A security professional implements encryption, a critical process that safeguards sensitive data in the digital age. This intricate dance of algorithms and keys ensures the confidentiality and integrity of information, making it unreadable to unauthorized eyes. Imagine a world where your personal data, financial records, and confidential communications are exposed to every prying gaze. Encryption acts as an invisible shield, protecting our digital lives from the ever-present threat of cyberattacks.
From securing online transactions to safeguarding medical records, encryption plays a vital role in protecting our privacy and ensuring the integrity of our digital world. Understanding the principles behind encryption, the different techniques employed, and the security considerations involved is crucial for anyone navigating the complexities of the digital landscape.
Understanding Encryption Fundamentals

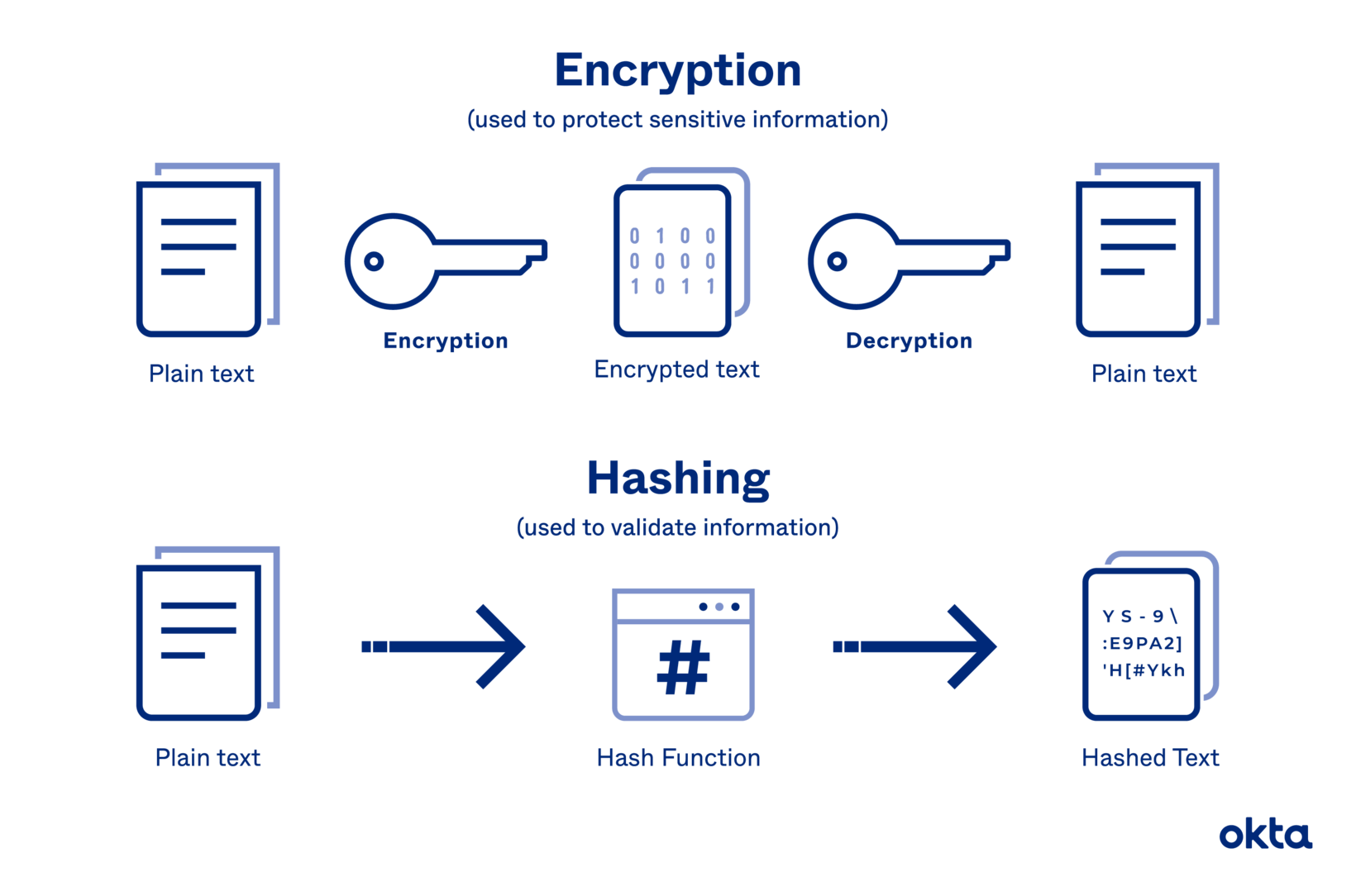
Encryption is a fundamental security practice that protects sensitive data by transforming it into an unreadable format, making it inaccessible to unauthorized individuals. This process involves converting plain text (plaintext) into an unreadable format (ciphertext) using an encryption algorithm and a secret key.
Symmetric Cryptography
Symmetric cryptography utilizes a single key for both encryption and decryption. This means the same key is used to scramble the data and unscramble it back to its original form. This approach is efficient for encrypting large amounts of data quickly, but it presents a challenge in securely sharing the key between parties.
For example, if Alice wants to send a secret message to Bob, they both need to have the same key. If the key falls into the wrong hands, the entire communication can be compromised.
Asymmetric Cryptography
Asymmetric cryptography, also known as public-key cryptography, employs two distinct keys: a public key and a private key. The public key can be shared freely, while the private key must be kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key.
For instance, Alice can generate a public-private key pair. She can share her public key with anyone who wants to send her encrypted messages. Bob can then use Alice’s public key to encrypt a message, and only Alice, with her private key, can decrypt the message.
Encryption Algorithms
Encryption algorithms are mathematical functions that define the precise steps involved in encrypting and decrypting data. These algorithms are essential for the effectiveness of encryption, ensuring that the data is transformed securely.
The strength of an encryption algorithm is measured by its resistance to attacks. A robust algorithm should be computationally difficult to break, even with significant computing power.
Key Management
Key management is the process of securely generating, storing, distributing, and managing cryptographic keys. It is crucial for maintaining the integrity and confidentiality of encrypted data. Proper key management practices help prevent unauthorized access to keys and ensure their availability when needed.
Key management involves various aspects, such as key generation, key storage, key distribution, key revocation, and key backup. Secure key management practices are essential to prevent data breaches and ensure the effectiveness of encryption.
Common Encryption Algorithms
- Advanced Encryption Standard (AES): A symmetric block cipher widely used for data encryption, including in the banking and government sectors. It is considered highly secure and efficient.
- RSA (Rivest-Shamir-Adleman): An asymmetric algorithm commonly used for digital signatures and key exchange. It relies on the difficulty of factoring large numbers.
- Elliptic Curve Cryptography (ECC): A modern asymmetric algorithm that provides comparable security to RSA with smaller key sizes, making it suitable for resource-constrained devices.
Implementing Encryption Techniques
Encryption, a cornerstone of cybersecurity, transforms data into an unreadable format, rendering it inaccessible to unauthorized individuals. This process ensures the confidentiality and integrity of sensitive information, safeguarding it from malicious actors. Implementing encryption techniques involves various methods, each tailored to specific data types and communication scenarios.
Encrypting Data at Rest
Data at rest refers to data stored on physical devices such as hard drives, servers, or databases. Encrypting data at rest is crucial for protecting sensitive information from unauthorized access, even if the physical device is compromised.
- File Encryption: This involves encrypting individual files using dedicated software or operating system features. File encryption tools employ algorithms to scramble the data, requiring a decryption key to access the original content. Popular file encryption tools include VeraCrypt, 7-Zip, and BitLocker (Windows).
- Database Encryption: Databases, repositories of structured data, can be encrypted using various techniques. Database encryption can be implemented at the field, table, or database level, ensuring the confidentiality of sensitive information stored within. Database encryption techniques include transparent data encryption (TDE), where the database management system (DBMS) handles the encryption and decryption process without requiring changes to applications, and column-level encryption, where specific columns within a table are encrypted, allowing for selective encryption of sensitive data.
Encrypting Data in Transit
Data in transit refers to data transmitted across networks, such as emails, web traffic, or file transfers. Encryption is essential to secure data in transit, protecting it from eavesdropping and interception.
- HTTPS (Hypertext Transfer Protocol Secure): HTTPS is the secure version of HTTP, the protocol used for communication on the World Wide Web. HTTPS encrypts the communication between a web browser and a web server, ensuring the confidentiality and integrity of data exchanged. This is indicated by the presence of a padlock icon in the browser’s address bar and the URL starting with “https://”.
- TLS/SSL (Transport Layer Security/Secure Sockets Layer): TLS/SSL protocols are widely used for secure communication over networks. These protocols establish an encrypted connection between two parties, ensuring the confidentiality, integrity, and authenticity of data exchanged. TLS/SSL is the foundation for HTTPS and is also used for secure email communication (SMTP/S), secure file transfer (FTPS), and other network protocols.
Digital Certificates
Digital certificates are electronic documents that bind a public key to an entity, such as a website or individual. They are essential for verifying the identity of entities participating in secure communication.
- Certificate Authority (CA): CAs are trusted organizations that issue and manage digital certificates. They verify the identity of applicants before issuing certificates, ensuring the authenticity of the public key associated with the certificate.
- Public Key Infrastructure (PKI): PKI is a framework that enables the use of digital certificates for secure communication. It includes components such as CAs, certificate management systems, and policies for certificate issuance and revocation. PKI plays a crucial role in securing communication channels by providing a mechanism for verifying the identity of entities and ensuring the integrity of data exchanged.
Security Considerations for Encryption: A Security Professional Implements Encryption
Encryption, while a powerful tool for safeguarding sensitive data, is not a foolproof solution. Effective implementation requires careful consideration of potential vulnerabilities and the adoption of robust security practices. This section explores crucial aspects of securing encryption, focusing on key management, key length, and other critical factors.
Vulnerabilities Associated with Encryption Implementation
Despite the strength of encryption algorithms, vulnerabilities can arise from improper implementation, weak key management, or the exploitation of weaknesses in the underlying systems. Understanding these potential risks is crucial for building a secure encryption strategy.
- Incorrect Algorithm Selection: Choosing an encryption algorithm that is not appropriate for the data’s sensitivity or the environment can lead to weaknesses. For example, using a weak cipher like DES for highly sensitive data could be easily compromised.
- Improper Key Management: The security of any encryption system hinges on the strength and management of its keys. Weak or compromised keys can render the entire encryption system useless. Key management practices should include secure storage, rotation, and access control.
- Side-Channel Attacks: These attacks exploit physical characteristics of the encryption process, such as timing variations or power consumption, to extract information about the key or plaintext. Countermeasures include using secure hardware and implementing countermeasures to mask side-channel leaks.
- Implementation Errors: Errors in the code or configuration of encryption libraries can create vulnerabilities. This underscores the importance of thorough testing and code reviews to ensure proper implementation.
- Cryptographic Backdoors: The inclusion of deliberate weaknesses in encryption algorithms for government access can compromise security. These backdoors can be exploited by malicious actors, undermining the overall trust in encryption.
Importance of Strong Key Management and Key Rotation Practices, A security professional implements encryption
Key management is a critical aspect of encryption security. It encompasses the processes for generating, storing, distributing, and revoking encryption keys. Robust key management practices are essential to prevent unauthorized access to keys and maintain the integrity of encrypted data.
- Secure Key Storage: Keys should be stored in a secure location, ideally in a hardware security module (HSM), which provides tamper-resistant protection. Avoid storing keys on easily accessible systems or in plain text.
- Key Rotation: Regularly rotating keys minimizes the impact of key compromise. If a key is compromised, the attacker’s access is limited to data encrypted with that specific key. Key rotation intervals should be determined based on the sensitivity of the data and the threat landscape.
- Access Control: Restricting access to keys to authorized personnel is crucial. Implement strong authentication and authorization mechanisms to control who can generate, use, or manage encryption keys.
- Key Backup and Recovery: Maintain secure backups of keys to facilitate recovery in case of system failures or accidental deletion. Backup procedures should be robust and regularly tested to ensure their effectiveness.
Impact of Key Length and Complexity on Encryption Strength
The length and complexity of encryption keys directly impact the strength of the encryption. Longer and more complex keys are harder to crack, making the encrypted data more secure.
- Key Length: The length of a key determines the number of possible combinations. Longer keys have a larger keyspace, making them exponentially harder to brute-force. For example, a 128-bit key has a keyspace of 2 128 possible combinations, while a 256-bit key has a keyspace of 2 256, making it significantly more secure.
- Key Complexity: Keys should be randomly generated and contain a mix of characters, including uppercase and lowercase letters, numbers, and symbols. Avoid using predictable patterns or personal information that could be easily guessed.
The strength of encryption is directly proportional to the length and complexity of the keys used.
Encryption Use Cases in Cybersecurity
Encryption plays a crucial role in safeguarding sensitive information in today’s digital landscape. It acts as a powerful tool for protecting data from unauthorized access, ensuring confidentiality and integrity during transmission and storage. This section explores various real-world scenarios where encryption is employed to enhance cybersecurity.
Data Breach Protection
Data breaches are a growing concern for organizations, with sensitive information often targeted by malicious actors. Encryption serves as a critical defense mechanism against data breaches by rendering stolen data useless without the decryption key. Imagine a scenario where a company’s database containing customer credit card details is compromised. If the data is encrypted, the attackers will only have access to scrambled data, making it impossible to use or sell.
This effectively prevents financial fraud and identity theft, minimizing the impact of the breach.
Secure Communications
Encryption is widely used to secure communications between devices and servers, ensuring that data remains confidential during transmission. For instance, when you access a website using HTTPS, the communication is encrypted using Transport Layer Security (TLS) protocol. This ensures that your personal information, such as login credentials and financial details, is protected from eavesdropping and interception.
Encryption Types in Cybersecurity Applications
Encryption techniques are employed in various cybersecurity applications to safeguard sensitive information. The following table provides a glimpse into the different types of encryption used in different contexts:
| Encryption Type | Application | Description |
|---|---|---|
| Symmetric-key encryption | Data storage, file encryption | Uses a single key for both encryption and decryption. This method is fast and efficient but requires secure key management. |
| Asymmetric-key encryption | Digital signatures, secure communication | Uses two keys: a public key for encryption and a private key for decryption. This approach provides non-repudiation and authentication, as only the holder of the private key can decrypt the message. |
| Hashing | Password storage, data integrity verification | Transforms data into a fixed-length hash value. This method is used to verify data integrity and store passwords securely, as it is computationally infeasible to reverse the hashing process. |
Encryption and Regulatory Compliance

Encryption has become an essential security practice in today’s data-driven world, and its importance is further amplified by the increasing prevalence of data privacy regulations. Many regulations and industry standards mandate the use of encryption to protect sensitive information, making it a critical aspect of compliance.
Regulations and Industry Standards Mandating Encryption
Data privacy regulations and industry standards emphasize the importance of encryption for protecting sensitive information. These regulations often require organizations to implement encryption measures to safeguard personal data, financial information, and other critical data.
- General Data Protection Regulation (GDPR): The GDPR, enforced in the European Union, mandates the implementation of appropriate technical and organizational measures to ensure the security of personal data, including encryption. This regulation emphasizes the importance of encryption for data at rest, data in transit, and data processing.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA, a US federal law, sets standards for protecting sensitive patient health information (PHI). It requires covered entities to implement appropriate safeguards, including encryption, to protect PHI from unauthorized access, use, or disclosure. This regulation emphasizes the importance of encryption for data at rest, data in transit, and data processing.
- Payment Card Industry Data Security Standard (PCI DSS): The PCI DSS, a set of security standards for organizations that handle credit card information, requires encryption of cardholder data during transmission and storage. This standard aims to protect cardholder data from unauthorized access and misuse.
- California Consumer Privacy Act (CCPA): The CCPA, a California law, requires businesses to implement reasonable security measures to protect personal information, including encryption. This regulation emphasizes the importance of encryption for data at rest, data in transit, and data processing.
Implications of Data Privacy Laws on Encryption Implementation
Data privacy laws have significant implications for encryption implementation. Organizations are required to implement robust encryption strategies to comply with these regulations.
- Data Minimization: Encryption is often used in conjunction with data minimization principles. Organizations should only collect and store data that is necessary for their legitimate business purposes. Encryption helps to protect this limited data set.
- Data Retention Policies: Data privacy laws often require organizations to have clear data retention policies. Encryption helps to protect data that is retained for specific purposes, such as legal or regulatory requirements.
- Data Breach Notification: Data privacy laws often require organizations to notify individuals in the event of a data breach. Encryption can help to minimize the impact of a breach by making it more difficult for attackers to access and exploit sensitive data.
Encryption’s Contribution to Compliance with GDPR and HIPAA
Encryption plays a crucial role in helping organizations comply with data privacy regulations like GDPR and HIPAA.
- GDPR: Encryption helps organizations meet the GDPR’s requirements for data security by protecting personal data from unauthorized access, use, or disclosure. This includes encrypting data at rest, data in transit, and data processing.
- HIPAA: Encryption is a critical component of HIPAA compliance, as it helps to protect sensitive patient health information (PHI) from unauthorized access, use, or disclosure. This includes encrypting PHI at rest, in transit, and during processing.
The Future of Encryption
The realm of encryption is constantly evolving, driven by advancements in technology and the ever-growing threat landscape. Emerging technologies are poised to revolutionize how we protect sensitive data, while new challenges and opportunities are arising in the face of evolving encryption methods.
Emerging Encryption Technologies
The development of new encryption technologies holds the potential to significantly enhance cybersecurity.
- Homomorphic Encryption: This advanced technique allows computations to be performed on encrypted data without decrypting it. This breakthrough has the potential to revolutionize data privacy, enabling secure data analysis and processing in cloud environments. For example, healthcare providers could analyze medical records without compromising patient privacy, or financial institutions could conduct fraud detection on encrypted data.
- Post-Quantum Cryptography: With the rise of quantum computing, existing encryption algorithms are vulnerable to attacks. Post-quantum cryptography aims to develop algorithms resistant to quantum computers, ensuring the long-term security of our digital infrastructure. Researchers are actively working on developing these algorithms, and their implementation will be crucial in safeguarding sensitive data in the future.
- Zero-Trust Encryption: This approach assumes no trust in any user or device, encrypting data at all levels. It emphasizes data protection through granular access control and strong encryption, regardless of location or network. Zero-trust encryption is particularly relevant in today’s distributed and mobile environments, where traditional security perimeters are becoming increasingly blurred.
Quantum Computing’s Impact on Encryption
Quantum computers, with their unprecedented processing power, pose a significant challenge to traditional encryption methods. These powerful machines could break current encryption algorithms, potentially compromising sensitive data. This has prompted the development of post-quantum cryptography, aiming to create algorithms resistant to quantum attacks. However, the development and deployment of quantum-resistant algorithms is a complex and ongoing process.
- Impact on Symmetric Key Cryptography: Quantum computers could break symmetric key algorithms like AES (Advanced Encryption Standard), rendering them vulnerable to attacks. This highlights the need for new algorithms that can withstand quantum attacks.
- Impact on Public Key Cryptography: Quantum computers could also break public key algorithms like RSA and ECC (Elliptic Curve Cryptography), which are widely used for digital signatures and secure communication. This emphasizes the need for quantum-resistant public key cryptography.
- Development of Quantum-Resistant Algorithms: Researchers are actively working on developing post-quantum cryptographic algorithms, aiming to provide long-term security against quantum attacks. These algorithms are based on mathematical problems that are believed to be difficult even for quantum computers to solve. Examples include lattice-based cryptography, code-based cryptography, and multivariate cryptography.
Challenges and Opportunities of Evolving Encryption Methods
The evolving landscape of encryption presents both challenges and opportunities. While new technologies offer enhanced security, they also require careful consideration and implementation.
- Complexity and Adoption: Implementing new encryption methods can be complex, requiring expertise and resources. Wide adoption is crucial to ensure widespread security, but this can be a slow process, especially for complex technologies like homomorphic encryption.
- Performance Overhead: Advanced encryption methods, such as homomorphic encryption, can introduce performance overhead, potentially impacting application performance. Striking a balance between security and performance is essential for practical implementation.
- Regulatory Compliance: Evolving encryption methods may require changes to existing regulations and standards to ensure compliance. This involves adapting legal frameworks and industry guidelines to address the use of new technologies.
- Emerging Threats: As encryption evolves, so do potential threats. It’s crucial to stay informed about emerging threats and vulnerabilities to ensure that encryption methods remain effective in protecting data.
As technology advances and cyber threats evolve, the importance of encryption only grows. By understanding the intricacies of encryption, security professionals can build robust defenses, protect sensitive information, and ensure a secure digital future. The journey into the world of encryption might seem daunting, but with a solid understanding of the fundamentals, you can become a guardian of digital security, safeguarding data and ensuring trust in the digital realm.
FAQ
What are some common encryption algorithms used in cybersecurity?
Common encryption algorithms used in cybersecurity include Advanced Encryption Standard (AES), RSA (Rivest-Shamir-Adleman), and Elliptic Curve Cryptography (ECC). Each algorithm has its strengths and weaknesses, and the choice depends on the specific security needs of the application.
How does encryption work in practice?
Encryption involves transforming plaintext data into an unreadable format called ciphertext using a specific algorithm and a key. The key is used to decrypt the ciphertext back into readable plaintext. The strength of the encryption depends on the complexity of the algorithm and the length and randomness of the key.
What are the benefits of using encryption?
Encryption offers several benefits, including confidentiality (protecting data from unauthorized access), integrity (ensuring data hasn’t been tampered with), and non-repudiation (proving the origin and authenticity of data). It plays a crucial role in securing sensitive information, protecting privacy, and maintaining trust in digital systems.






