security groups enables targeted application of policies based on user or computer roles and responsibilities.
This linking mechanism provides a powerful way to manage and control user and computer settings within an AD domain.
Linking a GPO to a Security Group
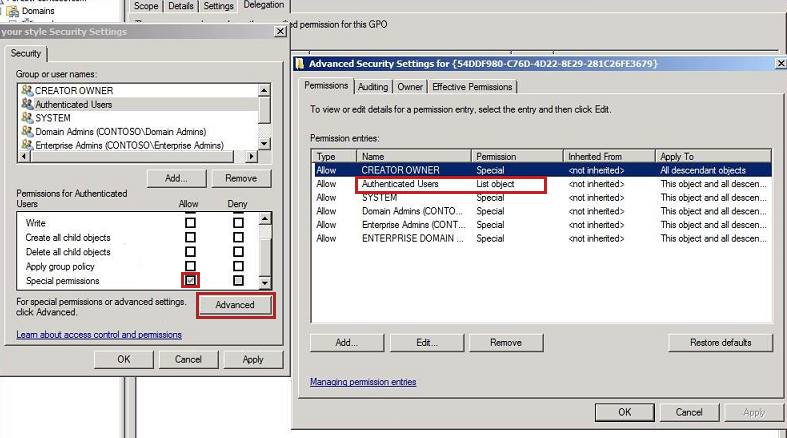
Linking a Group Policy Object (GPO) to a security group is a crucial step in applying specific settings and configurations to a defined group of users or computers within your Active Directory environment. This process ensures that the defined policies are enforced only on the targeted group, enhancing security and management efficiency.
Linking a GPO to a Security Group
To link a GPO to a security group, you need to navigate the Group Policy Management Console (GPMC) and perform a series of actions. Here’s a step-by-step guide:
- Open the GPMC by typing “gpmc.msc” in the Run dialog box or searching for it in the Windows search bar.
- In the GPMC, locate the domain or organizational unit (OU) where you want to apply the GPO.
- Right-click on the domain or OU and select “Create a GPO in this domain, and Link it here…”
- In the “New GPO” dialog box, enter a name for the GPO and click “OK.”
- The newly created GPO will appear in the “Group Policy Objects” container. Right-click on the GPO and select “Edit.”
- Configure the desired settings within the GPO. This could include user or computer configurations, software installations, security policies, or other settings.
- Once the GPO is configured, close the “Edit Group Policy” window.
- Navigate back to the domain or OU where the GPO is linked. Right-click on the GPO and select “Properties.”
- In the “Properties” window, select the “Security” tab.
- Click on “Add…” to add the security group you want to link the GPO to.
- In the “Select Users, Computers, or Groups” dialog box, enter the name of the security group and click “Check Names” to verify the group exists. Click “OK.”
- In the “Permissions for [GPO name]” window, select the desired permissions for the security group. These permissions will determine what actions the group members can perform on the GPO. For example, you might grant the group “Read” permissions to allow members to view the GPO settings, but not modify them.
- Click “Apply” and then “OK” to save the changes.
The security group you choose for the GPO should be appropriate for the specific policies you are applying. For example, if you are applying a policy to restrict access to certain files, you should link the GPO to a security group that contains only the users who should have access to those files.
Example: Linking a GPO to a Security Group, How to link a gpo to a security group
Let’s consider an example where you want to apply a GPO to a security group called “Marketing Team” to restrict access to a specific folder on a shared network drive.
- Create a new GPO called “Restrict Marketing Folder Access” and link it to the OU where the “Marketing Team” group resides.
- In the “Restrict Marketing Folder Access” GPO, navigate to “Computer Configuration” > “Policies” > “Windows Settings” > “Security Settings” > “File System.”
- Right-click on “File System” and select “Add File…”
- Enter the path to the shared network folder that you want to restrict access to, for example, “\\server\marketing_files.” Click “OK.”
- In the “Permissions for \\server\marketing_files” window, select “Advanced.”
- Click “Disable inheritance” and then “Remove all inherited permissions.”
- Click “Add…” to add the “Marketing Team” group.
- In the “Permissions for \\server\marketing_files” window, grant the “Marketing Team” group “Read” permissions to allow them to access the folder, but not modify the files. Click “OK.”
- Close the “Edit Group Policy” window and save the changes to the GPO.
- In the “Properties” window of the “Restrict Marketing Folder Access” GPO, select the “Security” tab and add the “Marketing Team” group. Grant the group “Read” permissions to allow them to view the GPO settings, but not modify them.
Now, only members of the “Marketing Team” group will have read-only access to the “marketing_files” folder on the shared network drive.
Choosing the Appropriate Security Group
The security group you link the GPO to is crucial. You should carefully consider the following factors when choosing a security group:
- Scope of the policy: The security group should contain only the users or computers that the policy applies to.
- Security considerations: Ensure the security group is appropriately configured to minimize security risks. For example, avoid granting excessive permissions to the group.
- Administrative convenience: Choose a security group that is easy to manage and update. For example, you might use an existing security group that already contains the appropriate users or computers.
Applying GPO Settings to Users and Computers
Group Policy Objects (GPOs) are applied to users and computers based on their membership in security groups. This means that the settings defined in a GPO will only be applied to users and computers that are members of the security groups linked to that GPO.
Applying GPOs to Users and Computers Based on Security Groups
GPOs are applied to users and computers based on their membership in security groups. When a user or computer logs in, the system checks the security groups the user or computer is a member of. The system then applies all GPOs linked to those security groups.
Methods of Applying GPOs
GPOs can be applied at different levels within the Active Directory domain hierarchy. The most common methods are:
- Site Level: GPOs applied at the site level are applied to all users and computers within the site. This is the broadest level of application.
- Domain Level: GPOs applied at the domain level are applied to all users and computers within the domain. This is a more targeted level of application than the site level.
- Organizational Unit (OU) Level: GPOs applied at the OU level are applied to all users and computers within that specific OU. This is the most targeted level of application, allowing for fine-grained control over GPO application.
Order of Precedence for Multiple GPOs
When multiple GPOs are applied to a user or computer, the order of precedence determines which GPO settings take effect. The order of precedence is as follows:
- Local Computer Policy: This is the policy applied directly to the computer. It has the highest precedence.
- Site GPOs: Site GPOs are applied next, followed by domain GPOs, and then OU GPOs.
- OU GPOs: GPOs applied at the OU level are applied next, with the most specific OU taking precedence over less specific OUs.
- Domain GPOs: Domain GPOs are applied after site and OU GPOs.
In cases where multiple GPOs have conflicting settings, the GPO with the highest precedence will take effect.
Common GPO Settings and Security Groups
Linking GPOs to security groups is a powerful way to manage user and computer access and behavior. By associating specific GPO settings with targeted groups, administrators can implement policies that are tailored to the needs of different user roles or departments.
Common GPO Settings and Their Applications
This section examines some common GPO settings that are often linked to security groups, along with their purposes and potential applications.
| Setting | Purpose | Effect on User or Computer Behavior | Example Security Groups |
|---|---|---|---|
| Password Policy | Enforces password complexity requirements, minimum length, and expiration policies. | Users are required to create passwords that meet specific criteria and change them regularly. | Domain Users, Administrators, Help Desk Staff |
| Software Installation | Manages the installation and removal of applications on user workstations. | Users can only install or uninstall applications that are explicitly allowed or blocked by the policy. | Engineering Team, Sales Department, Marketing Team |
| User Rights Assignment | Controls user privileges and access to system resources. | Users are granted or denied specific rights, such as the ability to log in remotely, run specific programs, or access system files. | Administrators, Developers, System Operators |
| Network Access | Restricts access to specific network resources, such as shared folders, printers, or websites. | Users can only access resources that are explicitly allowed by the policy. | Sales Team, Finance Department, Human Resources |
| Security Options | Configures security settings, such as firewall rules, account lockout policies, and auditing options. | Enhances system security by controlling network access, account access attempts, and system events. | Domain Controllers, Servers, Workstations |
Best Practices for Linking GPOs to Security Groups
Linking Group Policy Objects (GPOs) to security groups is a fundamental practice in managing Active Directory environments. It allows for the efficient application of settings to specific groups of users and computers, ensuring a streamlined and controlled approach to policy management. However, designing and implementing GPOs effectively requires adherence to best practices to maximize their effectiveness and minimize potential issues.
Designing and Implementing GPOs Linked to Security Groups
The design and implementation of GPOs linked to security groups are crucial for achieving desired outcomes. To ensure success, it’s essential to follow these best practices:
- Define Clear Objectives: Before creating a GPO, clearly define its purpose and the specific settings it should apply. This helps ensure that the GPO effectively addresses the desired outcomes.
- Use Granular Security Groups: Create specific security groups that accurately represent the users or computers that need to be targeted by the GPO. This helps ensure that the GPO applies only to the intended recipients.
- Employ Least Privilege Principle: Apply the least privilege principle when configuring GPO settings. Grant only the necessary permissions to users and computers, minimizing potential security risks.
- Prioritize Group Policy Inheritance: Leverage group policy inheritance to apply settings to nested groups. This helps streamline policy management and reduces the need to create multiple GPOs for similar settings.
- Avoid Overlapping GPOs: Carefully manage the order of GPOs linked to security groups. Avoid overlapping settings, as conflicts can arise and lead to unpredictable behavior.
- Utilize Group Policy Preferences: Consider using Group Policy Preferences to customize settings for specific users or computers. This offers greater flexibility in applying settings and can reduce the need for complex scripts or manual configuration.
- Document GPO Settings: Maintain comprehensive documentation for each GPO, outlining its purpose, settings, and linked security groups. This documentation serves as a valuable reference for troubleshooting and future updates.
Testing and Monitoring GPO Changes
Testing and monitoring are essential steps in the lifecycle of any GPO. This ensures that the GPO functions as intended and that any changes do not negatively impact users or computers.
- Implement a Testing Environment: Before deploying a GPO to production, test it thoroughly in a dedicated test environment. This allows for the identification and resolution of any potential issues before they affect users in the production environment.
- Monitor GPO Application: Utilize tools like Group Policy Results (GPR) or Event Viewer to monitor the application of GPOs. This helps identify any failures or unexpected behavior, enabling prompt resolution.
- Track GPO Changes: Maintain a log of all GPO changes, including dates, settings modifications, and responsible administrators. This log serves as a valuable record for troubleshooting and auditing purposes.
Documenting and Communicating GPO Changes
Proper documentation and communication about GPO changes are crucial for ensuring that users and administrators are aware of any policy updates.
- Maintain a GPO Knowledge Base: Establish a central repository for all GPO documentation, including purpose, settings, linked security groups, and testing results. This knowledge base provides a valuable resource for troubleshooting and understanding GPOs.
- Communicate GPO Changes to Users: Inform users about any changes to GPOs that may affect their workstations or applications. This communication can be delivered through email, internal messaging platforms, or documentation updates.
- Train Administrators on GPO Management: Provide comprehensive training to administrators on GPO management practices. This ensures that they understand the complexities of GPOs and can effectively manage them.
Troubleshooting GPO and Security Group Issues
Linking Group Policy Objects (GPOs) to security groups is a fundamental aspect of managing user and computer settings in an Active Directory environment. However, various issues can arise during this process, hindering the successful application of GPO settings. This section delves into common problems encountered while linking GPOs to security groups, providing troubleshooting steps to resolve them and discussing the use of Group Policy Resultant Set of Policy (RSoP) to diagnose GPO application issues.
Common Problems When Linking GPOs to Security Groups
Several factors can contribute to problems when linking GPOs to security groups. The following points highlight common issues:
- Incorrect Security Group Selection: Ensuring that the selected security group accurately represents the intended target users or computers is crucial. If the wrong group is chosen, the GPO settings will not apply to the desired recipients.
- Conflicting GPOs: Multiple GPOs linked to the same security group can lead to conflicting settings. This occurs when different GPOs attempt to configure the same setting with conflicting values. For instance, one GPO might configure a specific network drive, while another might disable network drive mapping altogether.
- GPO Inheritance and Blocking: GPO inheritance allows settings to be applied from parent containers to child containers. However, blocking inheritance can prevent GPOs from applying to certain objects. This can happen if a GPO is linked at a higher organizational unit (OU) level and then inheritance is blocked at a lower OU level.
- Security Group Membership: Users or computers must be members of the security group to which the GPO is linked. If a user or computer is not a member of the group, the GPO settings will not apply to them.
- GPO Processing Order: The order in which GPOs are processed can affect the final settings applied. If a GPO with higher priority is processed after a GPO with lower priority, the settings from the higher-priority GPO might override the settings from the lower-priority GPO.
- GPO Filtering: GPO filtering allows administrators to specify conditions that determine whether a GPO applies to a specific user or computer. If the filtering criteria are not configured correctly, the GPO might not apply to the intended recipients.
- Group Policy Extension Issues: Group Policy extensions are used to extend the functionality of Group Policy. If an extension is not installed correctly or is incompatible with the operating system, it can cause GPO application issues.
Troubleshooting Steps
Troubleshooting GPO and security group issues requires a systematic approach. The following steps can be used to diagnose and resolve common problems:
- Verify Security Group Membership: Ensure that the users or computers intended to receive the GPO settings are members of the security group to which the GPO is linked. This can be checked using Active Directory Users and Computers (ADUC).
- Review GPO Linking: Verify that the GPO is linked to the correct security group and that the linking order is appropriate. Ensure that inheritance is not blocked at the OU level where the GPO is linked.
- Check for Conflicting GPOs: Identify any other GPOs that might be linked to the same security group or that might apply to the same users or computers. Check for conflicting settings between these GPOs.
- Examine GPO Filtering: Review the GPO filtering settings to ensure that they are configured correctly and that they do not prevent the GPO from applying to the intended recipients.
- Analyze Group Policy Resultant Set of Policy (RSoP): RSoP is a powerful tool that allows administrators to analyze the GPOs that apply to a specific user or computer. RSoP can help identify conflicts, inheritance issues, and other problems that might prevent GPO settings from being applied.
- Review Event Logs: Examine the Group Policy event logs in the Event Viewer for errors or warnings related to GPO application. These logs can provide valuable information about the cause of the problem.
- Test GPO Settings: After making changes to GPO settings or resolving issues, test the changes to ensure that the GPO settings are applied correctly. This can be done by logging in as a user or computer that is subject to the GPO and verifying that the expected settings are in place.
Using Group Policy Resultant Set of Policy (RSoP)
RSoP is a valuable tool for diagnosing GPO application issues. It allows administrators to see the effective GPO settings for a specific user or computer. RSoP displays the GPOs that apply to the target object, the order in which they are processed, and the final settings that are applied.To use RSoP, follow these steps:
- Open the Group Policy Management Console (GPMC).
- Select the “Resultant Set of Policy” (RSoP) option from the GPMC menu.
- Select the user or computer for which you want to analyze GPO settings.
- Click “Analyze.”
RSoP will then display a detailed report of the GPO settings that apply to the selected user or computer. This report can help identify conflicts, inheritance issues, and other problems that might prevent GPO settings from being applied.
RSoP is a crucial tool for troubleshooting GPO application issues. It provides valuable insights into the GPO settings that apply to a specific user or computer, enabling administrators to diagnose and resolve problems effectively.
In conclusion, linking GPOs to security groups empowers administrators to fine-tune user and computer configurations, ensuring consistent policies and streamlined management. By carefully choosing the appropriate security groups for your GPOs, testing changes thoroughly, and documenting your configurations, you can achieve a robust and secure IT environment. Remember, continuous monitoring and troubleshooting are essential to address any potential issues and maintain optimal system performance.
Essential Questionnaire: How To Link A Gpo To A Security Group
What happens if a user is a member of multiple security groups that have linked GPOs?
The GPOs are applied in a specific order of precedence, with the most restrictive GPO taking priority. Typically, the order is: Local Computer Policy, Site Policy, Domain Policy, and Organizational Unit (OU) Policy. The GPO applied at the most specific level (e.g., OU) will override policies set at higher levels.
Can I link a GPO to multiple security groups?
Yes, you can link a single GPO to multiple security groups. This allows you to apply the same settings to users or computers that belong to different groups.
What are some common GPO settings that are often linked to security groups?
Some common settings include: Software Installation, User Rights Assignment, Folder Redirection, Network Drive Mapping, Security Options, and Script Execution.






