How to design a secure network infrastructure sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. In today’s digital age, where cyber threats are constantly evolving, securing your network is paramount. From understanding the fundamentals of network security to implementing robust access controls and data encryption, this guide will equip you with the knowledge and strategies to build a resilient and protected network infrastructure.
This guide will walk you through a step-by-step process, covering essential topics like network segmentation, secure access control, data encryption, and ongoing security monitoring. We’ll explore real-world examples and best practices to ensure your network is protected against a wide range of threats. Whether you’re a small business owner or a large enterprise, this comprehensive guide will empower you to make informed decisions and create a secure network that safeguards your data and operations.
Understanding Network Security Fundamentals
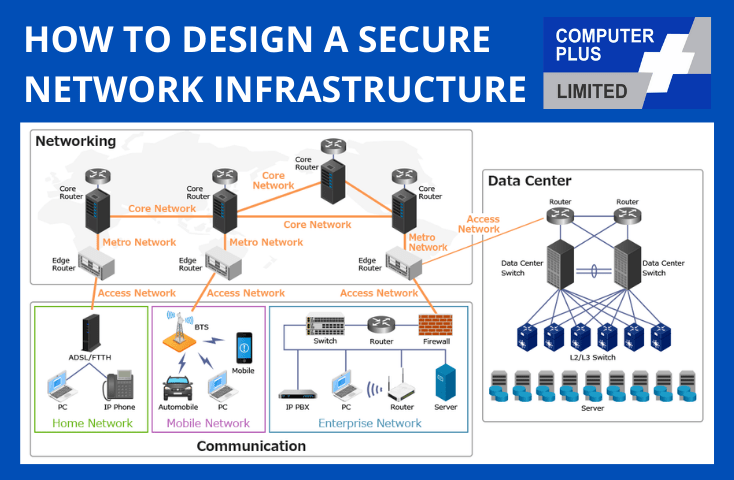
In today’s digital world, where information is constantly flowing, securing your network is crucial. A secure network infrastructure is the foundation of any organization’s digital safety and operational efficiency. It protects sensitive data, ensures smooth operations, and safeguards against potential threats.
Core Principles of Network Security
Network security is built on three core principles: confidentiality, integrity, and availability. These principles work together to ensure the safety and reliability of your network.
- Confidentiality: This principle ensures that only authorized individuals can access sensitive information. This involves implementing measures to prevent unauthorized access, such as strong passwords, encryption, and access control lists.
- Integrity: Integrity ensures that data remains accurate and unchanged during transmission and storage. This involves implementing measures to prevent data modification or corruption, such as checksums, digital signatures, and intrusion detection systems.
- Availability: Availability ensures that your network and its resources are accessible to authorized users when needed. This involves implementing measures to prevent outages and ensure network resilience, such as redundant systems, backups, and disaster recovery plans.
Common Network Security Threats and Vulnerabilities
Understanding common network security threats is crucial for implementing effective security measures. These threats can exploit vulnerabilities in your network infrastructure, leading to data breaches, system downtime, and financial losses.
- Malware: Malware is any software designed to harm or disrupt computer systems. This includes viruses, worms, trojans, and ransomware. Malware can spread through email attachments, infected websites, or malicious software downloads.
- Phishing: Phishing attacks use deceptive emails, websites, or messages to trick users into revealing sensitive information, such as passwords, credit card details, or personal data.
- Denial-of-Service (DoS) Attacks: DoS attacks aim to overload a network or server with traffic, making it unavailable to legitimate users. These attacks can disrupt critical services, causing significant downtime and financial losses.
Best Practices for Implementing Secure Network Configurations and Policies
Implementing best practices for secure network configurations and policies is essential to protect your network from threats and vulnerabilities. These practices involve a combination of technical measures and organizational policies.
- Strong Passwords and Multi-Factor Authentication: Encourage users to create strong passwords and implement multi-factor authentication for critical accounts. This adds an extra layer of security by requiring users to provide multiple forms of identification before accessing sensitive information.
- Regular Security Updates: Keep your operating systems, software, and firmware up-to-date with the latest security patches. This helps address vulnerabilities and prevents attackers from exploiting known weaknesses.
- Network Segmentation: Divide your network into smaller, isolated segments based on their security requirements. This limits the impact of a security breach by preventing attackers from spreading across the entire network.
- Firewall and Intrusion Detection Systems: Implement firewalls to control network traffic and intrusion detection systems to monitor network activity for suspicious patterns. These tools can help detect and prevent attacks before they cause significant damage.
- Data Encryption: Encrypt sensitive data at rest and in transit. This prevents unauthorized access to confidential information, even if it is intercepted by attackers.
- Regular Security Audits and Penetration Testing: Conduct regular security audits to identify vulnerabilities and implement penetration testing to simulate real-world attacks and assess your network’s security posture.
- Employee Security Awareness Training: Train employees on best practices for cybersecurity, such as recognizing phishing attempts, avoiding malicious websites, and using strong passwords.
Network Segmentation and Isolation
Network segmentation is a critical security practice that involves dividing a network into smaller, isolated segments. This approach helps to limit the impact of security breaches by preventing attackers from easily spreading across the entire network. It also enhances performance and simplifies network management.
Designing a Network Segmentation Strategy
A well-designed network segmentation strategy is essential for isolating critical systems and sensitive data. The strategy should consider the following:* Identify critical systems and sensitive data: The first step is to identify the most important systems and data within the network. This includes systems that handle sensitive financial information, customer data, or intellectual property.
Define security zones
Once critical systems and data are identified, the network should be divided into security zones based on the level of risk associated with each system. For example, a high-security zone might be used for systems that store highly sensitive data, while a lower-security zone might be used for systems that handle less sensitive data.
Implement network segmentation tools
Network segmentation can be implemented using a variety of tools, including firewalls, virtual private networks (VPNs), and network switches. These tools help to create secure boundaries between security zones, preventing unauthorized access between segments.
Using Virtual Private Networks (VPNs) and Firewalls
VPNs and firewalls are essential tools for creating secure network boundaries.* VPNs: A VPN creates a secure, encrypted connection between a user’s device and a network. This is particularly useful for remote users who need to access the network securely. VPNs can be used to segment users and devices, preventing unauthorized access to sensitive data.
Firewalls
Firewalls act as a barrier between a network and the outside world, blocking unauthorized access to the network. They can be used to create secure boundaries between security zones, preventing unauthorized communication between segments.
Implementing a Zero-Trust Security Model
The zero-trust security model assumes that no user or device can be trusted by default. This approach requires all users and devices to be authenticated and authorized before they can access resources on the network.* Benefits of a zero-trust model:
Improved security
By assuming that no user or device can be trusted, the zero-trust model helps to prevent unauthorized access to sensitive data.
Enhanced compliance
The zero-trust model can help organizations meet compliance requirements by providing a more secure environment for sensitive data.
Reduced risk of data breaches
By implementing a zero-trust model, organizations can reduce the risk of data breaches by preventing attackers from gaining access to sensitive data.
Secure Network Access Control
Securing network access is crucial for protecting sensitive data and systems from unauthorized access. Network access control encompasses various security measures to authenticate users, control access to network resources, and monitor network activity.
Multi-Factor Authentication Methods
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication. Here are some common MFA methods:
- Something you know: This factor typically involves a password or PIN that only the user knows.
- Something you have: This factor involves a physical token, such as a security key or a mobile device, that the user possesses.
- Something you are: This factor involves biometric authentication, such as fingerprint scanning or facial recognition, which verifies the user’s identity based on unique biological traits.
Access Control Lists and Network Intrusion Detection Systems
Access control lists (ACLs) and network intrusion detection systems (NIDS) play vital roles in managing network access.
- Access Control Lists (ACLs): ACLs are sets of rules that define which users or devices are allowed to access specific network resources. These rules can be based on factors such as IP address, port number, or protocol. ACLs can be implemented at various network layers, including the network layer (Layer 3) and the transport layer (Layer 4).
- Network Intrusion Detection Systems (NIDS): NIDS are software or hardware systems that monitor network traffic for suspicious activity. They analyze network packets and compare them against a database of known attack patterns. If a NIDS detects a potential threat, it can generate an alert to security personnel or take actions such as blocking the malicious traffic.
Secure Remote Access Solutions
Remote access solutions allow employees to access company resources from outside the office network. Securing remote access is essential for protecting sensitive data and systems from unauthorized access.
- Virtual Private Network (VPN): VPNs create a secure, encrypted tunnel between a user’s device and the company network. This tunnel encrypts all data transmitted between the user and the company, making it difficult for attackers to intercept or eavesdrop on the traffic.
- Remote Desktop Protocol (RDP): RDP allows users to remotely control a computer running a Windows operating system. RDP can be secured by using strong passwords, enabling MFA, and configuring appropriate security settings on the remote computer.
- Cloud-Based Access Control: Cloud-based access control solutions provide centralized management of user access to cloud-based resources. These solutions can enforce strong authentication policies, monitor user activity, and provide granular control over access permissions.
Data Encryption and Security
Data encryption is a crucial component of securing network infrastructure. It involves transforming data into an unreadable format, preventing unauthorized access and ensuring data confidentiality. Encryption plays a vital role in protecting sensitive information both while it’s being transmitted across the network (in transit) and when it’s stored on devices (at rest).
Encryption Algorithms
Encryption algorithms are mathematical functions used to transform data into an unreadable format. These algorithms are essential for securing data, and they are categorized based on their complexity, speed, and security strength. Here’s a comparison of common encryption algorithms:
- Symmetric-key algorithms, like AES (Advanced Encryption Standard), use a single key for both encryption and decryption. They are fast and efficient but require secure key management.
- Asymmetric-key algorithms, like RSA (Rivest-Shamir-Adleman), use separate keys for encryption and decryption. They are slower than symmetric-key algorithms but offer more secure key management.
- Hashing algorithms, like SHA-256 (Secure Hash Algorithm 256), generate a unique fingerprint of the data. They are used for data integrity verification and cannot be reversed.
Digital Certificates and Public Key Infrastructure (PKI)
Digital certificates and PKI play a critical role in securing communication by providing a way to verify the identity of parties involved in a transaction. Digital certificates are electronic documents that contain information about an entity, such as its name, public key, and validity period. PKI is a system that manages and distributes digital certificates and provides a framework for secure communication.
- Digital certificates are used to authenticate the identity of websites, servers, and individuals. They are issued by trusted certificate authorities (CAs) and are based on public-key cryptography. When a website uses a digital certificate, it means that the CA has verified the website’s identity, providing users with confidence that they are communicating with the legitimate website.
- PKI provides a framework for managing and distributing digital certificates, including key generation, certificate issuance, revocation, and validation. It allows for secure communication by establishing trust between parties involved in a transaction. For example, when a user connects to a website that uses a digital certificate, the browser checks the certificate’s validity and authenticity using PKI. If the certificate is valid, the browser trusts the website and establishes a secure connection.
Example: When you visit a website that uses HTTPS, the website’s digital certificate is used to establish a secure connection. The certificate verifies the website’s identity and ensures that data transmitted between your browser and the website is encrypted.
Network Security Monitoring and Response
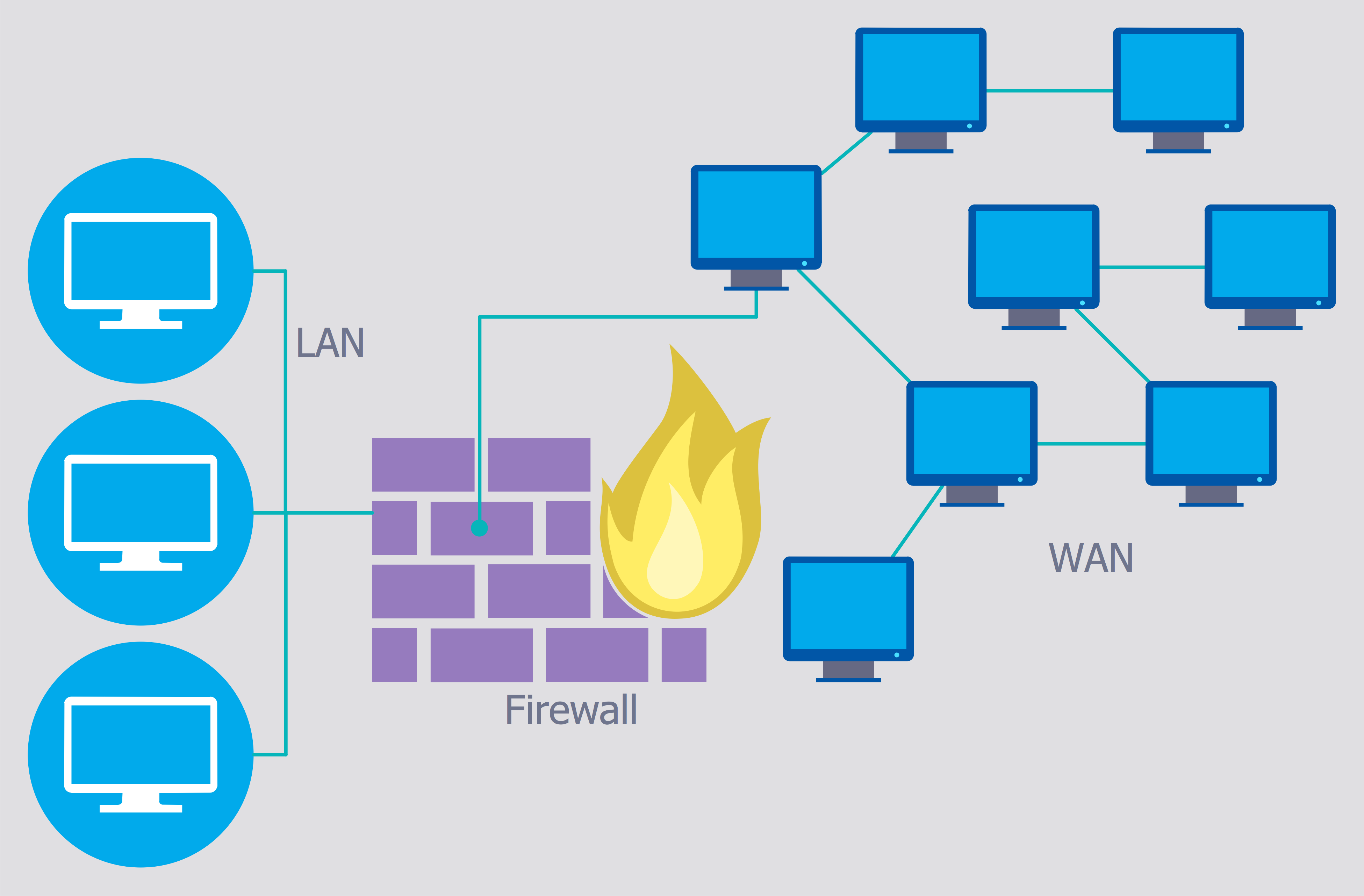
Imagine you’re running a business with a network that’s like a bustling city, full of activity. It’s important to have a system in place to monitor this activity and respond quickly if anything suspicious happens. This is where network security monitoring and response come in. It’s about having eyes and ears on your network, knowing what’s going on, and being ready to act when needed.
Key Components of a Comprehensive Network Security Monitoring System
A comprehensive network security monitoring system acts as your network’s watchdog. It involves several key components working together to ensure your network’s safety.
- Network Intrusion Detection and Prevention Systems (IDS/IPS): These are like security guards at the network’s gates, constantly looking for suspicious activity and blocking known threats. They analyze network traffic, looking for patterns that indicate malicious activity.
- Security Information and Event Management (SIEM): This is the central command center, collecting logs and security events from various sources across your network. It helps analyze these events, correlate them, and identify potential threats.
- Vulnerability Scanners: Think of these as network detectives, scanning your systems for weaknesses that attackers could exploit. They help identify vulnerabilities and prioritize patching efforts.
- Log Management Systems: These systems are like your network’s memory, storing and organizing logs from different devices and applications. They help you trace back events and identify patterns that could indicate security breaches.
- Network Traffic Analysis Tools: These tools are like network analysts, providing deep insights into network traffic patterns. They help identify unusual activity, potential threats, and performance bottlenecks.
The Importance of Security Information and Event Management (SIEM)
SIEM is like the brain of your security monitoring system, playing a crucial role in threat detection and analysis. It gathers security data from various sources, analyzes it for patterns, and helps you make informed decisions about security threats.
- Centralized Logging: SIEM collects logs from various devices and applications across your network, providing a single point of view for security monitoring.
- Real-time Threat Detection: SIEM uses advanced analytics and correlation rules to identify suspicious activity in real-time, enabling faster response to security incidents.
- Incident Response and Forensics: SIEM helps you investigate security incidents by providing detailed logs and analysis, enabling you to trace the source of the attack and understand its impact.
- Security Reporting and Auditing: SIEM provides valuable reports and insights into your network’s security posture, helping you identify vulnerabilities and areas for improvement.
Responding to Security Incidents
Responding to security incidents effectively is crucial for minimizing damage and ensuring business continuity. Here’s a step-by-step plan to guide you through the process:
- Detection and Identification: The first step is detecting the incident, identifying its nature, and understanding its scope.
- Containment: Once the incident is identified, the next step is to contain it, preventing further damage and spread. This may involve isolating affected systems or blocking malicious traffic.
- Eradication: The next step is to remove the threat, either by patching vulnerabilities, removing malware, or taking other appropriate actions.
- Recovery: After the threat is eradicated, you need to restore affected systems and data to their original state. This may involve backups or other recovery procedures.
- Lessons Learned: It’s important to analyze the incident, identify the root cause, and implement measures to prevent similar incidents in the future.
Network Security Best Practices

It’s not enough to just implement security measures. You gotta make sure you’re maintaining a solid, secure network infrastructure, man. That’s where best practices come in. Think of it like keeping your car in tip-top shape. Regular checkups, proper maintenance, and a little TLC can go a long way.
Regular Security Audits and Vulnerability Assessments
So, you’ve built a secure network, but how do you know it’s actually working? You gotta have a system to check up on it, man. Regular security audits and vulnerability assessments are like your network’s annual physical. They help identify any weaknesses or vulnerabilities in your system before they can be exploited.Think of it like this: Imagine you have a brand new car.
It’s shiny and new, but you still need to get it serviced regularly to make sure everything is running smoothly. Same goes for your network. Regular audits and assessments are like your car’s service schedule, ensuring your network stays in top shape.
- Internal Audits: These are conducted by your own team, like a self-check-up. They focus on policies, procedures, and configurations to ensure they’re aligned with your security goals.
- External Audits: This is like getting a second opinion from a professional. External auditors bring an unbiased perspective and can test your security controls from a hacker’s point of view.
- Vulnerability Assessments: These scans look for known weaknesses or vulnerabilities in your systems, like software bugs or outdated configurations. It’s like a car inspection that checks for any potential issues.
Security Awareness Training for Employees
Your employees are the first line of defense against cyber threats, man. They’re the ones interacting with your network every day. So, it’s crucial to make sure they’re aware of security risks and know how to protect themselves and your network.Security awareness training is like teaching your employees the rules of the road. It helps them understand the potential dangers and how to avoid them.
This training can include topics like:
- Phishing: This is a common attack where attackers try to trick you into giving them your login credentials or other sensitive information. Think of it like a scammer trying to get you to reveal your bank details.
- Social Engineering: This is a type of attack where attackers use psychological manipulation to trick you into doing something that compromises your security. It’s like someone trying to convince you to give them your car keys.
- Strong Password Practices: This involves creating strong passwords that are difficult to guess and not reusing the same password across multiple accounts. Think of it like using a different key for each of your locks.
- Data Security Best Practices: This covers how to handle sensitive data responsibly, like not sharing it with unauthorized individuals and encrypting it when necessary. Think of it like keeping your valuables locked up.
Secure Network Design for Specific Use Cases: How To Design A Secure Network Infrastructure
Designing a secure network infrastructure goes beyond general principles. It requires tailoring the approach to the specific needs and vulnerabilities of different organizations. This section will explore how to design secure networks for various use cases, including small businesses, large enterprises, and cloud-based environments.
Secure Network Design for a Small Business
Small businesses often have limited resources and may not have dedicated IT staff. This makes it crucial to implement a simple yet effective network security plan. Here are some key considerations:
- Strong Passwords and Multi-Factor Authentication: Encourage employees to use strong passwords and implement multi-factor authentication for critical accounts, like administrative access and cloud services. This significantly reduces the risk of unauthorized access.
- Firewall and Intrusion Detection Systems (IDS): Invest in a firewall to block unauthorized access to the network and use an IDS to detect suspicious activity. Many affordable firewall and IDS solutions are available for small businesses.
- Regular Software Updates: Ensure all devices, including computers, servers, and network equipment, are running the latest software versions to patch vulnerabilities.
- Employee Security Training: Educate employees about common security threats and best practices, such as phishing scams, malware, and social engineering. This helps prevent human error, which is a significant source of security breaches.
- Data Backup and Recovery: Implement a robust data backup and recovery plan to minimize data loss in case of a security incident or system failure.
Secure Network Design for a Large Enterprise with Multiple Locations, How to design a secure network infrastructure
Large enterprises with multiple locations face additional challenges, including managing geographically dispersed networks, ensuring data consistency, and maintaining regulatory compliance.Here are some key considerations:
- Centralized Security Management: Implement a centralized security management system to manage security policies, monitor network activity, and enforce security controls across all locations.
- Virtual Private Networks (VPNs): Securely connect remote offices and employees to the corporate network using VPNs, ensuring data confidentiality and integrity.
- Network Segmentation: Divide the network into smaller segments based on function and sensitivity of data. This limits the impact of a security breach to specific segments, preventing widespread damage.
- Security Information and Event Management (SIEM): Utilize SIEM tools to collect and analyze security events from various sources, providing real-time insights into potential threats and facilitating rapid incident response.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure compliance with industry standards and regulations.
Secure Network Design for Cloud-Based Networks
Cloud computing offers scalability and flexibility, but it also presents unique security challenges.Here are some key considerations:
- Shared Responsibility Model: Understand the shared responsibility model between the cloud provider and the organization. The cloud provider is responsible for securing the infrastructure, while the organization is responsible for securing data and applications running on the cloud.
- Data Encryption: Encrypt data at rest and in transit to protect sensitive information from unauthorized access, even if the cloud infrastructure is compromised.
- Identity and Access Management (IAM): Implement robust IAM controls to manage user access to cloud resources, ensuring only authorized personnel can access sensitive data and applications.
- Cloud Security Posture Management (CSPM): Use CSPM tools to monitor cloud security configurations and identify potential vulnerabilities, enabling proactive threat mitigation.
- Cloud Security Training: Train employees on cloud security best practices, including secure cloud storage, data protection, and identity management.
By following the principles Artikeld in this guide, you can build a secure network infrastructure that stands strong against modern cyber threats. Remember, a proactive approach to network security is essential for safeguarding your data, protecting your business, and ensuring continuity of operations. Stay informed, adapt to emerging threats, and continue to refine your security practices to ensure your network remains resilient and protected in the ever-evolving digital landscape.
Q&A
What are the most common network security threats?
Common threats include malware, phishing attacks, denial-of-service attacks, ransomware, and data breaches. Each of these poses a unique risk to your network and data.
How often should I perform security audits and vulnerability assessments?
It’s recommended to conduct regular security audits and vulnerability assessments at least annually, and more frequently if your network undergoes significant changes or you suspect a security breach.
What are the key elements of a comprehensive network security monitoring system?
A comprehensive system should include intrusion detection systems (IDS), firewalls, security information and event management (SIEM) tools, and log analysis software.
How can I design a secure network infrastructure for a remote workforce?
Use strong VPNs, implement multi-factor authentication, and enforce strict access controls for remote employees. Regular security training and awareness programs are also crucial.






