How to sell cyber security – How to sell cybersecurity is a question that many businesses are grappling with. In a world where cyber threats are constantly evolving, businesses need to be proactive in protecting themselves. This guide will provide you with the knowledge and tools you need to effectively sell cybersecurity solutions to your target audience.
Understanding the cybersecurity market, identifying your ideal customer, and crafting a compelling value proposition are crucial steps in developing a successful sales strategy. By focusing on the specific needs and pain points of your target audience, you can build trust and credibility, ultimately leading to increased sales.
Understanding the Cybersecurity Market

The cybersecurity market is a rapidly growing industry, driven by the increasing reliance on technology and the growing sophistication of cyber threats. Understanding the key challenges, trends, and solutions in this market is crucial for businesses to effectively protect their assets and ensure their continued operations.
Key Cybersecurity Challenges
Cybersecurity challenges are constantly evolving, requiring businesses to adapt and implement robust security measures. Here are some of the most significant challenges:
- Data Breaches: Data breaches are a major concern for businesses, as they can lead to financial losses, reputational damage, and legal liabilities. The stolen data can be used for identity theft, fraud, or other malicious purposes.
- Ransomware Attacks: Ransomware attacks involve encrypting a victim’s data and demanding payment for its decryption. These attacks can cripple businesses and cause significant downtime.
- Phishing and Social Engineering: Phishing attacks involve tricking users into revealing sensitive information, such as login credentials or financial details. Social engineering attacks involve manipulating people into granting access to systems or data.
- Insider Threats: Insider threats are posed by individuals with authorized access to a company’s systems or data. This can include employees, contractors, or former employees who may intentionally or unintentionally compromise security.
- Lack of Skilled Cybersecurity Professionals: The demand for cybersecurity professionals is high, but there is a shortage of qualified individuals. This can make it difficult for businesses to find and retain skilled cybersecurity personnel.
Emerging Cybersecurity Threats
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Here are some of the most prominent emerging threats:
- Artificial Intelligence (AI) and Machine Learning (ML) in Cyberattacks: AI and ML are being used by attackers to automate attacks, make them more sophisticated, and evade detection.
- Internet of Things (IoT) Security: The increasing number of connected devices in the IoT presents new security challenges, as these devices are often poorly secured.
- Cloud Security: As businesses increasingly adopt cloud services, securing data and applications in the cloud becomes a critical concern.
- Mobile Device Security: Mobile devices are becoming increasingly popular for both personal and professional use, making them a prime target for attackers.
- Supply Chain Attacks: Attackers are targeting supply chains to compromise businesses indirectly through their suppliers or partners.
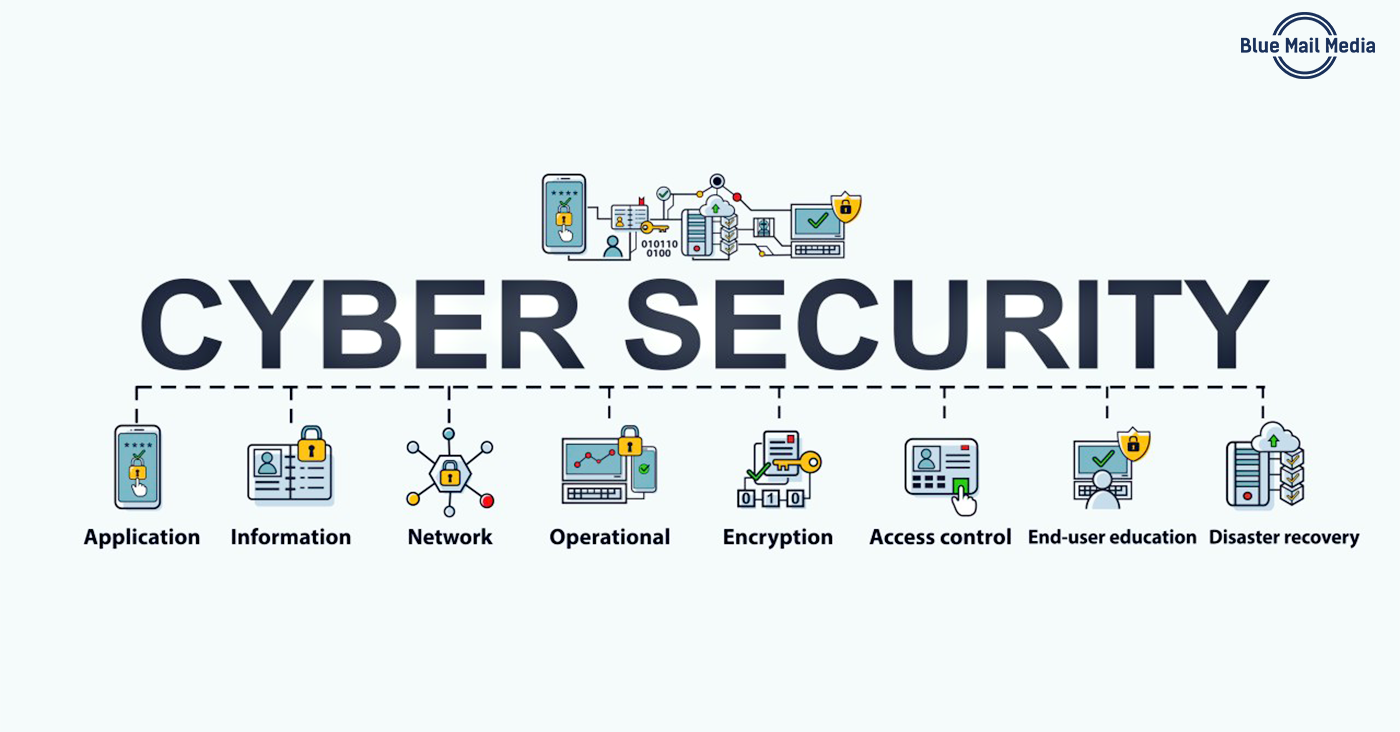
Types of Cybersecurity Solutions
The cybersecurity market offers a wide range of solutions to address different threats and challenges. Here are some of the most common types of cybersecurity solutions:
- Endpoint Security: Endpoint security solutions protect individual devices, such as computers, laptops, and mobile devices, from malware and other threats.
- Network Security: Network security solutions protect the network infrastructure, including firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
- Data Security: Data security solutions protect sensitive information, including data encryption, access control, and data loss prevention (DLP).
- Identity and Access Management (IAM): IAM solutions control access to systems and data based on user identity and permissions.
- Security Information and Event Management (SIEM): SIEM solutions collect and analyze security data from various sources to detect and respond to threats.
- Vulnerability Management: Vulnerability management solutions identify and remediate security vulnerabilities in systems and applications.
- Security Awareness Training: Security awareness training educates employees about cybersecurity threats and best practices.
- Incident Response: Incident response teams are responsible for responding to security incidents, containing damage, and recovering from attacks.
Defining Your Target Audience
Understanding your target audience is crucial for successful cybersecurity sales. By identifying the ideal customer profile and their specific needs, you can tailor your marketing and sales strategies to resonate with them.
Ideal Customer Profile
The ideal customer profile (ICP) represents the type of business that is most likely to benefit from your cybersecurity solutions. It Artikels the characteristics of your target audience, including:
- Industry: What industries are most vulnerable to cyberattacks? For example, healthcare, finance, and government sectors often face significant threats.
- Business Size: Are you targeting small businesses, medium-sized enterprises (SMEs), or large corporations? Different business sizes have varying cybersecurity needs and budgets.
- Revenue: What is the typical revenue range of your ideal customers? This helps you understand their financial capacity to invest in cybersecurity solutions.
- Technology Adoption: Are your solutions suitable for businesses with advanced technology infrastructure or those just starting their digital transformation journey?
- Security Posture: What is the current security posture of your target customers? Are they proactive in implementing security measures or reactive to security incidents?
Specific Needs and Pain Points
Different industries and business sizes have unique cybersecurity needs and pain points. Understanding these specific challenges will allow you to tailor your sales pitch and demonstrate how your solutions can address them.
Industries
- Healthcare: Healthcare organizations face increasing threats from ransomware attacks and data breaches, which can compromise sensitive patient information.
- Finance: Financial institutions are prime targets for cybercriminals due to the large amounts of money they handle. They need robust security measures to protect against fraud and data theft.
- Education: Educational institutions are increasingly relying on technology, making them vulnerable to cyberattacks. Protecting student data and maintaining academic integrity are key concerns.
- Government: Government agencies handle sensitive information, making them targets for cyberespionage and data breaches. They require advanced security solutions to protect national security and citizen privacy.
Business Size
- Small Businesses: Small businesses often lack the resources and expertise to implement comprehensive cybersecurity measures. They may need affordable and easy-to-use solutions that can be quickly deployed.
- Medium-Sized Enterprises (SMEs): SMEs are growing businesses that are increasingly adopting cloud computing and other technologies. They require scalable solutions that can adapt to their evolving needs.
- Large Corporations: Large corporations have complex IT infrastructure and require sophisticated security solutions to protect their vast data assets. They often have dedicated security teams and budgets for advanced cybersecurity measures.
Competitive Landscape
Analyzing the competitive landscape is crucial for differentiating your offerings and positioning yourself effectively in the market.
- Identify Key Competitors: Research your direct competitors and understand their strengths, weaknesses, and market positioning.
- Compare Solutions: Analyze the features, pricing, and target market of your competitors’ solutions. Identify key differentiators that set your offerings apart.
- Develop a Unique Value Proposition: Clearly articulate the unique benefits of your cybersecurity solutions and how they address the specific needs of your target audience.
“Understanding your target audience is the foundation for effective cybersecurity sales. By tailoring your message and solutions to their specific needs, you can build trust and drive conversions.”
Crafting a Compelling Value Proposition

A compelling value proposition is the heart of any successful cybersecurity sales strategy. It clearly articulates the unique benefits and advantages of your solutions, demonstrating their value to potential customers. It should be concise, persuasive, and tailored to the specific needs and challenges of your target audience.
Quantifying the Value of Cybersecurity Solutions
The value of cybersecurity solutions goes beyond simply preventing breaches. It encompasses a range of tangible benefits, such as reduced risk, improved efficiency, and cost savings. Here’s how you can quantify the value of your solutions:* Reduced Risk: Quantify the financial impact of potential security incidents, such as data breaches, system downtime, and reputational damage. You can use industry benchmarks and real-world examples to illustrate the potential costs.
Improved Efficiency
Highlight how your solutions streamline security operations, automate tasks, and reduce the burden on IT staff.
Cost Savings
Demonstrate how your solutions can save money by preventing costly security incidents, reducing the need for manual security processes, and improving operational efficiency. For example, you could highlight how your solution can help a company avoid a potential $1 million data breach by preventing a ransomware attack.
Aligning with Industry Best Practices and Regulations
Compliance with industry best practices and regulations is crucial for building trust and credibility with potential customers. Here’s how to demonstrate alignment:* Industry Standards: Highlight your solutions’ compliance with recognized industry standards, such as ISO 27001, NIST Cybersecurity Framework, and PCI DSS.
Regulatory Compliance
Showcase your solutions’ ability to meet specific regulatory requirements, such as GDPR, HIPAA, and CCPA.
Third-Party Certifications
Obtain certifications from reputable organizations, such as the National Institute of Standards and Technology (NIST) or the American National Standards Institute (ANSI), to demonstrate the quality and effectiveness of your solutions. By demonstrating compliance with industry best practices and regulations, you can build confidence in your solutions and assure potential customers that they are investing in a secure and reliable solution.
Building a Strong Sales Strategy
Now that you understand the market, your target audience, and your value proposition, it’s time to build a solid sales strategy. This strategy should be tailored to your specific offerings and target audience, ensuring you reach the right people with the right message.
Designing a Comprehensive Sales Process
A well-structured sales process is crucial for efficiently converting leads into paying customers. This process should be clearly defined and documented, providing a roadmap for your sales team to follow.
- Lead Generation: Start by identifying and attracting potential customers through various channels, such as online marketing, networking events, and industry partnerships.
- Lead Qualification: Assess the suitability of leads based on their needs, budget, and alignment with your target audience. This step helps prioritize your efforts and focus on prospects with a high probability of conversion.
- Needs Assessment: Conduct thorough conversations with qualified leads to understand their specific cybersecurity challenges, priorities, and pain points. This information is essential for tailoring your solutions and proposals.
- Solution Presentation: Showcase your cybersecurity solutions and services in a compelling and persuasive manner, highlighting the benefits and value they offer to address the customer’s needs. This might involve using presentations, demos, and case studies.
- Proposal and Negotiation: Develop a tailored proposal that Artikels the scope of work, pricing, and delivery timelines. Engage in negotiations to reach an agreement that satisfies both parties.
- Closing the Deal: Secure the commitment from the customer and finalize the contract. This stage involves addressing any remaining questions or concerns and finalizing the terms of the agreement.
- Onboarding and Implementation: Successfully integrate the customer into your ecosystem, providing necessary training, support, and ongoing communication to ensure a smooth transition and optimal utilization of your services.
Developing Compelling Sales Materials
High-quality sales materials are essential for communicating your value proposition and engaging potential customers. These materials should be visually appealing, informative, and tailored to your target audience.
- Presentations: Craft engaging presentations that effectively convey your message and demonstrate the value of your cybersecurity solutions. Use visuals, data points, and compelling storytelling to capture your audience’s attention.
- Brochures: Create concise and informative brochures that provide an overview of your services, highlight key benefits, and include contact information. Ensure the design is visually appealing and aligns with your brand identity.
- Case Studies: Showcase the success of your solutions by providing real-world examples of how you have helped other organizations achieve their cybersecurity goals. Include metrics, testimonials, and quantifiable results to demonstrate the impact of your services.
- White Papers: Offer valuable insights and thought leadership by publishing white papers that delve deeper into specific cybersecurity topics. These papers can establish your expertise and attract potential customers who are seeking in-depth information.
Creating Strategic Partnerships and Alliances
Collaborating with other companies in the cybersecurity ecosystem can expand your reach, leverage complementary expertise, and provide access to new markets.
- Technology Partners: Partner with technology vendors who offer complementary solutions or integrate seamlessly with your offerings. This can create a more comprehensive and robust cybersecurity ecosystem for your customers.
- Consulting Firms: Collaborate with consulting firms that specialize in cybersecurity to leverage their expertise in assessing customer needs and recommending solutions. This can enhance your credibility and expand your access to potential clients.
- Industry Associations: Engage with industry associations and professional organizations to network with potential partners, stay abreast of industry trends, and participate in joint initiatives.
Effective Marketing and Communication
Now that you’ve built a solid foundation for your cybersecurity business, it’s time to get the word out. Effective marketing and communication are crucial for attracting new clients and growing your business. It’s about reaching the right people with the right message at the right time.
Developing a Targeted Marketing Strategy
A targeted marketing strategy is essential for maximizing your marketing efforts. It’s about understanding your ideal customer and tailoring your messaging and outreach to their specific needs and interests.
- Identify your ideal customer profile: Who are your target clients? What are their pain points? What are their goals? You need to understand your audience inside and out.
- Define your value proposition: What makes your cybersecurity services unique and valuable? How do you solve your clients’ problems? Your value proposition should be clear, concise, and compelling.
- Choose the right marketing channels: There are many different marketing channels available, so it’s important to choose the ones that will reach your target audience. Consider online advertising, social media, content marketing, email marketing, and public relations.
Utilizing Various Marketing Channels
Once you’ve developed a targeted marketing strategy, you need to choose the right marketing channels to reach your ideal customers. Here’s a look at some popular options:
- Online advertising: Online advertising platforms like Google Ads and Facebook Ads allow you to target specific demographics, interests, and behaviors. This can be an effective way to reach potential clients who are actively searching for cybersecurity solutions.
- Social media: Social media platforms like LinkedIn, Twitter, and Facebook are great for building relationships with potential clients, sharing valuable content, and engaging in conversations.
- Content marketing: Content marketing involves creating and sharing valuable, relevant, and consistent content to attract and engage your target audience. This could include blog posts, articles, white papers, infographics, videos, and webinars.
- Public relations: Public relations can help you build credibility and generate positive media coverage. Consider issuing press releases, participating in industry events, and getting featured in relevant publications.
Sharing Compelling Stories and Testimonials
People are more likely to trust a business that has a strong reputation. Sharing compelling stories and testimonials from satisfied clients can help build trust and credibility.
- Case studies: Case studies are a powerful way to showcase your expertise and demonstrate the value of your services. Highlight how you helped a client solve a specific problem or achieve a particular goal.
- Client testimonials: Testimonials from satisfied clients are a powerful form of social proof. Encourage your clients to share their positive experiences with your services.
Providing Excellent Customer Service
In the cybersecurity landscape, customer service is not just an afterthought; it’s a critical differentiator. Building trust and loyalty with clients requires going above and beyond to ensure their satisfaction. By prioritizing customer service, you can establish a reputation for reliability, expertise, and commitment, which will ultimately drive long-term success.
Implement a Robust Customer Support System
A robust customer support system is essential for addressing any issues or concerns that clients may have. This system should be easily accessible, responsive, and provide clear communication channels.
- Establish Multiple Communication Channels: Offer various ways for customers to reach your support team, including email, phone, live chat, and a dedicated online portal. This ensures that customers can choose the communication method that best suits their needs.
- Provide 24/7 Support: Cybersecurity threats can occur at any time, so it’s crucial to offer 24/7 support to address urgent issues. This demonstrates a commitment to client needs and provides peace of mind.
- Use a Ticketing System: A ticketing system helps streamline support requests, track progress, and ensure that no issue falls through the cracks. This system should be user-friendly and provide real-time updates to customers.
- Offer Knowledge Base and FAQs: Create a comprehensive knowledge base and FAQ section on your website to address common questions and provide self-service options. This can reduce the workload on your support team and empower customers to find solutions independently.
Offer Ongoing Training and Resources
Continuously providing training and resources to customers is crucial for their success. This demonstrates your commitment to their ongoing security posture and helps them maximize the value of your services.
- Conduct Regular Webinars and Workshops: Offer educational sessions on emerging threats, best practices, and new features of your cybersecurity solutions. These sessions can be delivered online or in person, depending on your target audience and resources.
- Provide Access to White Papers and Reports: Share industry research and insights to keep customers informed about the latest security trends and vulnerabilities. This demonstrates your expertise and positions you as a thought leader in the cybersecurity space.
- Offer Personalized Training Programs: Tailor training programs to the specific needs of individual customers. This can include customized workshops, on-site training, or dedicated account managers who provide ongoing guidance and support.
Build Strong Relationships with Customers, How to sell cyber security
Building strong relationships with customers is essential for fostering loyalty and advocacy. This requires a proactive approach that goes beyond simply addressing technical issues.
- Regularly Check In with Customers: Schedule regular check-ins with customers to discuss their security posture, review their needs, and identify any potential challenges. This demonstrates your commitment to their success and allows you to build trust and rapport.
- Gather Feedback and Testimonials: Actively seek feedback from customers to understand their experiences and identify areas for improvement. Encourage satisfied customers to provide testimonials that can be used in your marketing materials and on your website.
- Offer Incentives for Referrals: Reward customers for referring new business to your company. This incentivizes existing customers to become advocates for your brand and can lead to significant growth in your client base.
Selling cybersecurity is not just about pushing products; it’s about building relationships and providing solutions that address real-world challenges. By taking a customer-centric approach, you can create a lasting impact and help businesses protect themselves from the ever-growing threat of cybercrime.
FAQ Summary: How To Sell Cyber Security
What are the most common cybersecurity threats?
Common threats include malware, phishing attacks, ransomware, data breaches, and denial-of-service attacks.
How can I effectively communicate the value of cybersecurity to my customers?
Focus on quantifying the risks and costs associated with cyberattacks, and demonstrate how your solutions can mitigate those risks and save money.
What are some essential elements of a strong sales strategy for cybersecurity?
A strong sales strategy includes a clear understanding of your target audience, a compelling value proposition, a well-defined sales process, and effective marketing and communication efforts.






