What is Forescout Secure Connector? Imagine a silent guardian, lurking in the shadows of your network, vigilantly watching for threats and anomalies. This guardian is Forescout Secure Connector, a powerful network security solution designed to detect and control devices before they can cause harm. With an air of mystery, it operates behind the scenes, ensuring the safety of your digital realm.
Forescout Secure Connector is a network access control (NAC) solution that provides visibility and control over devices connecting to your network. It acts as a gatekeeper, verifying the identity and security posture of each device before granting access. Its core function is to identify and mitigate security risks, enhancing your overall network security posture.
What is Forescout Secure Connector?
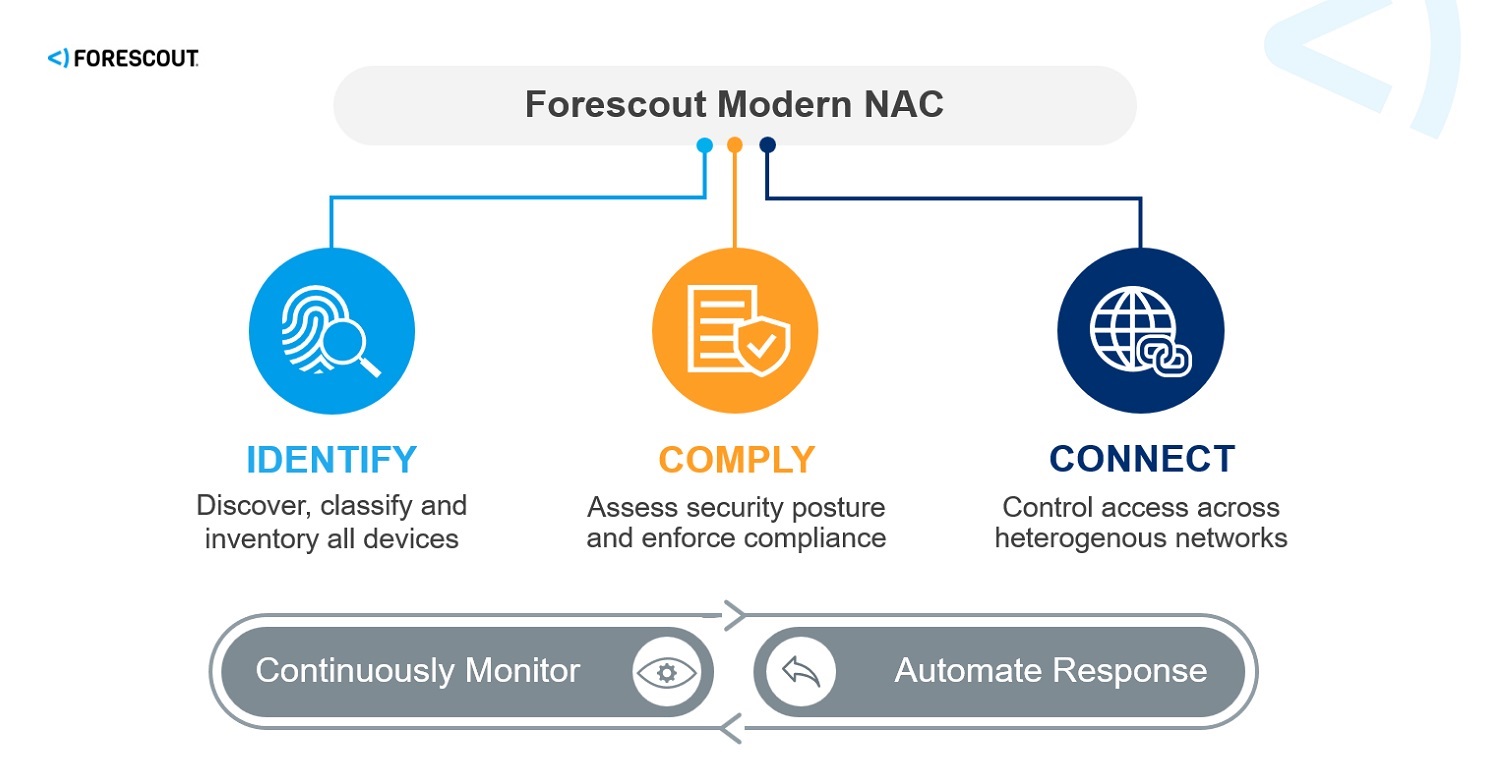
Forescout Secure Connector is a crucial component of the Forescout CounterACT platform, designed to enhance network security by providing visibility into and control over connected devices, regardless of their operating system or location. It acts as a bridge between Forescout CounterACT and various network devices, enabling the platform to gather real-time data and enforce security policies across the network.
Purpose of Forescout Secure Connector
The primary purpose of Forescout Secure Connector is to extend the reach and capabilities of Forescout CounterACT to a wider range of network devices and environments. It facilitates seamless integration with diverse network infrastructure components, allowing Forescout CounterACT to gather comprehensive device information, monitor network traffic, and implement security policies effectively.
Role of Forescout Secure Connector in Network Security
Forescout Secure Connector plays a vital role in enhancing network security by providing the following functionalities:
- Device Discovery and Inventory: The connector discovers and inventories all connected devices, regardless of their type, operating system, or location, providing a comprehensive view of the network landscape.
- Real-time Visibility: The connector continuously monitors network traffic and device activity, providing real-time insights into device behavior and potential security threats.
- Policy Enforcement: The connector enables Forescout CounterACT to enforce security policies across the network, including access control, vulnerability remediation, and compliance enforcement.
- Threat Detection and Response: The connector helps identify and respond to security threats by providing data on device vulnerabilities, malware infections, and suspicious activity.
Key Features and Functionalities of Forescout Secure Connector
Forescout Secure Connector offers a wide range of features and functionalities that contribute to its effectiveness in network security:
- Support for Multiple Network Devices: The connector supports a wide range of network devices, including switches, routers, firewalls, wireless access points, and more, ensuring comprehensive coverage across the network.
- Integration with Various Protocols: The connector integrates with various protocols, such as SNMP, NetFlow, and RADIUS, allowing it to collect data from diverse network devices.
- Customizable Configuration: The connector offers customizable configuration options to tailor its behavior and functionality to specific network requirements.
- Scalability and Performance: The connector is designed to scale effectively, supporting large and complex networks with high traffic volumes.
- Security and Compliance: The connector adheres to industry best practices for security and compliance, ensuring data integrity and confidentiality.
Examples of Forescout Secure Connector Use Cases
Forescout Secure Connector can be used in various scenarios to enhance network security:
- Device Visibility and Control: The connector can be used to discover and control unauthorized devices connected to the network, preventing access to sensitive resources.
- Vulnerability Remediation: The connector can be used to identify and remediate vulnerabilities on connected devices, reducing the risk of exploitation.
- Compliance Enforcement: The connector can be used to enforce compliance with security policies and regulations, ensuring that devices meet specific security standards.
- Threat Detection and Response: The connector can be used to detect and respond to security threats, such as malware infections and suspicious activity, minimizing the impact of attacks.
Benefits of Using Forescout Secure Connector
Implementing Forescout Secure Connector offers numerous advantages, significantly enhancing network visibility and security posture. By integrating with existing network infrastructure, it provides comprehensive device identification, control, and security posture assessment, ultimately improving overall security outcomes.
Network Visibility
Forescout Secure Connector empowers organizations to gain a deeper understanding of their network environment by providing real-time visibility into all connected devices, regardless of their type or location. This comprehensive visibility allows for:
- Comprehensive Device Inventory: Identifying all devices connected to the network, including known and unknown assets, such as laptops, smartphones, IoT devices, and servers. This ensures that organizations have a complete picture of their network landscape.
- Real-Time Device Tracking: Monitoring device activity and movements across the network, providing insights into user behavior and potential security risks. This enables proactive identification and mitigation of threats.
- Detailed Device Information: Gathering detailed information about each device, including its operating system, software versions, and security configurations. This information helps in assessing potential vulnerabilities and implementing appropriate security measures.
Enhanced Security Posture
Forescout Secure Connector plays a crucial role in strengthening network security by enabling organizations to:
- Automated Device Onboarding and Segmentation: Automating the process of onboarding new devices and segmenting them based on their security posture and risk profile. This ensures that only authorized and compliant devices can access sensitive network resources.
- Vulnerability Assessment and Remediation: Identifying and mitigating vulnerabilities across the network by continuously scanning devices for known security flaws. This proactive approach reduces the risk of exploitation by malicious actors.
- Threat Detection and Response: Detecting and responding to threats in real time by monitoring device behavior for suspicious activity. This includes identifying unauthorized access attempts, malware infections, and data breaches.
- Policy Enforcement and Compliance: Enforcing security policies across the network by automatically applying access controls and configurations based on predefined rules. This ensures compliance with industry standards and regulatory requirements.
Real-World Examples, What is forescout secure connector
- Healthcare Provider: A large healthcare provider implemented Forescout Secure Connector to gain visibility into their network and enforce security policies across their medical devices. The solution identified several vulnerable devices and enabled the organization to patch them promptly, reducing the risk of ransomware attacks and data breaches.
- Financial Institution: A financial institution used Forescout Secure Connector to monitor and control access to their sensitive financial data. The solution automatically segmented devices based on their security posture, ensuring that only authorized users could access critical systems. This significantly reduced the risk of unauthorized access and data breaches.
- Manufacturing Company: A manufacturing company deployed Forescout Secure Connector to secure their industrial control systems (ICS) from cyberattacks. The solution provided real-time visibility into all connected devices, including industrial robots and sensors, enabling the organization to detect and respond to threats promptly.
Architecture and Components of Forescout Secure Connector
Forescout Secure Connector (FSC) is a key component of the Forescout platform, enabling the secure connection of devices to the network. The FSC architecture is designed to provide a flexible and scalable solution that can be deployed in various network environments.The FSC architecture comprises several key components that work together to provide comprehensive device visibility and control.
Components and Functionalities
The FSC architecture comprises various components that work in unison to achieve secure network connectivity. Here’s a breakdown of the essential components and their roles:
- Forescout Secure Connector (FSC): This is the primary component of the Forescout platform. It acts as the agent that collects data from network devices and sends it to the Forescout Control Center (FCC). The FSC is responsible for monitoring network traffic, identifying devices, and enforcing policies based on the configured rules.
- Forescout Control Center (FCC): The FCC is the central management console for the Forescout platform. It receives data from the FSCs and analyzes it to identify potential security threats. The FCC also provides a user interface for configuring policies, managing devices, and monitoring network activity.
- Policy Engine: The Policy Engine is a core component of the FCC that evaluates the data collected by the FSCs and applies the appropriate policies. The Policy Engine uses a set of predefined rules to determine the actions that should be taken for each device, such as allowing or blocking access to specific resources.
- Device Inventory: The Device Inventory is a database that stores information about all the devices on the network. This information includes the device’s name, MAC address, IP address, operating system, and other relevant details. The Device Inventory is used by the FCC to identify devices and apply the appropriate policies.
- Reporting Engine: The Reporting Engine generates reports that provide insights into network activity and security posture. These reports can be used to identify trends, track compliance, and improve security.
- Integration Engine: The Integration Engine enables the Forescout platform to integrate with other security tools and systems. This allows the Forescout platform to share information with other security tools and automate security tasks.
Communication Flow
The communication flow between the FSCs and the FCC is essential for the Forescout platform to function effectively. The FSCs collect data from network devices and send it to the FCC. The FCC then analyzes this data and applies the appropriate policies. The FCC can also send commands to the FSCs to enforce policies or perform other actions.The communication flow between the FSCs and the FCC is typically based on TCP/IP and uses secure protocols such as HTTPS and TLS.
The FSCs communicate with the FCC using a secure connection to ensure that data is protected during transmission.
Component Functionalities
The following table summarizes the key components of the Forescout Secure Connector and their functionalities:
| Component | Functionality |
|---|---|
| Forescout Secure Connector (FSC) | Collects data from network devices, identifies devices, and enforces policies based on configured rules. |
| Forescout Control Center (FCC) | Central management console for the Forescout platform, analyzes data from FSCs, configures policies, manages devices, and monitors network activity. |
| Policy Engine | Evaluates data collected by the FSCs and applies appropriate policies based on predefined rules. |
| Device Inventory | Stores information about all the devices on the network, used by the FCC to identify devices and apply appropriate policies. |
| Reporting Engine | Generates reports that provide insights into network activity and security posture. |
| Integration Engine | Enables the Forescout platform to integrate with other security tools and systems, allowing for information sharing and automation. |
Deployment and Configuration of Forescout Secure Connector
Deploying and configuring Forescout Secure Connector is a crucial step in implementing a robust network security solution. This process involves installing the connector on your network devices, configuring its settings to match your security policies, and ensuring its integration with the Forescout platform for effective device visibility and control.
Deployment Steps
Deploying Forescout Secure Connector involves the following steps:
- Download the Forescout Secure Connector software: Obtain the appropriate connector software package from the Forescout website based on the supported operating system and hardware platform of your network devices.
- Install the Forescout Secure Connector: Install the downloaded connector software on your network devices, following the provided installation instructions. This may involve running an installer or copying files to the device.
- Configure the Forescout Secure Connector: Once installed, configure the connector to connect to your Forescout platform. This involves providing essential information such as the platform’s IP address, credentials, and other relevant settings.
- Verify the connector’s connection: After configuration, verify that the connector is successfully communicating with the Forescout platform. This can be done by checking the connector’s status on the Forescout console.
Configuration Best Practices
To optimize Forescout Secure Connector performance and ensure its effectiveness, consider the following configuration best practices:
- Configure logging: Enable logging on the connector to capture events and debug issues. This can help troubleshoot problems and understand the connector’s behavior.
- Set up alerts: Configure alerts to notify you of important events, such as unauthorized device access or policy violations. This helps you proactively address security risks.
- Optimize performance: Configure the connector to utilize appropriate network settings and resources to minimize performance impact on your network devices. This may involve adjusting communication frequency or limiting bandwidth usage.
- Implement security measures: Secure the connector itself by configuring strong passwords, enabling authentication mechanisms, and applying appropriate security policies. This helps prevent unauthorized access and malicious activities.
Deployment Models
Forescout Secure Connector offers various deployment models to suit different network environments:
- Centralized deployment: In this model, a single Forescout platform manages multiple connectors deployed across the network. This simplifies management and provides a centralized view of security events.
- Distributed deployment: This model involves deploying multiple Forescout platforms with their own connectors, each managing specific network segments. This can be beneficial for large and complex networks with diverse security requirements.
- Hybrid deployment: This model combines centralized and distributed approaches, offering flexibility and scalability for managing large and diverse networks.
Security Considerations
When deploying and configuring Forescout Secure Connector, it’s crucial to address security considerations:
- Secure communication: Ensure that communication between the connector and the Forescout platform is encrypted using secure protocols like TLS/SSL to prevent eavesdropping and data interception.
- Access control: Implement robust access control mechanisms to restrict access to the connector and its configuration settings. This helps prevent unauthorized modifications and malicious activities.
- Regular updates: Keep the connector software up-to-date with the latest security patches and bug fixes to mitigate vulnerabilities and improve security posture.
- Network segmentation: Consider segmenting your network to isolate the connector and its communication channels from other sensitive systems, reducing the potential impact of security breaches.
Integration with Other Security Tools
Forescout Secure Connector excels in its ability to integrate with a wide range of security tools, enhancing its capabilities and enabling comprehensive security posture management. These integrations streamline workflows, improve visibility, and facilitate automated responses to security threats.Forescout Secure Connector’s integration capabilities empower organizations to build a cohesive security ecosystem, where various tools collaborate seamlessly to achieve optimal security outcomes.
Integration with SIEM
Forescout Secure Connector integrates with Security Information and Event Management (SIEM) systems, providing valuable context to security events. This integration enhances threat detection and incident response by enriching SIEM alerts with detailed device information, network context, and vulnerability data.For example, when a SIEM system detects suspicious network traffic, Forescout Secure Connector can provide the following information:* Device details: Device type, operating system, MAC address, and other identifying information.
Network context
Network location, VLAN membership, and connected network segments.
Vulnerability data
Known vulnerabilities on the device, including CVSS scores and remediation guidance.This enriched data allows security analysts to prioritize alerts, quickly determine the affected devices, and take appropriate actions to mitigate threats.
Integration with EDR
Forescout Secure Connector integrates with Endpoint Detection and Response (EDR) solutions, enabling automated response to security incidents. This integration allows for swift containment of threats by leveraging EDR capabilities to isolate compromised devices or terminate malicious processes.For instance, if Forescout Secure Connector detects a device exhibiting suspicious behavior, it can trigger an EDR agent to:* Isolate the device: Disconnect the device from the network to prevent further spread of infection.
Terminate malicious processes
Identify and terminate malicious processes running on the device.
Collect forensic data
Gather evidence from the device for further investigation.This integration streamlines incident response by automating critical steps, reducing the time it takes to contain threats and minimizing potential damage.
Integration with Other Network Security Solutions
Forescout Secure Connector seamlessly integrates with various network security solutions, such as firewalls, intrusion detection systems (IDS), and network access control (NAC) systems. These integrations enhance network security by sharing information and automating security actions.For example, Forescout Secure Connector can:* Share device information with firewalls: Provide firewall rules with up-to-date device information, ensuring accurate access control.
Trigger IDS alerts
Send alerts to IDS systems when suspicious activity is detected on a device.
Enforce NAC policies
Automate the enforcement of NAC policies based on device compliance and security posture.These integrations enable a unified approach to network security, ensuring consistent security posture across the entire network infrastructure.
Integration Benefits
| Integration | Benefits |
|---|---|
| SIEM | Enhanced threat detection and incident response, improved security visibility, and streamlined incident investigation. |
| EDR | Automated incident response, rapid threat containment, and reduced mean time to remediate (MTTR). |
| Firewalls | Improved access control, accurate firewall rule enforcement, and enhanced network security. |
| IDS | Enhanced threat detection, automated response to security incidents, and improved network security. |
| NAC | Automated policy enforcement, improved device compliance, and enhanced network security. |
Use Cases and Best Practices: What Is Forescout Secure Connector
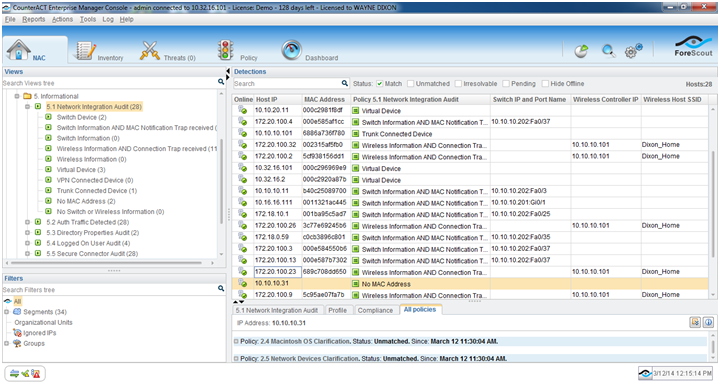
Forescout Secure Connector offers a range of functionalities to enhance security posture and visibility across your network. Understanding its various use cases and implementing best practices will maximize its benefits.
Common Use Cases
Forescout Secure Connector can be leveraged in several critical areas:
- Device Visibility and Control: Gaining visibility into all connected devices, including those not managed by traditional systems, is crucial. Forescout Secure Connector helps identify and control unauthorized devices, preventing potential security threats.
- Vulnerability Management: Identifying and mitigating vulnerabilities is essential. Forescout Secure Connector helps assess the security posture of devices, identify vulnerabilities, and prioritize remediation efforts.
- Network Segmentation: Segmenting your network effectively isolates sensitive data and reduces the impact of potential breaches. Forescout Secure Connector helps implement and enforce network segmentation policies, enhancing security.
- Compliance and Auditing: Meeting regulatory requirements and industry standards requires robust security controls. Forescout Secure Connector aids in demonstrating compliance by providing detailed audit trails and reports.
- Threat Response and Incident Handling: In case of a security incident, quick and effective response is critical. Forescout Secure Connector helps isolate compromised devices, contain the spread of malware, and facilitate incident investigation.
Best Practices for Implementation and Management
- Comprehensive Deployment: Deploy Forescout Secure Connector across all network segments to ensure complete visibility and control. This includes both wired and wireless networks.
- Policy-Based Configuration: Implement comprehensive and granular policies to control device access, network traffic, and user behavior. These policies should align with your organization’s security requirements.
- Regular Monitoring and Analysis: Continuously monitor the Forescout Secure Connector console for alerts, events, and device activity. Analyze data to identify trends, potential threats, and compliance gaps.
- Integration with Other Security Tools: Integrate Forescout Secure Connector with other security tools, such as firewalls, intrusion detection systems (IDS), and SIEM systems, to enhance threat detection and response capabilities.
- Regular Updates and Patches: Keep Forescout Secure Connector software and agent components up to date with the latest security patches and updates to mitigate vulnerabilities and ensure optimal performance.
Real-World Examples of Success
Forescout Secure Connector has been successfully implemented in various organizations to address critical security challenges:
- Healthcare: A major hospital chain used Forescout Secure Connector to identify and control medical devices, preventing unauthorized access and ensuring patient data security.
- Financial Services: A global bank implemented Forescout Secure Connector to segment its network, isolate sensitive data, and comply with regulatory requirements.
- Education: A university used Forescout Secure Connector to gain visibility into student and faculty devices, enforce access control policies, and prevent unauthorized access to sensitive research data.
Recommendations for Optimizing Forescout Secure Connector
- Leverage Automation: Automate tasks such as device onboarding, policy updates, and incident response to streamline operations and improve efficiency.
- Utilize Advanced Analytics: Employ machine learning and artificial intelligence (AI) capabilities to detect anomalies, predict potential threats, and enhance threat response.
- Develop a Comprehensive Security Strategy: Integrate Forescout Secure Connector into a holistic security strategy that includes other security tools, processes, and best practices.
- Invest in Training and Expertise: Ensure your security team is trained and proficient in using Forescout Secure Connector effectively.
Security and Compliance
Forescout Secure Connector is designed with robust security measures to ensure the protection of sensitive data and compliance with industry regulations. It plays a crucial role in maintaining a secure network environment and helping organizations meet their compliance obligations.
Security Considerations
Forescout Secure Connector incorporates several security considerations to safeguard the network and sensitive data. These include:* Data Encryption: The Secure Connector encrypts all communication with the Forescout platform, preventing unauthorized access to sensitive information.
Authentication and Authorization
Secure Connector implements strong authentication and authorization mechanisms to control access to its functionalities and ensure only authorized users can manage and configure the device.
Secure Communication Protocols
The Secure Connector uses secure communication protocols like HTTPS and TLS to protect data during transmission.
Regular Security Updates
Forescout provides regular security updates and patches to address vulnerabilities and maintain the security posture of the Secure Connector.
Security Auditing
The Secure Connector logs all activities, providing a detailed audit trail for security investigations and compliance reporting.
Compliance with Industry Regulations
Forescout Secure Connector helps organizations meet compliance requirements by providing the necessary tools and functionalities to enforce security policies and track device behavior. It supports compliance with various industry regulations, including:* PCI DSS: The Secure Connector helps organizations comply with the Payment Card Industry Data Security Standard (PCI DSS) by enforcing access control policies, detecting and mitigating vulnerabilities, and providing detailed audit trails.
HIPAA
The Secure Connector assists in complying with the Health Insurance Portability and Accountability Act (HIPAA) by controlling access to sensitive medical data, enforcing security policies, and monitoring device behavior.
GDPR
The Secure Connector helps organizations meet the General Data Protection Regulation (GDPR) by providing tools for data inventory management, access control, and data breach detection.
SOX
The Secure Connector facilitates compliance with the Sarbanes-Oxley Act (SOX) by providing detailed audit trails and security controls for financial data.
Examples of Compliance Use Cases
Here are some examples of how Forescout Secure Connector can be used to address compliance requirements:* Device Inventory and Control: The Secure Connector can be used to identify and track all devices connected to the network, ensuring that only authorized devices are allowed access. This helps meet compliance requirements related to device inventory management and access control.
Vulnerability Management
The Secure Connector can scan devices for vulnerabilities and enforce remediation policies. This helps organizations comply with regulations that require vulnerability management and patching.
Data Loss Prevention
The Secure Connector can be used to implement data loss prevention policies, preventing sensitive data from being transmitted to unauthorized destinations. This helps organizations comply with regulations related to data protection.
Network Segmentation
The Secure Connector can be used to segment the network, isolating critical systems from less secure areas. This helps organizations comply with regulations that require network segmentation and access control.
Security Features and Functionalities
Forescout Secure Connector offers several security features and functionalities that contribute to a secure network environment. These include:* Device Identification and Classification: The Secure Connector identifies and classifies devices based on various attributes, including hardware, software, and network behavior. This enables organizations to apply appropriate security policies based on device type and risk profile.
Network Access Control (NAC)
The Secure Connector implements NAC policies to control device access to the network based on device identity, security posture, and compliance status.
Vulnerability Assessment and Remediation
The Secure Connector scans devices for vulnerabilities and automatically remediates them by applying patches or configuring security settings.
Data Loss Prevention (DLP)
The Secure Connector can be used to prevent sensitive data from being transmitted to unauthorized destinations.
Security Policy Enforcement
The Secure Connector enforces security policies across the network, ensuring devices comply with security standards and regulations.
Threat Intelligence Integration
The Secure Connector integrates with threat intelligence feeds to identify and mitigate known threats.
Incident Response
The Secure Connector provides visibility into device behavior and security events, enabling rapid incident response and mitigation.
Troubleshooting and Support
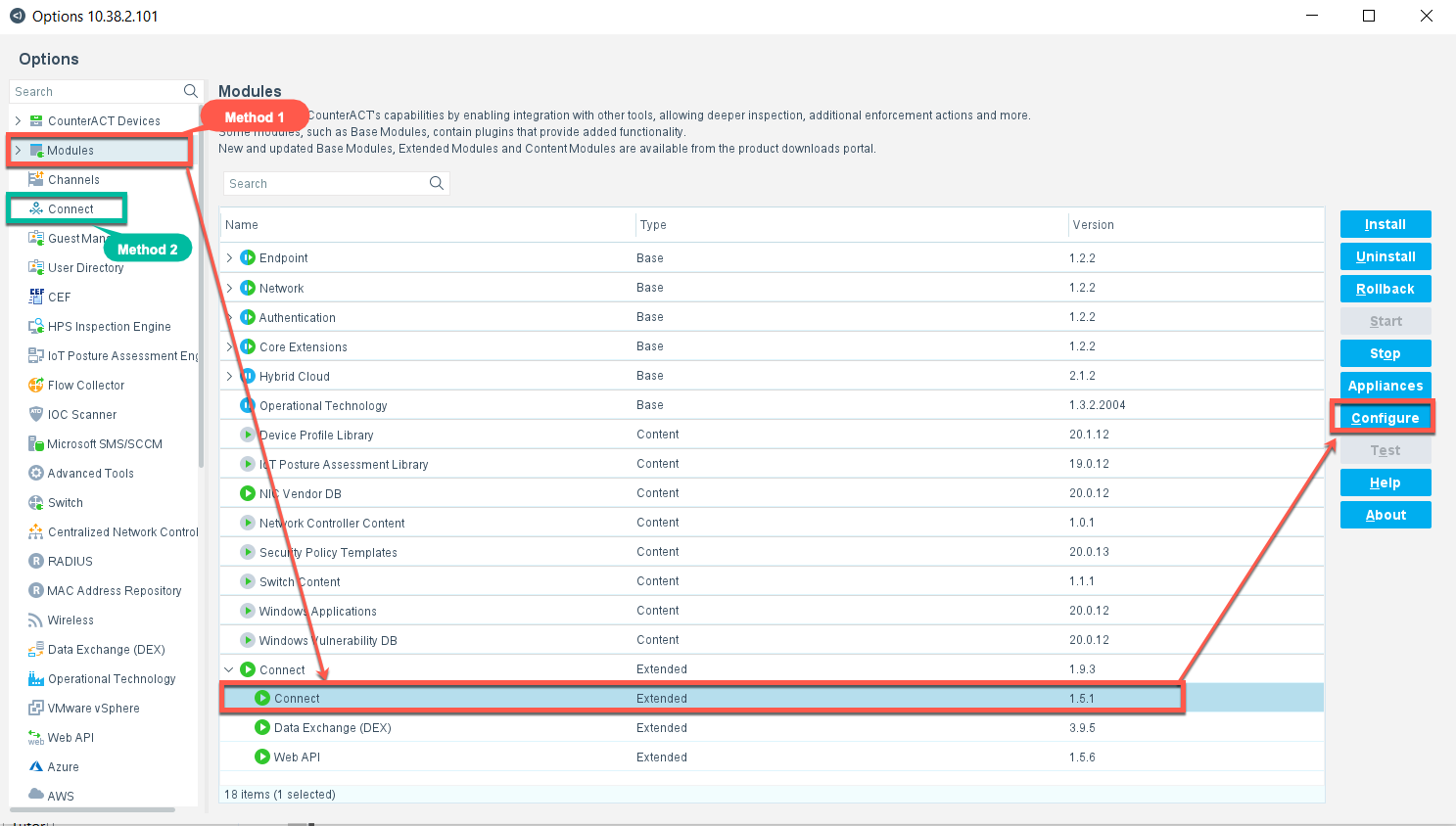
Forescout Secure Connector is a powerful tool for network security, but like any complex software, it can encounter issues. Troubleshooting and resolving these issues efficiently is crucial for maintaining network security and ensuring smooth operations. This section explores common troubleshooting techniques, support resources, and steps for resolving common problems with Forescout Secure Connector.
Common Troubleshooting Techniques
Troubleshooting Forescout Secure Connector involves a systematic approach to identify and resolve the root cause of issues. Common techniques include:
- Reviewing Logs: Forescout Secure Connector generates extensive logs that provide valuable insights into system activity, errors, and warnings. Reviewing these logs, particularly during troubleshooting, can pinpoint the source of the problem.
- Verifying Network Connectivity: Ensure the Forescout Secure Connector has proper network connectivity to the Forescout platform and any relevant network devices. This includes checking firewall rules, network configurations, and the status of network interfaces.
- Checking System Resources: Resource constraints such as CPU, memory, or disk space can impact Forescout Secure Connector performance. Monitor these resources to identify potential bottlenecks or resource exhaustion issues.
- Testing Configuration: Thoroughly review the Forescout Secure Connector configuration to ensure all settings are correct and consistent with network requirements. Testing configuration changes in a controlled environment before deploying them in production can minimize potential disruptions.
- Analyzing Event Data: Forescout Secure Connector collects data about network events, including device connections, security events, and policy violations. Analyzing this event data can help identify patterns, anomalies, and potential security threats.
Available Support Resources
Forescout offers various support resources to assist users with troubleshooting and resolving issues:
- Forescout Support Portal: This online portal provides access to comprehensive documentation, knowledge base articles, and support resources. Users can search for information, submit support tickets, and engage with Forescout support engineers.
- Forescout Community Forums: The Forescout community forums offer a platform for users to connect, share experiences, and seek assistance from peers and Forescout experts. This collaborative environment fosters knowledge sharing and problem-solving.
- Forescout Professional Services: Forescout offers professional services for deployment, configuration, and ongoing support. These services provide expert guidance and assistance to ensure successful implementation and optimal performance of Forescout Secure Connector.
Resolving Common Issues
Following are steps to resolve some common issues with Forescout Secure Connector:
- Device Communication Errors:
- Verify network connectivity between the Forescout Secure Connector and the device experiencing communication issues. Check firewall rules, network configurations, and the status of network interfaces.
- Review Forescout Secure Connector logs for any error messages related to device communication. These logs can provide insights into the specific communication problems.
- Ensure the device is configured correctly to support communication with the Forescout Secure Connector. Check the device’s network settings and protocols.
- If the issue persists, contact Forescout support for further assistance.
- Policy Enforcement Issues:
- Verify that the policy is correctly configured and applied to the affected device. Check the policy rules, conditions, and actions.
- Ensure the Forescout Secure Connector has the necessary permissions and access to enforce the policy on the device.
- Review Forescout Secure Connector logs for any errors or warnings related to policy enforcement. These logs can provide clues about the root cause of the issue.
- If the issue persists, contact Forescout support for further assistance.
- Performance Degradation:
- Monitor Forescout Secure Connector system resources, including CPU, memory, and disk space. Identify any resource constraints that might be impacting performance.
- Review Forescout Secure Connector logs for any performance-related errors or warnings. These logs can provide insights into potential bottlenecks or resource exhaustion issues.
- Optimize Forescout Secure Connector configuration by adjusting settings such as scan intervals, data collection frequency, and logging levels. Experiment with different settings to find the optimal balance between performance and data collection.
- Consider upgrading Forescout Secure Connector to the latest version to benefit from performance enhancements and bug fixes.
- If performance issues persist, contact Forescout support for further assistance.
Frequently Asked Questions
- How can I troubleshoot device communication errors with Forescout Secure Connector?
- Verify network connectivity between the Forescout Secure Connector and the device experiencing communication issues. Check firewall rules, network configurations, and the status of network interfaces.
- Review Forescout Secure Connector logs for any error messages related to device communication. These logs can provide insights into the specific communication problems.
- Ensure the device is configured correctly to support communication with the Forescout Secure Connector. Check the device’s network settings and protocols.
- If the issue persists, contact Forescout support for further assistance.
- What are some common reasons for policy enforcement issues with Forescout Secure Connector?
- Verify that the policy is correctly configured and applied to the affected device. Check the policy rules, conditions, and actions.
- Ensure the Forescout Secure Connector has the necessary permissions and access to enforce the policy on the device.
- Review Forescout Secure Connector logs for any errors or warnings related to policy enforcement. These logs can provide clues about the root cause of the issue.
- If the issue persists, contact Forescout support for further assistance.
- How can I improve Forescout Secure Connector performance?
- Monitor Forescout Secure Connector system resources, including CPU, memory, and disk space. Identify any resource constraints that might be impacting performance.
- Review Forescout Secure Connector logs for any performance-related errors or warnings. These logs can provide insights into potential bottlenecks or resource exhaustion issues.
- Optimize Forescout Secure Connector configuration by adjusting settings such as scan intervals, data collection frequency, and logging levels. Experiment with different settings to find the optimal balance between performance and data collection.
- Consider upgrading Forescout Secure Connector to the latest version to benefit from performance enhancements and bug fixes.
- If performance issues persist, contact Forescout support for further assistance.
Forescout Secure Connector stands as a silent sentinel, safeguarding your network from unseen threats. Its ability to identify and control devices, combined with its seamless integration with other security tools, makes it a crucial asset in any modern security arsenal. By implementing Forescout Secure Connector, you can create a more secure and resilient network environment, confident that your data and systems are protected from malicious actors.
FAQ Resource
How does Forescout Secure Connector identify devices?
Forescout Secure Connector utilizes various methods to identify devices, including MAC address, IP address, and device type. It also uses network protocols like DHCP and DNS to gather information about devices on the network.
What types of devices can Forescout Secure Connector manage?
Forescout Secure Connector can manage a wide range of devices, including computers, laptops, servers, printers, mobile devices, and IoT devices.
Is Forescout Secure Connector compatible with my existing security tools?
Forescout Secure Connector is designed to integrate with various security tools, including SIEM, EDR, and firewalls. It offers a robust API and various integration options to enhance your overall security infrastructure.
What are some common use cases for Forescout Secure Connector?
Forescout Secure Connector is used in various scenarios, including:
- Enforcing device compliance with security policies
- Detecting and isolating rogue devices
- Preventing unauthorized access to sensitive data
- Improving network visibility and control
- Responding to security incidents more effectively






