Could not establish secure channel for ssl tls with authority – Have you ever encountered the dreaded “could not establish a secure channel for SSL/TLS with authority” error? This cryptic message often throws a wrench into our digital interactions, leaving us frustrated and wondering what went wrong. This error, unfortunately, can be a common hurdle in the world of secure communication, but understanding its root causes and troubleshooting steps can empower you to overcome it.
Imagine trying to access a website or online service, only to be met with this perplexing error message. It disrupts our online experience, raising concerns about the security of our data and the integrity of the website we’re trying to reach. The “could not establish a secure channel” error can occur in various scenarios, from outdated certificates to misconfigured servers, each presenting unique challenges.
Understanding the Error
The error “could not establish a secure channel for SSL/TLS with authority” signals a fundamental breakdown in the communication between a client (like your browser) and a server (the website you’re trying to access). It essentially means that the two parties cannot agree on a secure method to exchange information. This error has significant implications for both users and applications.
Implications for Users and Applications
This error prevents users from accessing the intended website or application. The user might encounter a blank page, an error message, or a warning about a security issue. For applications, this error can disrupt operations, preventing them from accessing critical resources or performing necessary tasks.
Common Scenarios Where This Error Might Occur
Several scenarios can lead to this error. These include:
- Invalid or Expired SSL/TLS Certificates: The server might have an invalid or expired SSL/TLS certificate, making it impossible for the client to verify its identity.
- Mismatched Cipher Suites: The client and server might not support the same encryption methods (cipher suites), leading to an inability to establish a secure connection.
- Firewall or Proxy Issues: Network security measures, like firewalls or proxies, might be blocking or interfering with the SSL/TLS handshake process.
- Incorrect Server Configuration: The server’s SSL/TLS configuration might be flawed, preventing it from properly establishing secure connections.
- Certificate Authority (CA) Issues: The client might not trust the Certificate Authority (CA) that issued the server’s certificate, leading to a trust violation.
SSL/TLS Basics
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a cryptographic protocol that provides secure communication over a computer network. It is essential for protecting sensitive information like passwords, credit card details, and other confidential data during online transactions and communication. SSL/TLS works by establishing an encrypted connection between a client (e.g., your web browser) and a server (e.g., a website). This encryption ensures that any data exchanged between the two parties remains confidential and protected from eavesdropping or tampering.
Key Components of SSL/TLS
The core components of SSL/TLS are:
- Certificate: A digital certificate is a file that contains information about the website owner and a public key. This certificate is issued by a trusted Certificate Authority (CA), which verifies the identity of the website owner. When a client connects to a website, the server presents its certificate to the client, allowing the client to verify the website’s authenticity.
- Key: Each website has a pair of keys: a public key and a private key. The public key is shared with the client, while the private key is kept secret on the server. These keys are used to encrypt and decrypt data during communication.
- Trust Store: The client’s web browser contains a list of trusted Certificate Authorities (CAs). When a website presents its certificate, the browser checks if the issuing CA is trusted. If the CA is trusted, the browser accepts the certificate and establishes a secure connection.
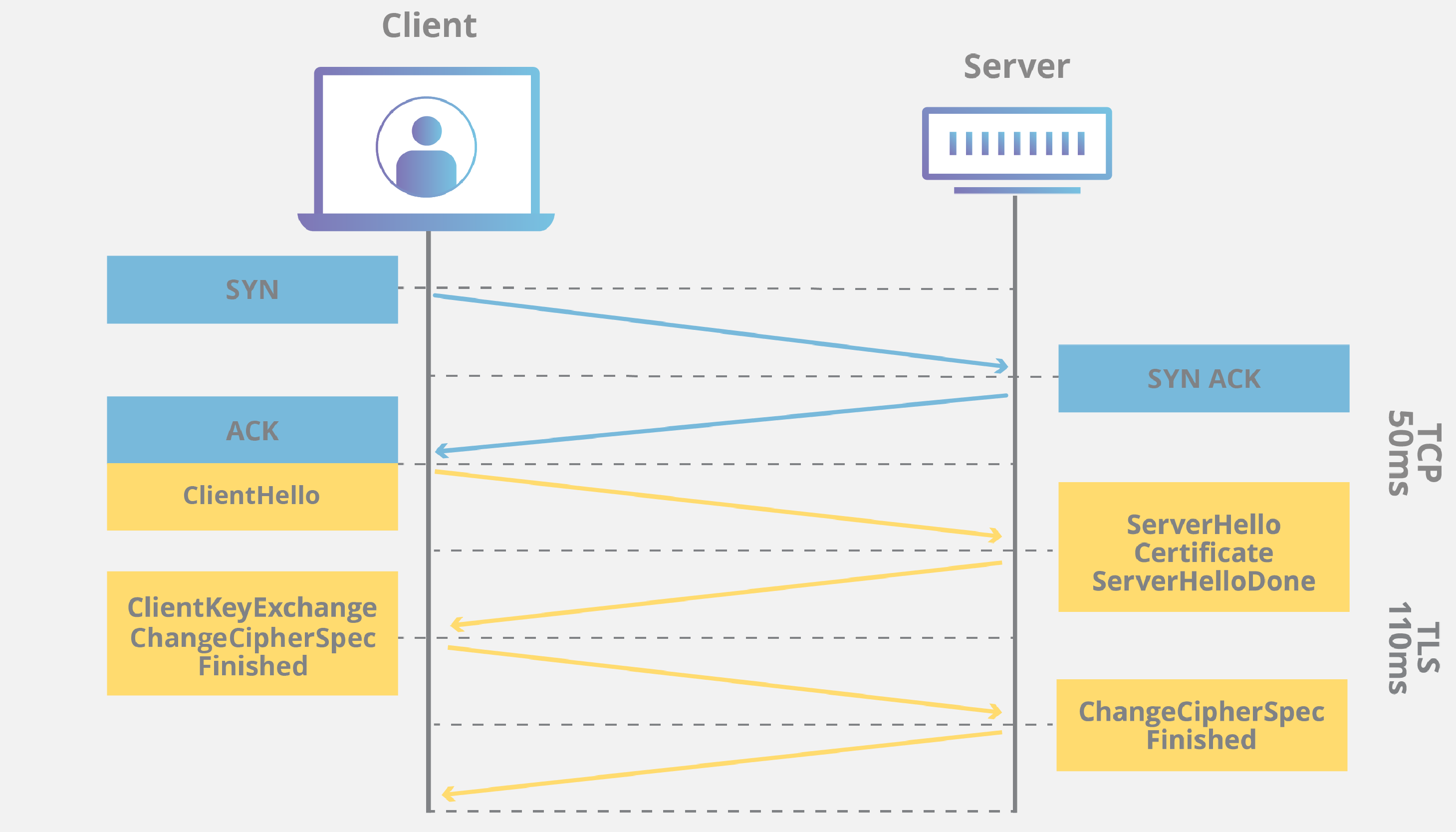
SSL/TLS Handshake Process
The handshake process is a series of steps that occur when a client initiates a connection to a secure website. The handshake process ensures the authenticity of the server and establishes a secure channel for communication.
The handshake process involves the following steps:
- Client Request: The client sends a request to the server, indicating its intention to establish a secure connection.
- Server Response: The server responds with its SSL/TLS certificate.
- Certificate Verification: The client verifies the server’s certificate against its list of trusted CAs. If the certificate is valid, the client generates a random session key.
- Key Exchange: The client encrypts the session key using the server’s public key and sends it to the server.
- Session Key Establishment: The server decrypts the session key using its private key. Both the client and server now have the same session key, which is used to encrypt all subsequent communication.
- Secure Communication: The client and server can now communicate securely using the established session key.
Potential Causes: Could Not Establish Secure Channel For Ssl Tls With Authority
The “could not establish a secure channel” error usually indicates a problem with the SSL/TLS handshake process. This handshake is crucial for establishing a secure connection between a client (like your browser) and a server. If any step in this process fails, the connection will be aborted, resulting in the error message. Let’s delve into some common reasons behind this error.
Certificate Validity and Trust
The SSL/TLS handshake relies heavily on digital certificates. These certificates act as digital identities for websites and servers, verifying their authenticity and ensuring data encryption. If there’s an issue with the certificate, the connection might fail.
- Expired Certificate: The certificate has passed its expiration date, making it invalid. This can occur if the website administrator hasn’t renewed the certificate.
- Not Yet Valid Certificate: The certificate hasn’t yet become active. This could be due to a misconfiguration or a delay in certificate issuance.
- Self-Signed Certificate: A self-signed certificate is created and signed by the website owner themselves, rather than a trusted Certificate Authority (CA). While useful for testing, they’re often not trusted by browsers and other applications.
- Certificate Revocation: A certificate can be revoked if it’s compromised or no longer valid. Browsers check for revoked certificates, and if one is found, the connection will be blocked.
Server Configuration Issues
The server’s configuration plays a crucial role in establishing secure connections. Incorrect settings can lead to handshake failures.
- Incorrect SSL/TLS Protocol Versions: The server might be configured to use outdated or unsupported SSL/TLS versions. For instance, older browsers might not support the latest versions, while some servers might not support older versions.
- Missing or Incorrect Cipher Suites: Cipher suites define the encryption algorithms used during the handshake. If the server and client don’t agree on a compatible cipher suite, the connection will fail.
- Port Misconfiguration: The server might be listening on the wrong port for SSL/TLS traffic. Typically, HTTPS connections use port 443, but if it’s configured differently, the client won’t be able to connect.
- Server Load or Resource Constraints: A heavily loaded server might not have enough resources to process the SSL/TLS handshake, leading to connection errors.
Client Settings and Compatibility
The client’s settings and compatibility also play a role in establishing secure connections.
- Outdated Browser or Operating System: Older browsers or operating systems might not support the latest SSL/TLS protocols or have outdated certificate trust lists.
- Firewall or Antivirus Interference: Security software like firewalls or antivirus programs might be blocking the connection.
- Proxy Server Issues: If you’re using a proxy server, it might be misconfigured or have issues establishing secure connections.
- Certificate Trust Store Issues: The client’s certificate trust store might be missing or have outdated information, leading to trust issues with the server’s certificate.
Troubleshooting Steps
Troubleshooting the “could not establish secure channel for SSL/TLS with authority” error involves systematically examining potential issues on both the client and server sides. This guide provides a step-by-step approach to identify and resolve the problem.
Verifying Certificate Validity and Trust
Verifying the validity and trust of the SSL/TLS certificate is a crucial step in troubleshooting. It ensures that the certificate is current, issued by a trusted authority, and matches the server’s domain name.
- Use a Certificate Checker Tool: Numerous online tools, like SSL Labs’ SSL Server Test ( https://www.ssllabs.com/ssltest/ ), allow you to analyze a website’s certificate. These tools provide details about the certificate’s validity, issuer, and chain of trust.
- Inspect the Certificate Manually: You can manually inspect the certificate by accessing it through your browser. In most browsers, you can find the certificate details by clicking the padlock icon in the address bar and selecting “Certificate” or “View Certificate.” Look for the following information:
- Issuer: The Certificate Authority (CA) that issued the certificate.
- Valid From/Valid To: The certificate’s validity period.
- Subject: The server’s domain name or hostname.
- Subject Alternative Names (SANs): If the certificate uses SANs, ensure they include the domain you’re trying to access.
- Check for Certificate Revocation: Certificates can be revoked if they become compromised. You can check the certificate’s revocation status using the Online Certificate Status Protocol (OCSP) or Certificate Revocation List (CRL).
Checking Server Configuration
The server’s configuration plays a vital role in establishing secure SSL/TLS connections. This section Artikels steps to verify the server’s configuration.
- Ensure the Correct Port is Open: SSL/TLS connections typically use port 443. Verify that port 443 is open and accessible on the server. You can use tools like `netstat` (on Linux/macOS) or `nmap` to check for open ports.
- Check the Server’s SSL/TLS Configuration: The server’s SSL/TLS configuration file specifies the protocols, ciphers, and certificates used. Review the configuration file for any errors or misconfigurations.
- Protocol Support: Ensure that the server supports the appropriate SSL/TLS protocols, such as TLS 1.2 or higher.
- Cipher Suites: The server should offer a strong set of cipher suites, including modern and secure options.
- Certificate and Key: Verify that the certificate and private key are correctly configured and match.
- Review Server Logs: Examine the server’s logs for any error messages related to SSL/TLS connections. These logs might provide insights into the specific cause of the error.
Checking Client Configuration
The client’s configuration also impacts the ability to establish secure SSL/TLS connections. This section focuses on verifying the client’s settings.
- Verify Client-Side Certificate Trust: Ensure that the client trusts the Certificate Authority (CA) that issued the server’s certificate. Clients typically have a list of trusted CAs.
- Operating System Settings: Check your operating system’s certificate store for trusted CAs.
- Browser Settings: Review your browser’s settings for trusted CAs.
- Check Client-Side SSL/TLS Settings: Examine the client’s SSL/TLS settings, such as supported protocols and cipher suites.
- Protocol Compatibility: Ensure that the client supports the same SSL/TLS protocols as the server.
- Cipher Suite Preferences: Review the client’s cipher suite preferences and make sure they overlap with the server’s offerings.
- Review Client-Side Logs: Check the client’s logs for any error messages related to SSL/TLS connections. These logs might provide information about the problem.
Troubleshooting Tools and Resources
Several tools and resources can aid in troubleshooting SSL/TLS errors:
- Network Analyzers: Tools like Wireshark can capture network traffic and analyze SSL/TLS handshake messages, providing detailed insights into the communication flow.
- SSL/TLS Debugging Tools: Specialized debugging tools like OpenSSL’s `s_client` command can help diagnose SSL/TLS connection issues.
- Online Forums and Communities: Online communities like Stack Overflow and security forums often have discussions and solutions for common SSL/TLS problems.
Security Best Practices
Preventing the “Could Not Establish Secure Channel” error requires a proactive approach to security. By implementing robust security practices, you can minimize the risk of encountering this error and ensure the integrity of your connections.
Certificate Management and Renewal
Certificate management is crucial for maintaining secure communication.
- Choose a reputable Certificate Authority (CA): Trusted CAs like Let’s Encrypt, DigiCert, and Sectigo offer reliable certificates and adhere to industry standards.
- Set up automatic renewal: Configure your server or web hosting platform to automatically renew certificates before they expire. This prevents interruptions in service due to expired certificates.
- Monitor certificate expiration dates: Regularly monitor certificate expiration dates and proactively renew certificates well in advance of their expiry.
Importance of Trusted Certificate Authorities
Using trusted certificate authorities (CAs) is essential for secure communication.
- Trusted CAs are vetted and verified: They undergo rigorous audits and security checks to ensure the validity and trustworthiness of their certificates.
- Browser and operating system compatibility: Trusted CAs are recognized by major browsers and operating systems, ensuring smooth and secure connections.
- Reduced risk of man-in-the-middle attacks: Using certificates from trusted CAs helps mitigate the risk of man-in-the-middle attacks, where attackers intercept and manipulate communication.
Illustrative Examples
To understand the error “could not establish secure channel for SSL/TLS with authority” more clearly, let’s look at some practical scenarios and their potential causes. These examples can help you identify the root of the issue and apply the appropriate solutions.
Common Scenarios Leading to SSL/TLS Errors
Here’s a table illustrating various scenarios that lead to the error, along with their causes and solutions:
| Scenario | Cause | Solution |
|---|---|---|
| Incorrect Server Configuration | The server might be misconfigured, with incorrect SSL/TLS settings like an invalid certificate, mismatched hostname, or missing intermediate certificates. | Review the server configuration and ensure all SSL/TLS settings are correct. Verify the certificate is valid, the hostname matches the one in the certificate, and all necessary intermediate certificates are included. |
| Expired or Invalid Certificate | The SSL/TLS certificate on the server might have expired or become invalid due to revocation or other issues. | Check the certificate’s validity and expiration date. If expired, renew the certificate. If revoked, investigate the reason for revocation and obtain a new certificate. |
| Certificate Chain Issues | The certificate chain, which includes the server certificate and its intermediate certificates, might be incomplete or broken. | Ensure the complete certificate chain is present and correctly configured on the server. Use tools like OpenSSL to verify the chain’s integrity. |
| Mismatched Hostname | The hostname in the certificate might not match the hostname being accessed. | Ensure the hostname in the certificate matches the hostname used in the browser or client application. |
| Port Blocking | The server’s port used for HTTPS (typically port 443) might be blocked by a firewall or other network security measures. | Check if port 443 is open and accessible. Configure firewall rules to allow traffic on this port. |
| Client-Side Issues | The client (browser or application) might have outdated SSL/TLS settings or be configured to block certain protocols or ciphers. | Update the client’s SSL/TLS settings to the latest versions and ensure the client supports the server’s protocols and ciphers. |
| DNS Issues | The DNS records for the server might be incorrect or unavailable, preventing the client from resolving the hostname and establishing a connection. | Verify the DNS records for the server are correct and accessible. Use tools like nslookup or dig to check the DNS resolution. |
Security Tools and Resources
Navigating SSL/TLS errors can be complex, but utilizing specialized security tools and resources can greatly simplify the troubleshooting process and improve your understanding of the underlying issues. These tools provide valuable insights, helping you identify the root cause of the problem and implement appropriate solutions.
Network Analyzers, Could not establish secure channel for ssl tls with authority
Network analyzers are essential for dissecting network traffic and understanding the communication flow between your client and the server. These tools capture and analyze packets, providing detailed information about each communication exchange.
- Wireshark: A powerful and widely-used open-source network protocol analyzer. Wireshark allows you to capture and analyze network traffic in real-time, providing a detailed view of packets, headers, and payload data. This information is invaluable for identifying SSL/TLS handshake failures, certificate issues, and other network-related problems.
Documentation: https://www.wireshark.org/docs/
Community: https://ask.wireshark.org/ - tcpdump: A command-line network packet analyzer that provides a simple yet effective way to capture and analyze network traffic. tcpdump is particularly useful for analyzing network traffic in a terminal environment, allowing you to filter and analyze packets based on specific criteria.
Documentation: https://www.tcpdump.org/manpages/tcpdump.1.html - Network Performance Monitor (NPM): Network performance monitoring tools like SolarWinds Network Performance Monitor and Datadog provide comprehensive network visibility, including real-time traffic analysis, performance metrics, and anomaly detection. They can help identify network bottlenecks, packet loss, and other issues that might contribute to SSL/TLS errors.
SSL/TLS Testers
Dedicated SSL/TLS testers help you evaluate the security posture of your website or server. These tools examine the configuration, certificates, and cipher suites used, identifying potential vulnerabilities and providing recommendations for improvement.
- SSL Labs: A comprehensive SSL/TLS testing service provided by Qualys. SSL Labs performs a thorough assessment of your website’s SSL/TLS configuration, including certificate chain validation, cipher suite analysis, and vulnerability detection. It provides a detailed report with recommendations for strengthening your security posture.
Website: https://www.ssllabs.com/ssltest/ - DigiCert SSL Checker: Another popular SSL/TLS testing service that provides a quick and easy way to check your website’s SSL/TLS configuration. DigiCert SSL Checker provides information about your certificate, including its validity, expiration date, and cipher suites supported.
Website: https://www.digicert.com/help/ssl-certificate-checker/ - Qualys SSL Labs API: For automated SSL/TLS testing and integration into your development workflows, consider using the Qualys SSL Labs API. This API allows you to programmatically perform SSL/TLS scans and retrieve results, enabling you to incorporate security checks into your continuous integration and deployment processes.
Documentation: https://community.qualys.com/docs/DOC-1334
Certificate Management Tools
Managing SSL/TLS certificates can be a complex task, especially when dealing with multiple websites and servers. Certificate management tools streamline the process, ensuring certificates are properly installed, renewed, and monitored.
- Let’s Encrypt: A free and automated certificate authority that provides SSL/TLS certificates for websites. Let’s Encrypt simplifies the certificate acquisition and renewal process, offering tools like Certbot for automated certificate issuance and management.
Website: https://letsencrypt.org/ - Certbot: An automated tool for obtaining and installing Let’s Encrypt certificates. Certbot simplifies the process of obtaining, installing, and renewing certificates for websites, supporting various web servers and operating systems.
Documentation: https://certbot.eff.org/docs/ - CloudFlare: A popular content delivery network (CDN) that offers SSL/TLS certificate management as part of its services. CloudFlare automatically issues and manages certificates for websites hosted on its platform, providing a secure and hassle-free experience.
Website: https://www.cloudflare.com/
By understanding the basics of SSL/TLS, identifying potential causes, and following a methodical troubleshooting process, we can overcome the “could not establish a secure channel” error and restore secure communication. Remember, security is paramount in the digital world, and by taking the necessary steps to ensure secure connections, we protect ourselves and our data from potential threats. Embrace the power of knowledge and confidently navigate the complexities of secure communication, ensuring a safe and reliable online experience.
FAQ Corner
What does “could not establish a secure channel” mean?
This error indicates that the website or service you’re trying to access cannot establish a secure connection with your device due to issues with SSL/TLS encryption.
Why is this error important?
This error highlights a potential security vulnerability, as it suggests that the communication between your device and the website is not secure.
Can I still access the website if I see this error?
You can, but it is not recommended. Accessing a website without a secure connection exposes your data to potential interception and compromise.
How do I fix this error?
Troubleshooting steps vary depending on the specific cause. Common solutions include verifying certificate validity, checking server configuration, and updating your browser or operating system.






