A security classification guide is a critical tool for any organization that handles sensitive information. It provides a framework for assessing, categorizing, and protecting data based on its value and confidentiality. The guide serves as a roadmap for safeguarding sensitive information, ensuring compliance with regulations, and mitigating risks.
Without a robust security classification guide, organizations face a significant risk of data breaches, legal penalties, and reputational damage. By implementing a comprehensive classification system, organizations can establish clear guidelines for data handling, access control, and information security measures.
Introduction
A security classification guide is a document that Artikels the levels of sensitivity and confidentiality assigned to information within an organization. It establishes a framework for protecting sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction.The purpose of security classification is to ensure that information is handled and protected according to its level of sensitivity. This helps organizations to mitigate risks, comply with regulations, and maintain the confidentiality, integrity, and availability of critical data.
Real-World Scenarios
Security classification is essential in various real-world scenarios, including:
- Financial institutions: Protect customer financial data, such as account numbers and credit card information, from unauthorized access and fraud.
- Healthcare organizations: Safeguard patient health records, including medical history, diagnoses, and treatment plans, to comply with HIPAA regulations and protect patient privacy.
- Government agencies: Classify sensitive information related to national security, defense, and intelligence, to prevent leaks and maintain national security.
- Technology companies: Protect intellectual property, trade secrets, and customer data to maintain competitive advantage and prevent breaches.
Elements of a Security Classification Guide
A security classification guide is a crucial document that Artikels the procedures for classifying information based on its sensitivity and the potential impact of unauthorized disclosure. It’s like a roadmap for safeguarding sensitive data, ensuring it stays in the right hands and doesn’t fall into the wrong ones.
Confidentiality, Integrity, and Availability
These three pillars form the foundation of information security. Think of them as the holy trinity of data protection.
- Confidentiality: This refers to protecting information from unauthorized access. It’s about keeping secrets, you know, like your crush’s phone number or the recipe for your grandma’s famous cookies.
- Integrity: Ensuring the accuracy and completeness of information. It’s like making sure your homework assignment is free from typos and plagiarism.
- Availability: This means making sure that authorized users can access information when they need it. Imagine trying to use your phone when the battery is dead, that’s what unavailability feels like.
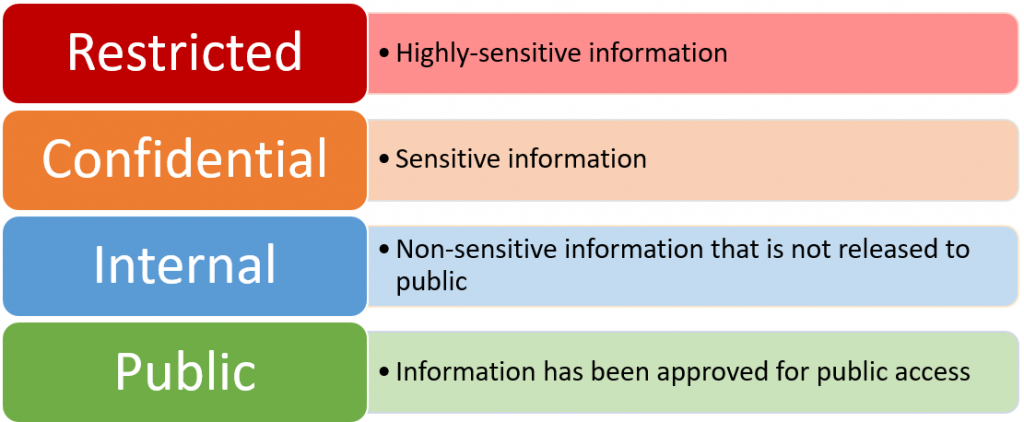
Classification Levels
Security classification guides typically define different levels of sensitivity, each with its own set of controls.
- Confidential: This level is for information that could cause some harm if disclosed. Think of it like a secret that could get you in a little trouble if it got out.
- Secret: This level is for information that could cause serious harm if disclosed. It’s like a secret that could get you in a lot of trouble if it got out.
- Top Secret: This level is for information that could cause exceptionally grave harm if disclosed. It’s like a secret that could get you in a whole lot of trouble if it got out.
Classification Process: A Security Classification Guide Is
The classification process involves a systematic approach to determining the sensitivity and criticality of information assets. It’s a crucial step in establishing a robust security posture.
Steps in Classifying Information Assets
The classification process typically involves these steps:
- Identify Information Assets: This step involves cataloging all information assets within the organization. This includes documents, databases, applications, systems, and any other forms of information.
- Determine Sensitivity: This step focuses on assessing the potential impact of unauthorized disclosure, modification, or destruction of the information. This includes evaluating the confidentiality, integrity, and availability of the information.
- Evaluate Criticality: This step involves assessing the importance of the information to the organization’s operations, reputation, and financial stability. Critical information is essential for the organization’s core functions and operations.
- Assign Classification Levels: Based on the sensitivity and criticality assessments, information assets are assigned specific classification levels. These levels represent the level of protection required for the information.
- Document Classification: The classification process is documented to ensure consistency and transparency. This documentation includes the classification criteria, assigned levels, and any relevant policies or procedures.
- Regular Review and Update: The classification process should be reviewed and updated regularly to reflect changes in the organization’s environment, business operations, and regulatory requirements.
Criteria for Determining Sensitivity and Criticality
The following criteria are typically considered when determining the sensitivity and criticality of information:
- Confidentiality: The level of confidentiality required for the information. This includes the potential impact of unauthorized disclosure on the organization’s reputation, financial stability, or national security.
- Integrity: The importance of ensuring the accuracy and completeness of the information. This includes the potential impact of unauthorized modification or alteration of the information.
- Availability: The importance of ensuring that the information is accessible to authorized users when needed. This includes the potential impact of unauthorized disruption or denial of access to the information.
- Legal and Regulatory Compliance: The compliance requirements related to the information, such as privacy laws, data protection regulations, and industry standards.
- Business Impact: The potential impact of unauthorized disclosure, modification, or destruction of the information on the organization’s business operations, financial performance, and reputation.
Methods for Assessing Risk and Assigning Classification Levels, A security classification guide is
Several methods can be used to assess risk and assign classification levels, including:
- Risk Assessment Frameworks: Frameworks like ISO 27005 and NIST SP 800-30 provide a structured approach to risk assessment. These frameworks help identify, analyze, and evaluate risks associated with information assets.
- Quantitative Risk Analysis: This method involves using statistical techniques to quantify the likelihood and impact of risks. This approach helps prioritize risks and allocate resources effectively.
- Qualitative Risk Analysis: This method involves using expert judgment and subjective assessments to evaluate risks. This approach is useful for evaluating risks that are difficult to quantify.
- Data Loss Prevention (DLP) Tools: DLP tools can be used to identify and monitor sensitive data and prevent its unauthorized disclosure. These tools can also be used to classify data based on predefined rules and policies.
Implementation and Management

Implementing and managing a security classification guide effectively is crucial for ensuring the protection of sensitive information. This section explores best practices for implementation, employee training, and ongoing review and updates to the guide.
Implementation Best Practices
Implementing a security classification guide requires a systematic approach to ensure its effectiveness. This includes:
- Clear Communication: Disseminate the guide to all employees, providing clear and concise explanations of classification levels, policies, and procedures. Ensure everyone understands their responsibilities in protecting sensitive information.
- Training and Awareness: Conduct comprehensive training programs to educate employees on the guide’s purpose, policies, and procedures. Use interactive methods like role-playing scenarios and quizzes to reinforce learning.
- System Integration: Integrate the guide with existing security systems, such as access control, data encryption, and data loss prevention (DLP) solutions. This ensures that security controls align with the classification levels.
- Regular Review and Updates: Regularly review the guide to ensure it remains relevant and effective. Consider updates based on changes in regulations, business operations, or technological advancements.
Employee Training Strategies
Effective employee training is crucial for successful implementation of the security classification guide. Consider these strategies:
- Interactive Training: Utilize interactive training methods, such as simulations, case studies, and group discussions, to engage employees and enhance understanding of the guide’s principles.
- Role-Playing Scenarios: Develop role-playing scenarios that demonstrate how to apply the classification guide in real-world situations. This helps employees practice decision-making in different contexts.
- Online Learning Platforms: Leverage online learning platforms to provide accessible and flexible training modules. This allows employees to learn at their own pace and access information anytime, anywhere.
- Regular Refreshers: Conduct regular refresher training sessions to reinforce knowledge and address any emerging security threats or changes in regulations.
Importance of Ongoing Review and Updates
A security classification guide is not a static document. It requires ongoing review and updates to remain effective. This is crucial for:
- Staying Ahead of Threats: Regularly review the guide to incorporate new threats, vulnerabilities, and security best practices. This ensures that the guide remains relevant and protects against emerging risks.
- Adapting to Business Changes: Update the guide to reflect changes in business operations, regulations, or technology. This ensures that the classification levels and policies remain aligned with current needs.
- Maintaining Compliance: Regularly review the guide to ensure compliance with relevant regulations and industry standards. This helps avoid potential legal or financial penalties.
Benefits of Security Classification
A well-defined security classification guide offers numerous benefits, contributing to a robust and secure information management system. It serves as a cornerstone for protecting sensitive information, ensuring compliance with regulations, and fostering a culture of security awareness within an organization.
Protection of Sensitive Information
A comprehensive security classification guide helps protect sensitive information from unauthorized access by establishing clear guidelines for data handling. It provides a structured framework for identifying and categorizing information based on its confidentiality, integrity, and availability requirements.
- Confidentiality: Classification ensures that sensitive data, such as financial records, customer information, or trade secrets, is accessible only to authorized individuals, preventing unauthorized disclosure.
- Integrity: By assigning appropriate classification levels, organizations can ensure that data remains accurate and unaltered, safeguarding against malicious modifications or accidental data corruption.
- Availability: The guide Artikels the availability requirements for different data categories, ensuring that critical information remains accessible to authorized users when needed, even during disruptions or emergencies.
Compliance with Regulatory Requirements
Security classification plays a crucial role in ensuring compliance with various industry regulations and legal requirements. By adhering to classification guidelines, organizations can demonstrate their commitment to data protection and security, reducing the risk of legal penalties and reputational damage.
- Data Protection Regulations: Regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) require organizations to implement robust data security measures, including classification systems to protect personal data.
- Industry Standards: Specific industries often have their own security standards, such as HIPAA (Health Insurance Portability and Accountability Act) for healthcare or PCI DSS (Payment Card Industry Data Security Standard) for financial institutions. Security classification helps organizations meet these industry-specific requirements.
- Government Regulations: Government agencies often have regulations governing the handling of classified information. Security classification guides help organizations comply with these regulations by defining clear procedures for managing sensitive data.
Enhanced Security Awareness
A well-defined security classification guide promotes a culture of security awareness within an organization. By providing clear guidelines and educating employees on data classification principles, organizations can foster a proactive approach to information security.
- Employee Training: The classification guide serves as a foundation for employee training programs, equipping them with the knowledge and skills to handle classified information responsibly.
- Clear Expectations: By outlining specific classification levels and associated responsibilities, the guide sets clear expectations for employees, reducing the likelihood of accidental data breaches or security incidents.
- Improved Data Security Practices: The guide encourages employees to adopt best practices for handling classified information, such as using strong passwords, implementing access controls, and reporting suspicious activities.
Challenges and Considerations
Implementing and maintaining a security classification guide can present various challenges, requiring careful consideration to ensure its effectiveness and practicality. Striking a balance between security needs and operational efficiency is crucial, while addressing potential conflicts between different classification levels is essential for maintaining a consistent and robust security posture.
Balancing Security and Efficiency
Balancing security needs with operational efficiency is a constant challenge in implementing and maintaining a security classification guide. While a stringent classification system can enhance security, it may also hinder productivity and create unnecessary bureaucracy. This section discusses how to achieve this balance.
- Streamlined Classification Process: Simplifying the classification process by minimizing the number of classification levels and providing clear, concise guidelines can reduce administrative overhead and improve efficiency.
- Risk-Based Approach: Implementing a risk-based approach to classification allows for a more flexible and efficient system. By focusing on the most critical information and assets, organizations can allocate resources more effectively and prioritize security measures.
- Technology-Enabled Solutions: Utilizing technology solutions, such as automated classification tools or data loss prevention (DLP) software, can streamline the classification process, reduce manual effort, and improve efficiency.
Addressing Conflicts Between Classification Levels
Conflicts between different classification levels can arise when individuals or departments have differing interpretations of the classification guidelines or when conflicting requirements exist. This section addresses how to handle these conflicts effectively.
- Clear and Consistent Guidelines: Establishing clear and consistent classification guidelines, including definitions, examples, and procedures, can minimize ambiguity and reduce the likelihood of conflicts.
- Designated Authority: Designating a responsible authority to resolve classification disputes or provide guidance on specific cases can ensure consistent application of the guidelines and maintain a unified approach.
- Regular Review and Updates: Periodically reviewing and updating the classification guide to reflect changes in technology, threats, or organizational needs can address potential conflicts and ensure its continued relevance.
Examples and Case Studies

It’s time to get real, fam. Let’s see how security classification guides actually work in the real world. We’ll check out some examples from different industries and see how they’ve been used to keep things safe. We’ll also look at some case studies that show how security classification has made a difference in real-life situations.
Security Classification Guides in Different Industries
Here’s the deal, security classification guides are used in many different industries, each with its own unique needs. Let’s take a look at some examples:
- Healthcare: Hospitals and clinics need to protect sensitive patient information, like medical records and insurance details. They use security classification guides to determine the level of protection needed for different types of data. This helps them comply with regulations like HIPAA and protect patient privacy.
- Finance: Banks and financial institutions handle tons of confidential financial data, like customer account information and transaction records. Security classification guides help them identify and protect sensitive data, preventing fraud and data breaches.
- Government: Governments deal with classified information, like national security secrets and confidential policy documents. Security classification guides are crucial for ensuring the confidentiality, integrity, and availability of this sensitive information.
- Education: Schools and universities have to protect student records, research data, and financial information. Security classification guides help them comply with regulations like FERPA and protect the privacy of students and faculty.
- Technology: Tech companies handle large amounts of sensitive data, including customer information, intellectual property, and proprietary algorithms. Security classification guides help them protect this data from unauthorized access and cyberattacks.
Case Studies of Security Classification Effectiveness
Now, let’s see how security classification has been used in the real world. These case studies show how it can make a real difference:
- A large retail chain: This company implemented a security classification guide to categorize its customer data based on sensitivity. They used this guide to implement access controls and encryption measures, significantly reducing the risk of data breaches. This case study shows how security classification can be used to protect customer data and build trust.
- A government agency: This agency implemented a security classification guide to manage classified information. The guide helped them identify and protect sensitive data, preventing leaks and ensuring national security. This case study demonstrates how security classification can be used to protect sensitive information and maintain national security.
- A healthcare provider: This provider implemented a security classification guide to protect patient health information. The guide helped them identify and protect sensitive data, ensuring compliance with HIPAA and protecting patient privacy. This case study shows how security classification can be used to protect patient data and comply with regulations.
Lessons Learned from Security Classification Implementations
Here’s the thing, not all security classification implementations are successful. Some things can go wrong, and it’s important to learn from those mistakes. Let’s look at some lessons learned:
- Lack of buy-in from employees: If employees don’t understand the importance of security classification, they may not follow the guidelines. This can lead to data breaches and security vulnerabilities. It’s important to involve employees in the implementation process and educate them about the importance of security classification.
- Poorly defined classification levels: If the classification levels are not clearly defined, it can be difficult to determine the appropriate level of protection for different types of data. This can lead to inconsistencies and security vulnerabilities. It’s important to define clear and concise classification levels that are easy to understand and apply.
- Lack of regular review and updates: Security threats are constantly evolving, so it’s important to regularly review and update security classification guides. This ensures that the guide remains effective and addresses new threats. Regularly review and update the security classification guide to reflect changes in technology, regulations, and threats.
A security classification guide is not merely a document; it’s a dynamic process that requires ongoing attention and adaptation. As threats evolve and regulatory landscapes shift, organizations must regularly review and update their classification systems to maintain effectiveness. By prioritizing security classification, organizations can build a culture of data protection and ensure the confidentiality, integrity, and availability of their most valuable assets.
Questions and Answers
What are the different classification levels?
Classification levels typically include “Confidential,” “Secret,” and “Top Secret,” with each level requiring progressively stricter security controls.
How often should a security classification guide be reviewed?
A security classification guide should be reviewed at least annually, or more frequently if there are significant changes in the organization’s operations, regulatory requirements, or threat landscape.
What are the consequences of not having a security classification guide?
The consequences of not having a security classification guide can be severe, including data breaches, regulatory fines, and reputational damage.






