Who is responsible for decisions about security strategy – Who’s Calling the Shots on Security Strategy? It’s a question that keeps security experts up at night, especially in today’s digital Wild West. From Hollywood blockbusters to real-life cyberattacks, the stakes are higher than ever. But who’s actually in charge of protecting our data and systems? Is it the tech wizards in the basement, the boardroom suits, or some shadowy government agency?
Let’s dive into the fascinating world of security strategy and uncover who’s pulling the strings.
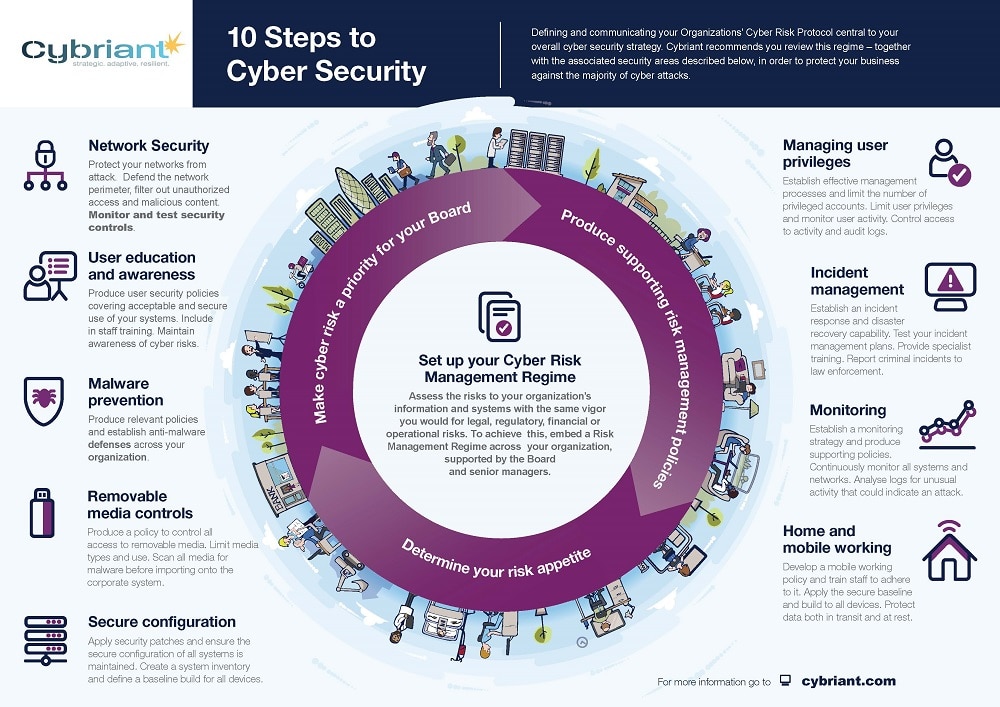
Security strategy isn’t just about firewalls and passwords; it’s about making tough decisions that balance risk and reward. It’s about understanding the vulnerabilities, identifying threats, and putting in place the right safeguards to keep our digital lives safe. This involves a diverse cast of characters, each playing a critical role in this ongoing cybersecurity drama. From the top executives who set the stage to the security professionals who man the front lines, everyone has a part to play in this high-stakes game.
The Role of Leadership
Leadership plays a pivotal role in defining and executing a successful security strategy. Top-level executives are ultimately responsible for setting the overall security vision, allocating resources, and ensuring that security is prioritized across the organization.
Setting the Security Vision and Priorities
Leadership establishes the security vision by outlining the organization’s goals, objectives, and risk tolerance regarding information security. This vision serves as a guiding principle for all security-related decisions and activities. Leadership also sets priorities, determining which security threats and vulnerabilities pose the greatest risk to the organization and allocating resources accordingly. For example, a financial institution might prioritize protecting customer data and financial transactions, while a healthcare organization might focus on safeguarding patient health information.
Communicating the Importance of Security
Effective leadership communicates the importance of security to the entire organization. This involves:
- Regularly communicating security risks and threats to employees at all levels, emphasizing the potential consequences of security breaches.
- Promoting a culture of security awareness by encouraging employees to report suspicious activities and follow security best practices.
- Recognizing and rewarding employees who demonstrate strong security practices and contribute to the organization’s security posture.
By effectively communicating the importance of security, leadership can foster a culture of security awareness and accountability throughout the organization.
Security Teams and Their Responsibilities
Security teams are crucial in safeguarding an organization’s assets, including its data, systems, and infrastructure. They are responsible for developing, implementing, and monitoring security strategies that mitigate risks and ensure the organization’s resilience against cyber threats.
Roles of Security Professionals, Who is responsible for decisions about security strategy
Security teams are comprised of professionals with diverse skillsets and expertise, each contributing to the overall security posture of the organization. These roles are often specialized and work in conjunction to address various security challenges.
- Security Analyst: These professionals are responsible for monitoring security systems, analyzing security events, and responding to incidents. They are often the first line of defense against cyberattacks and play a critical role in incident response.
- Security Architect: Security architects design and implement secure systems and architectures. They are responsible for ensuring that security is built into the organization’s infrastructure from the ground up.
- Security Engineer: Security engineers are responsible for implementing and maintaining security controls. They may work with a variety of technologies, such as firewalls, intrusion detection systems, and antivirus software.
- Penetration Tester: Penetration testers are responsible for simulating real-world attacks to identify vulnerabilities in an organization’s systems. Their findings help organizations improve their security posture by addressing weaknesses before malicious actors exploit them.
- Security Manager: Security managers are responsible for overseeing the organization’s security program. They develop and implement security policies, procedures, and standards.
- Chief Information Security Officer (CISO): The CISO is responsible for the overall security of the organization. They are responsible for setting the security strategy, managing the security budget, and reporting to senior management on security risks.
Collaboration with Other Departments
Effective security relies on collaboration between security teams and other departments within the organization. This collaboration ensures that security considerations are integrated into all aspects of the organization’s operations.
- IT Department: Security teams work closely with the IT department to ensure that security controls are implemented and maintained effectively. This collaboration is crucial for ensuring that security measures are aligned with the organization’s IT infrastructure and operations.
- Legal Department: Security teams collaborate with the legal department to ensure compliance with relevant laws and regulations. This includes data privacy laws, such as the General Data Protection Regulation (GDPR), and cybersecurity regulations, such as the California Consumer Privacy Act (CCPA).
- Human Resources Department: Security teams work with the human resources department to develop and implement security awareness training programs for employees. This training is essential for educating employees about security threats and best practices for protecting sensitive information.
The Importance of Risk Assessment
A comprehensive risk assessment is a cornerstone of any effective security strategy. It provides a structured framework for identifying, analyzing, and prioritizing potential threats and vulnerabilities, ultimately informing the development of appropriate mitigation strategies. This process helps organizations make informed decisions regarding resource allocation and security investments, ensuring that they are addressing the most critical risks effectively.
Factors Considered in Risk Assessment
A thorough risk assessment considers a wide range of factors to gain a comprehensive understanding of an organization’s security posture. These factors can be categorized as follows:
- Assets: Identifying the organization’s critical assets, including physical infrastructure, data, systems, and intellectual property, is essential. This involves determining the value and sensitivity of each asset and its potential impact if compromised.
- Threats: Organizations must identify potential threats that could target their assets. This includes both internal and external threats, such as malicious actors, natural disasters, and human error. Understanding the motivations, capabilities, and tactics of potential attackers is crucial.
- Vulnerabilities: A vulnerability is a weakness in an asset or system that could be exploited by a threat. Identifying vulnerabilities involves examining the security controls in place, the configuration of systems, and the potential weaknesses in processes.
- Likelihood: The likelihood of a threat exploiting a vulnerability to compromise an asset is a critical factor in risk assessment. This involves analyzing historical data, industry trends, and threat intelligence to estimate the probability of a threat materializing.
- Impact: The impact of a successful attack on an asset is measured in terms of financial, operational, reputational, and legal consequences. A thorough assessment of potential impacts helps prioritize risks and allocate resources accordingly.
Prioritizing Risks and Mitigation Strategies
Once risks have been identified and assessed, they must be prioritized based on their likelihood and impact. This involves creating a risk matrix that maps the severity of each risk, allowing organizations to focus their efforts on the most critical threats.
- Risk Matrix: A risk matrix typically uses a two-dimensional grid with likelihood on one axis and impact on the other. Risks are plotted within the matrix based on their corresponding values, providing a visual representation of their relative severity.
- Mitigation Strategies: Once risks have been prioritized, appropriate mitigation strategies are developed. These strategies aim to reduce the likelihood or impact of the identified risks. Examples include implementing stronger security controls, enhancing awareness training, and developing incident response plans.
Examples of Risk Assessment Informing Security Decisions
- Data Breach Prevention: A risk assessment might reveal that a company’s customer data is highly vulnerable to a data breach due to weak password policies. The assessment would then prioritize this risk, leading to the implementation of stronger password requirements and multi-factor authentication to reduce the likelihood of unauthorized access.
- Cybersecurity Investments: Organizations can use risk assessments to justify investments in cybersecurity solutions. For example, if an assessment reveals a high likelihood of a ransomware attack, the organization might invest in advanced endpoint protection and data backup solutions to mitigate this risk.
- Incident Response Planning: Risk assessments can help organizations develop effective incident response plans. By understanding the potential impact of various threats, organizations can create detailed plans to respond to incidents promptly and effectively, minimizing damage and recovery time.
Stakeholder Involvement and Collaboration: Who Is Responsible For Decisions About Security Strategy

A robust security strategy is not solely the responsibility of a dedicated security team. It requires a collaborative approach that encompasses input and participation from various stakeholders within an organization. This ensures that the security strategy aligns with the organization’s overall objectives and addresses the specific needs and concerns of different groups.
The Importance of Stakeholder Involvement
Engaging stakeholders in the security strategy development process offers numerous benefits, including:
- Enhanced Awareness and Understanding: By involving stakeholders, organizations can foster a shared understanding of security risks and the importance of implementing security measures. This helps to cultivate a security-conscious culture where everyone understands their role in safeguarding sensitive information.
- Improved Alignment with Business Objectives: Stakeholder involvement ensures that the security strategy is aligned with the organization’s strategic goals and priorities. This prevents security measures from becoming an isolated initiative and instead integrates them seamlessly into the overall business operations.
- Increased Acceptance and Buy-in: When stakeholders are involved in the decision-making process, they are more likely to support and embrace the security strategy. This reduces resistance to change and promotes a more proactive approach to security.
- Identification of Critical Security Needs: Stakeholders from different departments and roles can bring unique perspectives and insights into the security risks and vulnerabilities specific to their areas of expertise. This helps to identify critical security needs that may be overlooked in a more isolated approach.
The Roles of Different Stakeholders
Different stakeholders play distinct roles in shaping and implementing a comprehensive security strategy. Here’s a breakdown of their contributions:
- Employees: Employees are often the first line of defense against security threats. Their role involves adhering to security policies, reporting suspicious activities, and participating in security awareness training. Engaging employees in the security strategy development process helps to ensure that the policies and procedures are practical, understandable, and acceptable from their perspective.
- Customers: Customers are increasingly concerned about the security of their personal data. Organizations need to involve customers in discussions about data privacy and security practices to build trust and confidence. This can include obtaining consent for data collection and use, providing clear and concise information about security measures, and offering options for managing privacy settings.
- Business Partners: Organizations often rely on business partners for various services, such as data storage, software development, or IT support. Collaborating with business partners on security matters is crucial to ensure that their practices align with the organization’s security standards. This can involve conducting security audits of partner organizations, sharing security best practices, and establishing clear security protocols for data exchange.
- Regulatory Bodies: Organizations operating in regulated industries must comply with relevant security regulations and standards. Engaging with regulatory bodies can provide valuable insights into compliance requirements and best practices. This can help to ensure that the security strategy meets legal and regulatory obligations.
Examples of Stakeholder Collaboration
Numerous examples demonstrate the positive impact of stakeholder collaboration on security outcomes.
- Security Awareness Training: Organizations can involve employees in the design and delivery of security awareness training. This allows employees to contribute their insights and perspectives, making the training more relevant and engaging. For example, a company could involve employees in creating mock phishing scenarios based on their own experiences with phishing emails, leading to a more effective and relatable training program.
- Data Privacy Policies: Involving customers in the development of data privacy policies can ensure that the policies are clear, understandable, and address customer concerns. This can include providing customers with options for managing their data privacy settings, such as opting out of certain types of data collection or receiving notifications about data breaches.
- Security Audits: Organizations can collaborate with business partners to conduct joint security audits. This allows both parties to assess their security practices and identify potential vulnerabilities. For instance, a software development company could work with its clients to conduct a joint audit of the development process, ensuring that security considerations are integrated into the software development lifecycle.
Compliance and Regulatory Requirements
Compliance with relevant security regulations and standards is a crucial aspect of any effective security strategy. Organizations must understand and adhere to these requirements to protect sensitive data, ensure operational continuity, and maintain public trust.
Identifying Relevant Security Regulations and Standards
Understanding the applicable regulations and standards is the first step in ensuring compliance. These requirements vary based on industry, location, and the type of data handled. Some of the most common security regulations and standards include:
- General Data Protection Regulation (GDPR): This regulation, applicable in the European Union, focuses on protecting the personal data of individuals. Organizations must implement measures to ensure data privacy, security, and transparency.
- California Consumer Privacy Act (CCPA): Similar to GDPR, the CCPA provides California residents with rights regarding their personal data. Organizations handling the data of California residents must comply with the CCPA’s requirements.
- Payment Card Industry Data Security Standard (PCI DSS): This standard applies to organizations that process, store, or transmit credit card data. It Artikels specific security requirements to protect cardholder data from unauthorized access, use, or disclosure.
- Health Insurance Portability and Accountability Act (HIPAA): This act governs the protection of protected health information (PHI) in the healthcare industry. Organizations must comply with HIPAA’s security and privacy rules to safeguard patient data.
- ISO 27001: This international standard provides a framework for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). It offers guidance on managing risks and protecting sensitive information.
Ensuring Compliance with Regulations
Organizations must establish a comprehensive compliance program to meet the requirements of relevant regulations and standards. This program should include the following steps:
- Risk Assessment: Identify and assess the risks associated with data breaches and security vulnerabilities. This assessment should consider the specific regulations and standards that apply to the organization.
- Policy Development and Implementation: Develop and implement security policies, procedures, and controls that align with regulatory requirements. These policies should cover areas such as data access, encryption, incident response, and employee training.
- Monitoring and Auditing: Regularly monitor compliance with regulations and standards. Conduct internal audits to assess the effectiveness of security controls and identify any areas for improvement.
- Documentation and Reporting: Maintain comprehensive documentation of security policies, procedures, and activities. Prepare reports to demonstrate compliance with regulatory requirements.
Examples of Compliance Requirements Influencing Security Decisions
Compliance requirements can significantly influence security decisions. For example:
- Data Encryption: Regulations like GDPR and HIPAA mandate data encryption to protect sensitive information. Organizations must implement encryption solutions for data at rest and in transit to comply with these requirements.
- Access Control: Compliance regulations often require organizations to implement strong access controls to restrict unauthorized access to data. This may involve implementing multi-factor authentication, role-based access control, and regular password changes.
- Data Retention Policies: Regulations like GDPR specify data retention periods. Organizations must establish clear policies for data storage and deletion to comply with these requirements.
- Incident Response: Compliance regulations require organizations to have a comprehensive incident response plan. This plan should Artikel procedures for detecting, containing, and reporting security incidents.
Ultimately, who’s responsible for decisions about security strategy is a team effort. It’s about collaboration, communication, and a shared commitment to keeping our digital world safe. From the boardroom to the IT department, everyone needs to be on the same page to ensure we’re not caught flat-footed by the next cyberattack. So, who’s calling the shots? The answer is everyone.
It’s a collective responsibility that requires constant vigilance and a proactive approach to stay ahead of the curve. So, buckle up, because the cybersecurity landscape is constantly evolving, and we need to be ready for whatever comes next.
FAQ
What are some common security risks that organizations face?
Organizations face a wide range of security risks, including data breaches, malware attacks, phishing scams, denial-of-service attacks, and insider threats. It’s important to have a comprehensive security strategy that addresses these risks and protects against potential vulnerabilities.
How can organizations ensure their security strategy is effective?
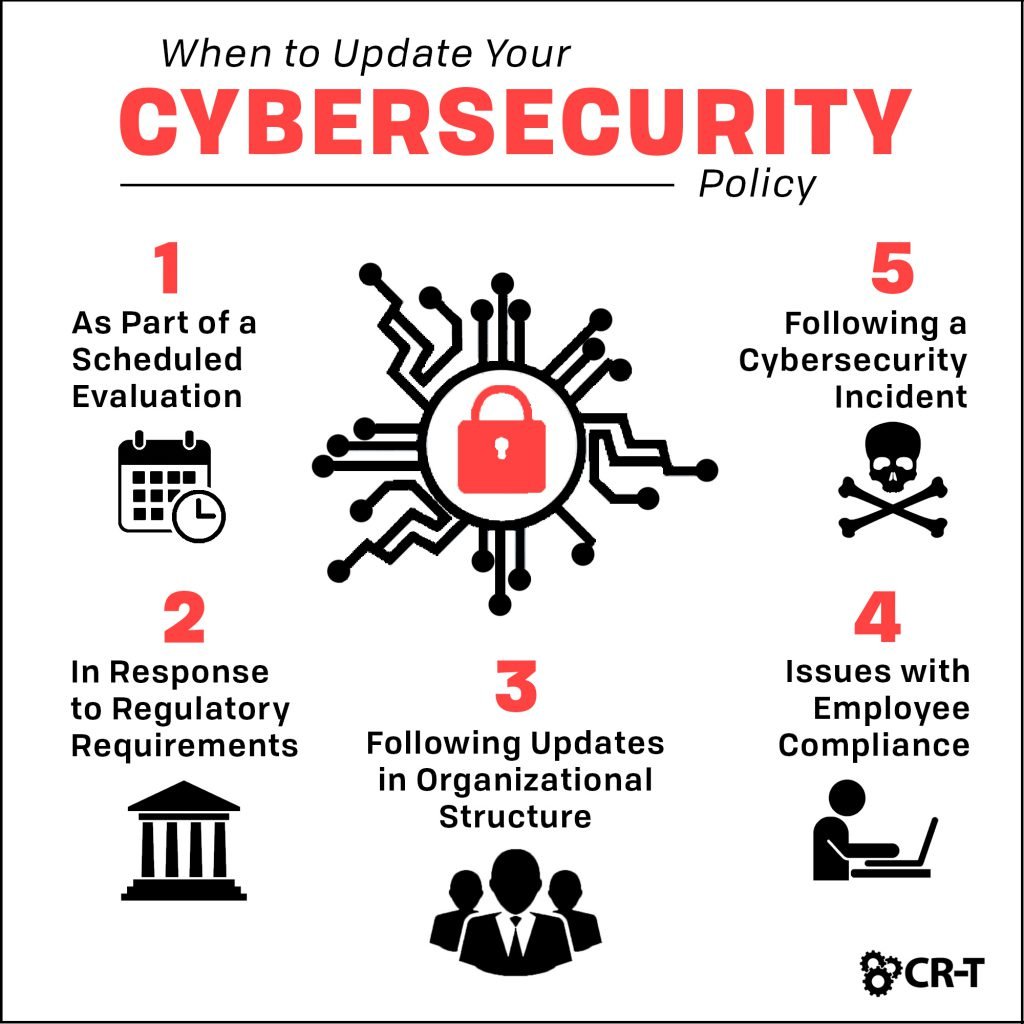
To ensure effectiveness, security strategies should be regularly reviewed and updated to reflect changing threats and vulnerabilities. Organizations should also conduct regular security assessments and penetration testing to identify weaknesses and implement appropriate safeguards.
What are some key elements of a strong security awareness program?
A strong security awareness program should include regular training for employees on topics such as phishing, social engineering, and password security. It should also provide clear guidelines on acceptable use of company resources and reporting suspicious activity.






