How to enable Secure Boot without disabling CSM is a question that arises frequently for users who want to leverage the security benefits of Secure Boot while still supporting legacy hardware. Secure Boot, a feature found in modern UEFI systems, aims to prevent malicious software from loading during the boot process. However, it often conflicts with CSM (Compatibility Support Module), which is necessary for booting legacy devices using BIOS-based systems.
This delicate balance between security and compatibility presents a challenge, but navigating it effectively can unlock a more secure and functional computing environment.
This guide delves into the intricacies of Secure Boot and CSM, exploring the potential conflicts and offering practical solutions to enable Secure Boot without compromising legacy boot capabilities. We’ll examine the BIOS/UEFI settings that allow for this configuration, discuss compatibility considerations, and explore alternative approaches to address legacy boot requirements. By understanding the nuances of these technologies, users can confidently implement Secure Boot without sacrificing compatibility, thereby enhancing system security while maintaining access to essential legacy devices.
Understanding Secure Boot and CSM
Secure Boot and Compatibility Support Module (CSM) are two crucial components of the boot process in modern computer systems. Understanding their functions and potential conflicts is essential for troubleshooting boot issues and ensuring system security.
Secure Boot
Secure Boot is a security feature designed to protect your computer from malicious software by verifying the authenticity of the operating system and other critical software components before they are loaded. It works by checking the digital signature of the boot loader and other software components against a list of trusted keys stored in the system firmware. This ensures that only authorized software can be loaded and executed, preventing unauthorized modifications or attacks.
Compatibility Support Module (CSM)
The Compatibility Support Module (CSM) is a feature that allows older computers, designed for legacy BIOS systems, to boot from devices that use the newer UEFI (Unified Extensible Firmware Interface) standard. It essentially acts as a bridge between the legacy BIOS and UEFI, allowing older hardware and software to function on newer systems. CSM enables the computer to boot from devices that use older boot methods, such as MBR (Master Boot Record) partitioning and legacy BIOS boot loaders.
Potential Conflicts Between Secure Boot and CSM
Secure Boot and CSM can conflict because they rely on different boot methods and security mechanisms. Secure Boot relies on digital signatures and trusted keys to verify the authenticity of software, while CSM allows for the use of legacy boot methods that do not have the same security features. This can create vulnerabilities, as malicious software could potentially bypass Secure Boot by using CSM to load legacy boot loaders or other unauthorized software.
The primary conflict arises because CSM enables legacy boot methods, which do not employ the same rigorous security checks as Secure Boot. This opens the door for potential vulnerabilities where malicious software could exploit the lack of digital signature verification in the legacy boot process.
Enabling Secure Boot Without Disabling CSM: How To Enable Secure Boot Without Disabling Csm
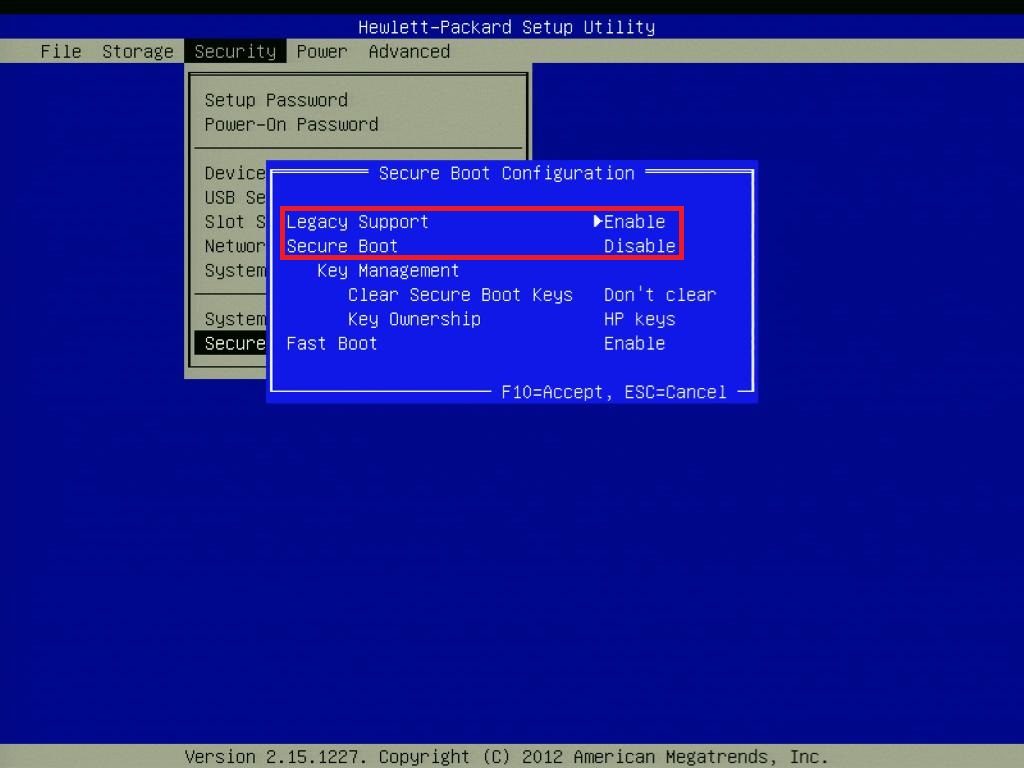
Enabling Secure Boot without disabling CSM is a valuable technique for enhancing system security while maintaining compatibility with legacy hardware. This approach allows you to leverage the benefits of Secure Boot, such as preventing unauthorized bootloaders and operating systems, without sacrificing the ability to boot from older devices that rely on the Compatibility Support Module (CSM).
BIOS/UEFI Settings
The specific BIOS/UEFI settings that enable Secure Boot without disabling CSM vary depending on the motherboard manufacturer. However, most modern BIOS/UEFI interfaces provide options for configuring Secure Boot and CSM independently. Here’s a general overview of the settings you need to look for:* Secure Boot: This setting enables or disables Secure Boot functionality. You’ll need to enable Secure Boot to utilize its security features.
CSM (Compatibility Support Module)
This setting enables or disables the Compatibility Support Module, which allows legacy devices to boot in a traditional BIOS environment.
Secure Boot Mode
Some BIOS/UEFI interfaces offer a specific setting for choosing the Secure Boot mode. Look for options like “Legacy Secure Boot” or “CSM Secure Boot,” which allow you to enable Secure Boot without disabling CSM.
Compatibility Considerations
While enabling Secure Boot without disabling CSM offers a valuable security advantage, it’s essential to consider potential compatibility issues. Here are some aspects to keep in mind:* Legacy Hardware: Older hardware, such as optical drives, may not be compatible with Secure Boot, even if CSM is enabled. In such cases, you might need to disable Secure Boot or use a different boot method.
Legacy Operating Systems
Some older operating systems might not be compatible with Secure Boot. You might need to install a compatible operating system or use a legacy boot method.
Boot Order
Ensure that your boot order is configured correctly to prioritize booting from the desired device, whether it’s a legacy or UEFI device.
Best Practices
To ensure optimal system performance and security when enabling Secure Boot without disabling CSM, follow these best practices:* Update BIOS/UEFI: Ensure that your BIOS/UEFI firmware is up-to-date. This helps improve compatibility and security features.
Check Device Compatibility
Before enabling Secure Boot, verify that your hardware and operating system are compatible.
Configure Boot Order
Carefully configure your boot order to prioritize booting from the desired device.
Test System Functionality
After enabling Secure Boot, thoroughly test your system to ensure that all hardware and software components function correctly.
Alternative Solutions for Legacy Boot
Sometimes, disabling Secure Boot isn’t the most desirable solution. Fortunately, there are alternative approaches for booting legacy devices without sacrificing the security benefits of Secure Boot. These methods allow you to run legacy operating systems while maintaining a secure boot environment.
Using Virtual Machines
Virtual machines (VMs) offer a sandboxed environment where you can run legacy operating systems without interfering with the host system’s Secure Boot settings. VMs isolate the legacy operating system from the host system, ensuring that Secure Boot remains active on the host.
- Virtualization Software: Popular virtualization software like VMware Workstation, Oracle VirtualBox, and Microsoft Hyper-V allows you to create virtual machines and install legacy operating systems within them. These virtual machines can then be configured to boot from legacy BIOS mode, even if the host system uses UEFI with Secure Boot.
- Benefits: VMs offer a safe and isolated environment for running legacy operating systems, protecting the host system from potential security vulnerabilities associated with legacy software. This allows you to maintain the integrity of your host system while still being able to use legacy applications or games.
Utilizing Emulators
Emulators provide a simulated environment that mimics the hardware and software of a legacy system, allowing you to run legacy operating systems on modern hardware. Emulators effectively create a virtual environment where the legacy operating system believes it’s running on its original hardware.
- Emulator Software: Emulators like QEMU, VirtualBox, and VMware Workstation can be used to run legacy operating systems like Windows XP, Windows 98, and various Linux distributions. These emulators can be configured to emulate the legacy BIOS and hardware, enabling legacy operating systems to boot and function.
- Compatibility: Emulators often provide better compatibility with legacy software and hardware than VMs, as they specifically focus on mimicking the legacy environment. However, some legacy applications may still experience issues due to the emulation layer.
Specialized Tools and Techniques
In some cases, specialized tools and techniques can be used to overcome compatibility challenges with legacy boot. These methods may require advanced technical knowledge and involve modifying system settings or using specific software.
- Legacy Boot Drivers: Some legacy operating systems may require specific drivers to function properly in a UEFI environment. These drivers can be obtained from the operating system vendor or third-party developers and installed on the host system to enable legacy boot.
- UEFI Bootloaders: UEFI bootloaders like Grub2 and rEFInd can be configured to load legacy operating systems, allowing them to boot even in a UEFI environment with Secure Boot enabled. However, this approach requires careful configuration and may involve modifying the boot order.
Security Implications and Considerations
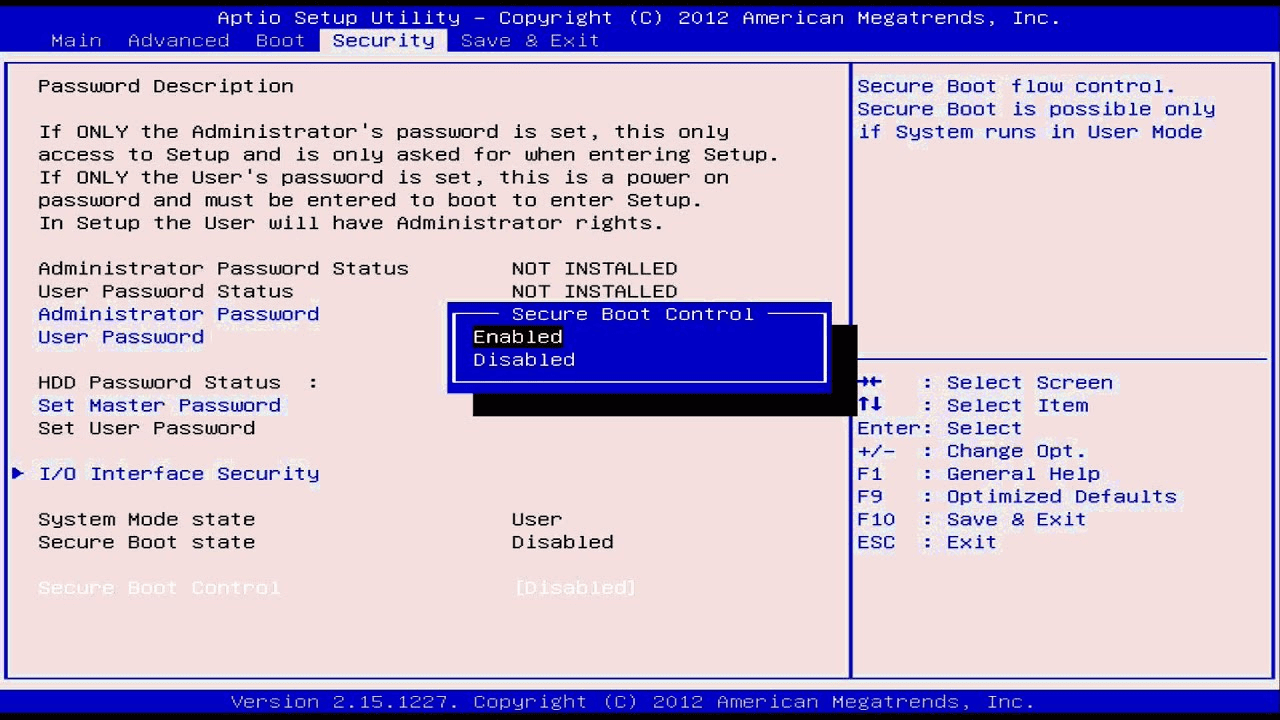
Enabling Secure Boot without disabling CSM can introduce security risks, as it creates a mixed environment where legacy and UEFI boot modes coexist. This approach might seem convenient, but it requires careful consideration to ensure a secure system.
Security Risks Associated with Enabling Secure Boot Without Disabling CSM
The coexistence of CSM and Secure Boot can lead to potential vulnerabilities.
- Reduced Effectiveness of Secure Boot: CSM allows legacy boot loaders to bypass Secure Boot’s verification process, potentially enabling the execution of unsigned or malicious code. This weakens the security provided by Secure Boot, making the system more susceptible to attacks.
- Vulnerability to Legacy Boot Exploits: CSM provides a pathway for attackers to exploit vulnerabilities in legacy boot loaders, which may have outdated security measures. These exploits could lead to malware infection, data theft, or unauthorized access to the system.
- Potential for Bootloader Hijacking: In a mixed environment, attackers could potentially manipulate the boot process by hijacking the legacy boot loader, redirecting the system to malicious boot code instead of the intended operating system.
Mitigation Strategies for Security Risks
To mitigate the security risks associated with enabling Secure Boot without disabling CSM, consider the following strategies:
- Use Secure Boot-Compatible Legacy Drivers: If you must use legacy drivers, ensure they are compatible with Secure Boot. These drivers are digitally signed and verified by Secure Boot, reducing the risk of malicious code execution.
- Disable Unnecessary Legacy Boot Options: Minimize the use of legacy boot options to reduce the attack surface. Only enable the essential legacy options required for your specific hardware or software.
- Keep Legacy Boot Loaders Updated: Regularly update your legacy boot loaders to patch security vulnerabilities. This helps protect against known exploits and reduces the risk of malicious code execution.
- Implement Strong Security Measures: In addition to Secure Boot, implement other security measures, such as a strong password policy, regular system updates, and a reliable antivirus solution, to further enhance system security.
Comparison of Security Benefits and Drawbacks
- Disabling CSM: This approach offers the highest level of security by eliminating the legacy boot environment completely. However, it may require compatibility adjustments for legacy hardware or software.
- Enabling Secure Boot Without Disabling CSM: This approach provides some level of security by verifying the UEFI boot process. However, it leaves the system vulnerable to exploits targeting the legacy boot environment.
- Not Enabling Secure Boot: This approach offers no security benefits and leaves the system open to various attacks, including boot loader hijacking, malware infection, and unauthorized access.
Case Studies and Real-World Examples
Secure boot without disabling CSM is a practical approach that addresses compatibility issues while maintaining security. Let’s delve into real-world scenarios where this method has been implemented successfully.
Successful Implementations of Secure Boot Without Disabling CSM
Real-world examples demonstrate the feasibility of secure boot without disabling CSM. This approach has proven successful in various environments, including:
- Legacy Hardware Integration: In scenarios where organizations need to integrate legacy hardware with newer systems, secure boot without disabling CSM provides a solution. For instance, a company might have older servers running critical applications that cannot be upgraded immediately. By enabling secure boot without disabling CSM, they can secure the newer systems while maintaining compatibility with the older hardware.
- Virtualized Environments: Virtualization environments often involve running different operating systems on a single physical host. Secure boot without disabling CSM enables secure booting of virtual machines while preserving compatibility with legacy operating systems or applications running on the host.
- Embedded Systems: Secure boot without disabling CSM has been successfully implemented in embedded systems, such as industrial controllers and medical devices. These systems often require compatibility with legacy firmware and drivers while maintaining security.
Addressing Compatibility Issues
This approach effectively addresses compatibility issues in specific scenarios, such as:
- Legacy Bootloaders: Some legacy operating systems and applications rely on older bootloaders that are not compatible with UEFI-only boot modes. Enabling secure boot without disabling CSM allows these systems to boot while maintaining security.
- Proprietary Drivers: Certain hardware devices might use proprietary drivers that are not signed with a trusted certificate. Secure boot without disabling CSM enables these devices to function while still providing a level of security.
- Legacy BIOS Settings: Legacy BIOS settings might be required for certain hardware configurations or specific applications. Secure boot without disabling CSM allows these settings to be preserved while maintaining security.
Challenges and Lessons Learned, How to enable secure boot without disabling csm
While effective, this approach presents certain challenges:
- Configuration Complexity: Setting up secure boot without disabling CSM can be complex, requiring careful configuration of both the BIOS and the operating system.
- Limited Support: Not all operating systems or hardware platforms fully support secure boot without disabling CSM.
- Potential Security Risks: If not properly configured, secure boot without disabling CSM could potentially expose the system to vulnerabilities.
Enabling Secure Boot without disabling CSM empowers users to enhance system security while maintaining compatibility with legacy hardware. By carefully configuring BIOS/UEFI settings and exploring alternative solutions, users can strike a balance between security and functionality. This approach not only strengthens system defenses against malicious threats but also ensures access to critical legacy devices. As technology evolves, understanding the intricacies of Secure Boot and CSM remains crucial for optimizing system performance and security, allowing users to navigate the complexities of modern computing with confidence and control.
FAQ Corner
What are the potential security risks associated with enabling Secure Boot without disabling CSM?
Enabling Secure Boot without disabling CSM might expose the system to potential vulnerabilities if the CSM is not properly configured or if legacy devices are not thoroughly vetted for security risks. It’s crucial to ensure that legacy devices are updated with the latest security patches and that CSM settings are appropriately restricted to minimize potential threats.
Can I use a virtual machine to run legacy operating systems without disabling Secure Boot?
Yes, using a virtual machine is a common solution for running legacy operating systems without disabling Secure Boot. Virtual machines provide a sandboxed environment where legacy operating systems can run without interfering with the host system’s Secure Boot configuration.
Are there any specific tools or techniques for overcoming compatibility challenges with Secure Boot and CSM?
Specialized tools and techniques, such as boot loaders designed for both UEFI and legacy environments, can help overcome compatibility challenges. Additionally, certain BIOS/UEFI settings might allow for configuring Secure Boot to accept specific legacy boot loaders, enabling a more flexible approach to compatibility.





